🐛Module 07: Malware Threats
Overview of Malware
With the help of a malicious application (malware), an attacker gains access to stored passwords in a computer and is able to read personal documents, delete files, display pictures, or messages on the screen, slow down computers, steal personal information, send spam, and commit fraud. Malware can perform various malicious activities that range from simple email advertising to complex identity theft and password stealing.
Programmers develop malware and use it to:
Attack browsers and track websites visited
Affect system performance, making it very slow
Cause hardware failure, rendering computers inoperable
Steal personal information, including contacts
Erase valuable information, resulting in substantial data losses
Attack additional computer systems directly from a compromised system
Spam inboxes with advertising emails
Lab 1: Gain Access to the Target System using Trojans
Overview of Trojans
In Ancient Greek mythology, the Greeks won the Trojan War with the aid of a giant wooden horse that the Greeks built to hide their soldiers. The Greeks left the horse in front of the gates of Troy. The Trojans, thinking that it was a gift from the Greeks that they had left before apparently withdrawing from the war, brought the horse into their city. At night, the hidden Greek soldiers emerged from the wooden horse and opened the city’s gates for their soldiers, who eventually destroyed the city of Troy.
Thus, taking its cue from this myth, a computer Trojan is a program in which malicious or harmful code is contained inside apparently harmless programming or data in such a way that it can gain control and cause damage such as ruining the file allocation table on your hard disk.
Task 1: Gain Control over a Victim Machine using the njRAT RAT Trojan
Attackers use Remote Access Trojans (RATs) to infect the target machine to gain administrative access. RATs help an attacker to remotely access the complete GUI and control the victim’s computer without his/her awareness. They can perform screening and camera capture, code execution, keylogging, file access, password sniffing, registry management, and other tasks. The virus infects victims via phishing attacks and drive-by downloads and propagates through infected USB keys or networked drives. It can download and execute additional malware, execute shell commands, read and write registry keys, capture screenshots, log keystrokes, and spy on webcams.
njRAT is a RAT with powerful data-stealing capabilities. In addition to logging keystrokes, it is capable of accessing a victim’s camera, stealing credentials stored in browsers, uploading and downloading files, performing process and file manipulations, and viewing the victim’s desktop.
This RAT can be used to control Botnets (networks of computers), allowing the attacker to update, uninstall, disconnect, restart, and close the RAT, and rename its campaign ID. The attacker can further create and configure the malware to spread through USB drives with the help of the Command and Control server software.
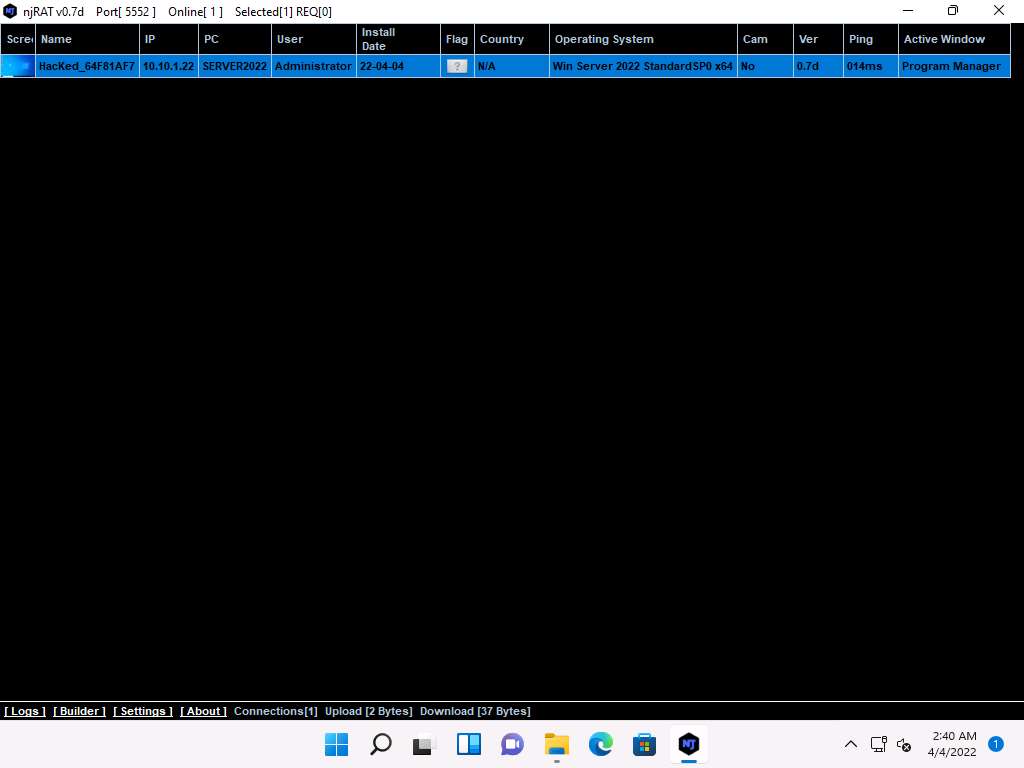
The njRAT GUI appears along with an njRAT pop-up, where you need to specify the port you want to use to interact with the victim machine. Enter the port number and click Start.
In this task, the default port number 5552 has been chosen.
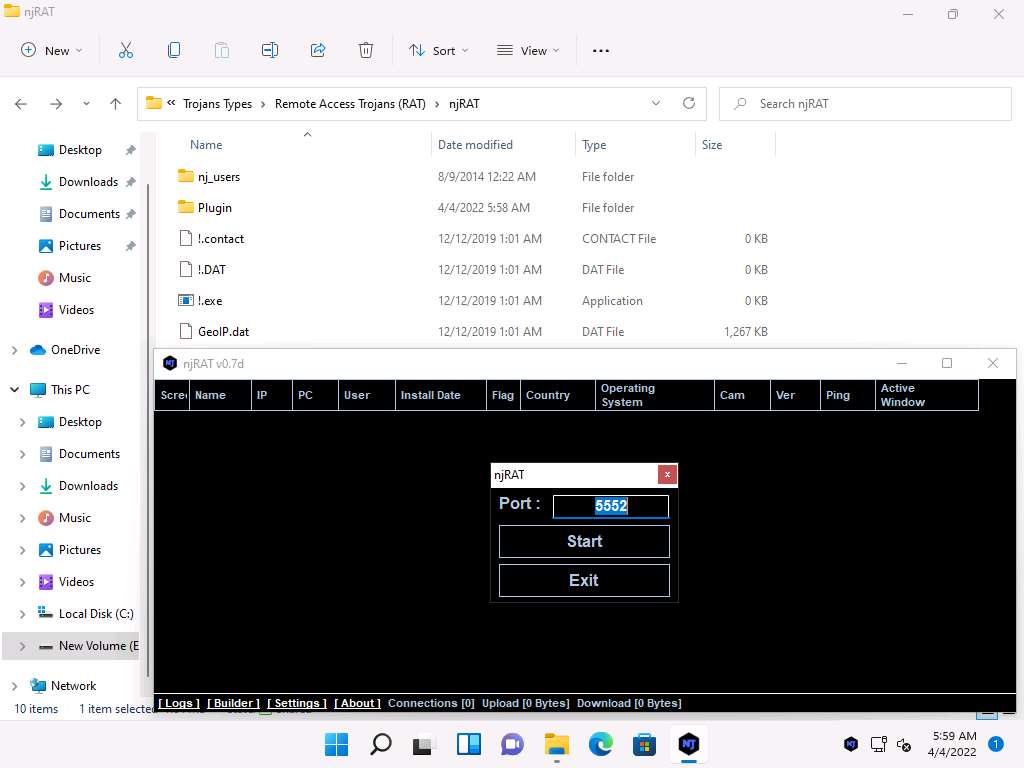
Screenshot The njRAT GUI appears; click the Builder link located in the lower-left corner of the GUI to configure the exploit details.
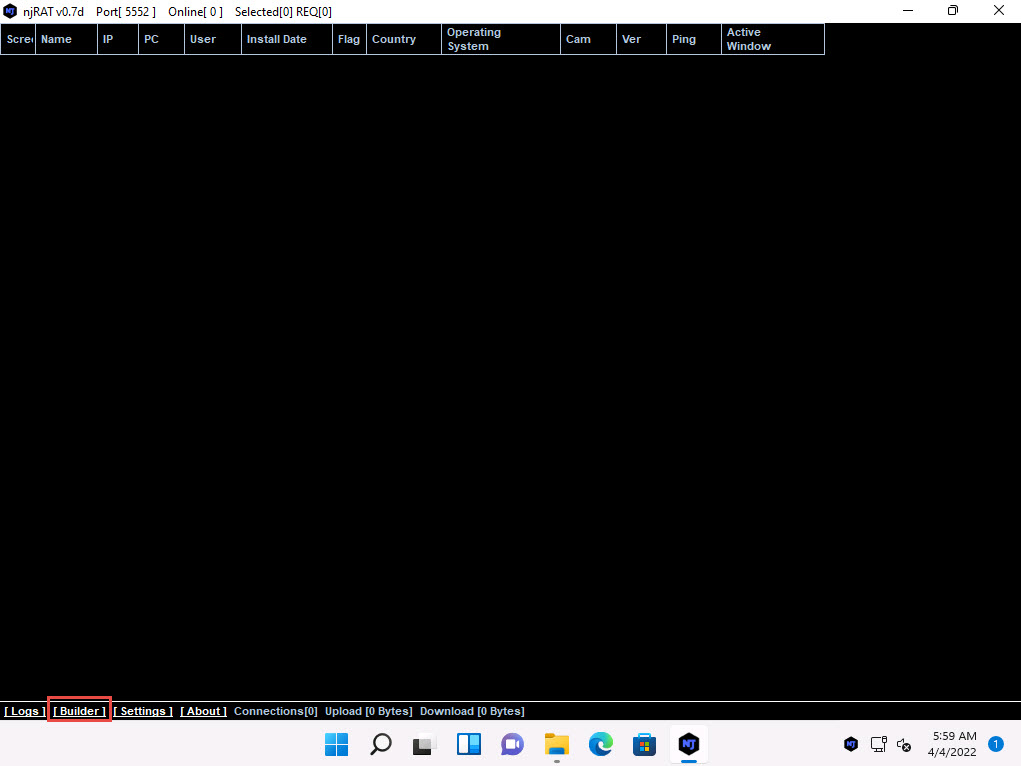
2022-04-04_14-30-07.jpg The Builder dialog-box appears; enter the IP address of the Windows 11 (attacker machine) machine in the Host field, check the option Registy StarUp, leave the other settings to default, and click Build.
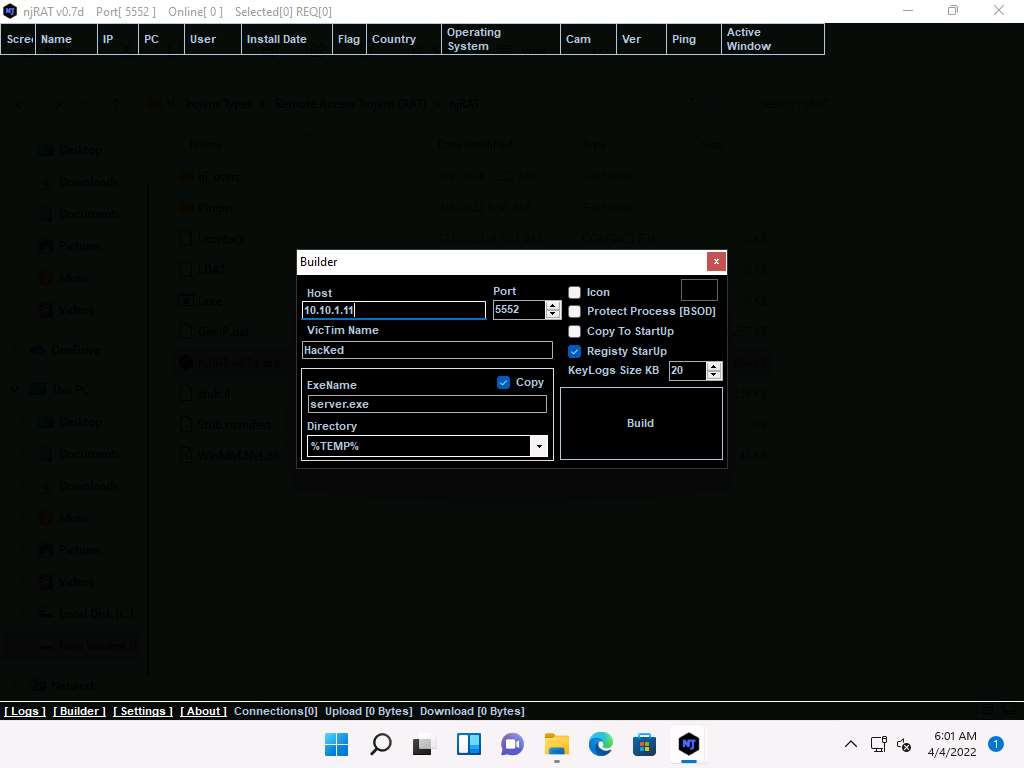
Screenshot The Save As window appears; specify a location to store the server, rename it, and click Save.
In this lab, the destination location chosen is Desktop, and the file is named Test.exe.
Screenshot Once the server is created, the DONE! pop-up appears; click OK.
Now, use any technique to send this server to the intended target through email or any other source (in real-time, attackers send this server to the victim).
In this task, we copied the Test.exe file to the shared network location (CEH-Tools) to share the file.
Screenshot Navigate to the shared network location (CEH-Tools), and then Copy and Paste the executable file (Test.exe) onto the Desktop of Windows Server 2022.
Here, you are acting both as an attacker who logs into the Windows 11 machine to create a malicious server, and as a victim who logs into the Windows Server 2022 machine and downloads the server.
Double-click the server (Test.exe) to run this malicious executable.
Screenshot Click Windows 11 to switch back to the Windows 11 machine. Maximise njRAT GUI window. As soon as the victim (here, you) double-clicks the server, the executable starts running and the njRAT client (njRAT GUI) running in Windows 11 establishes a persistent connection with the victim machine, as shown in the screenshot.
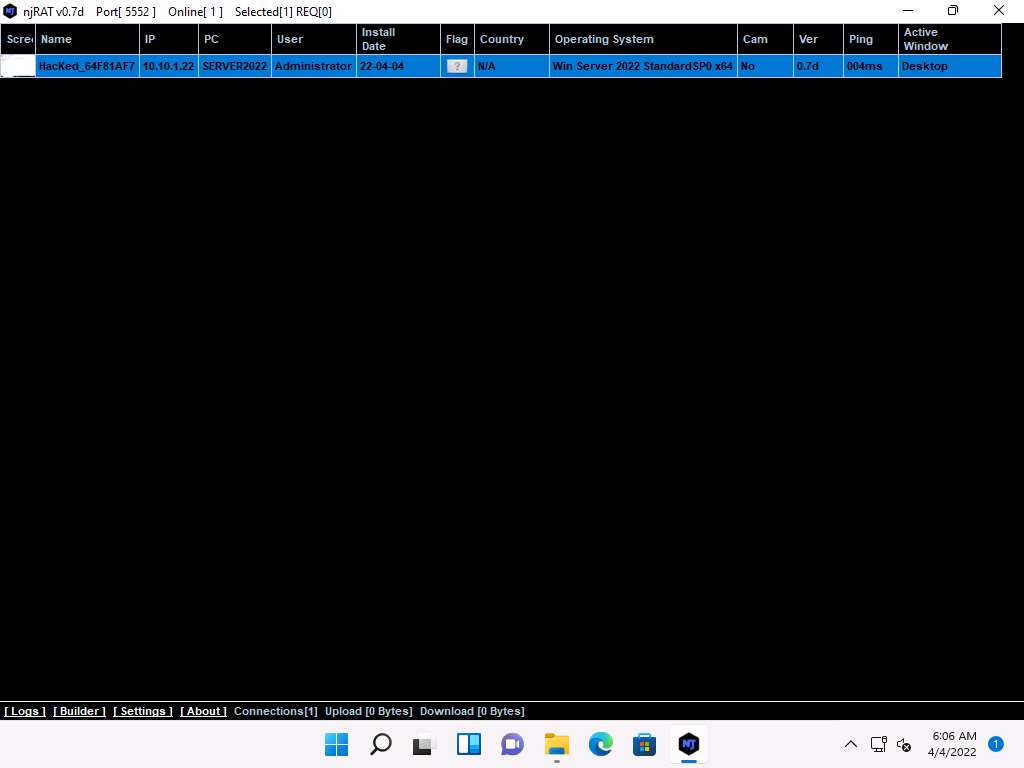
Screenshot Unless the attacker working on the Windows 11 machine disconnects the server on their own, the victim machine remains under their control.
The GUI displays the machine’s basic details such as the IP address, User name, and Type of Operating system.
Right-click on the detected victim name and click Manager.
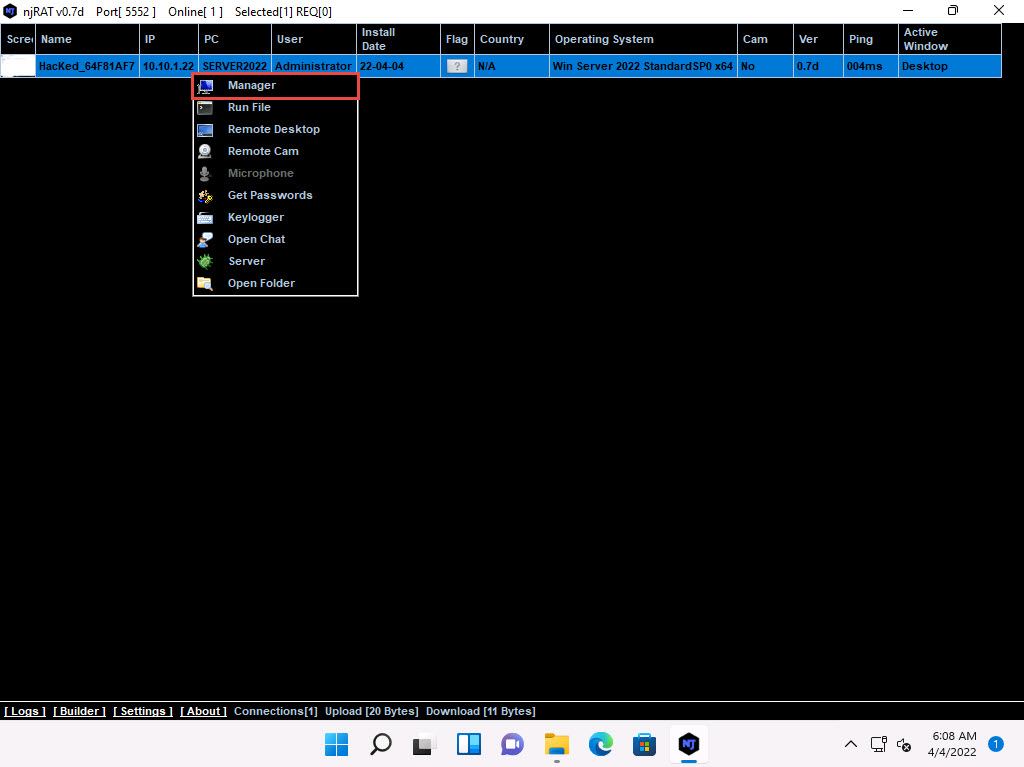
2022-04-04_14-38-23.jpg The manager window appears with File Manager selected by default.
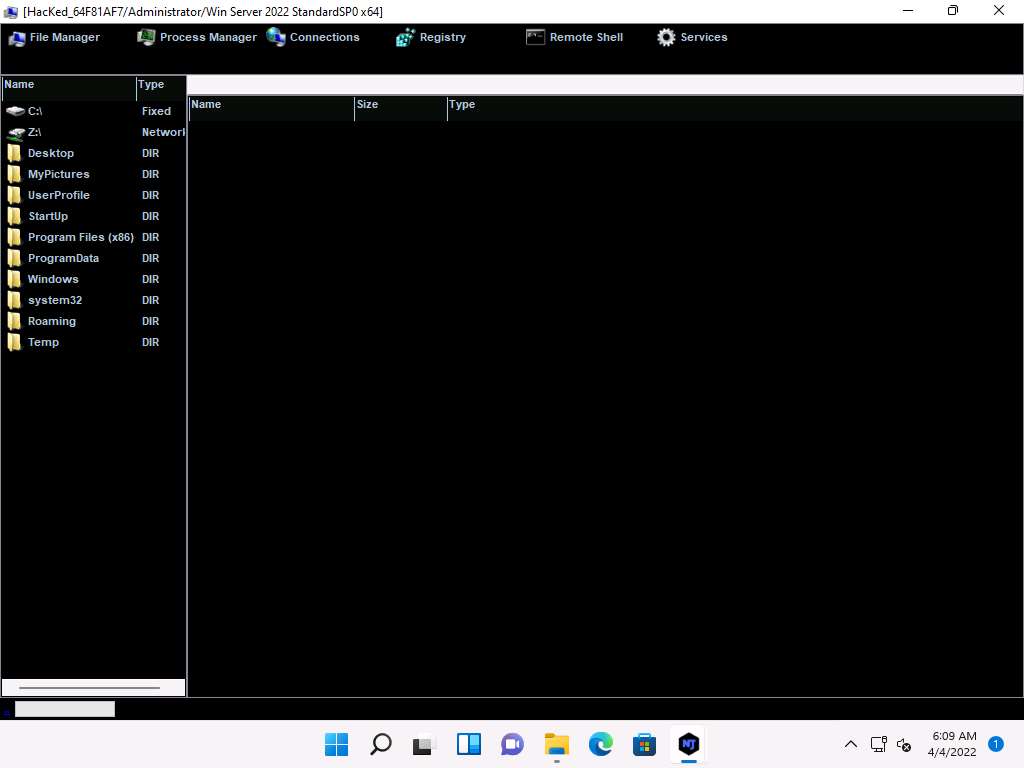
Screenshot Double-click any directory in the left pane (here, ProgramData); all its associated files and directories are displayed in the right pane. You can right-click a selected directory and manipulate it using the contextual options.
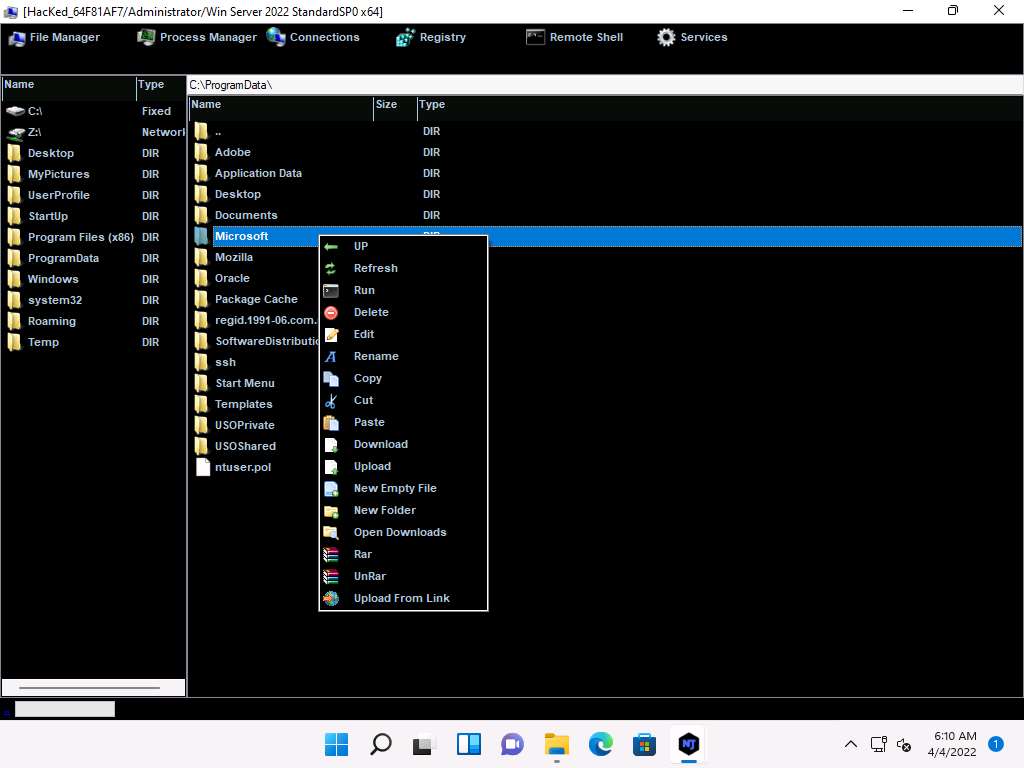
Screenshot Click on Process Manager. You will be redirected to the Process Manager, where you can right-click on a selected process and perform actions such as Kill, Delete, and Restart.
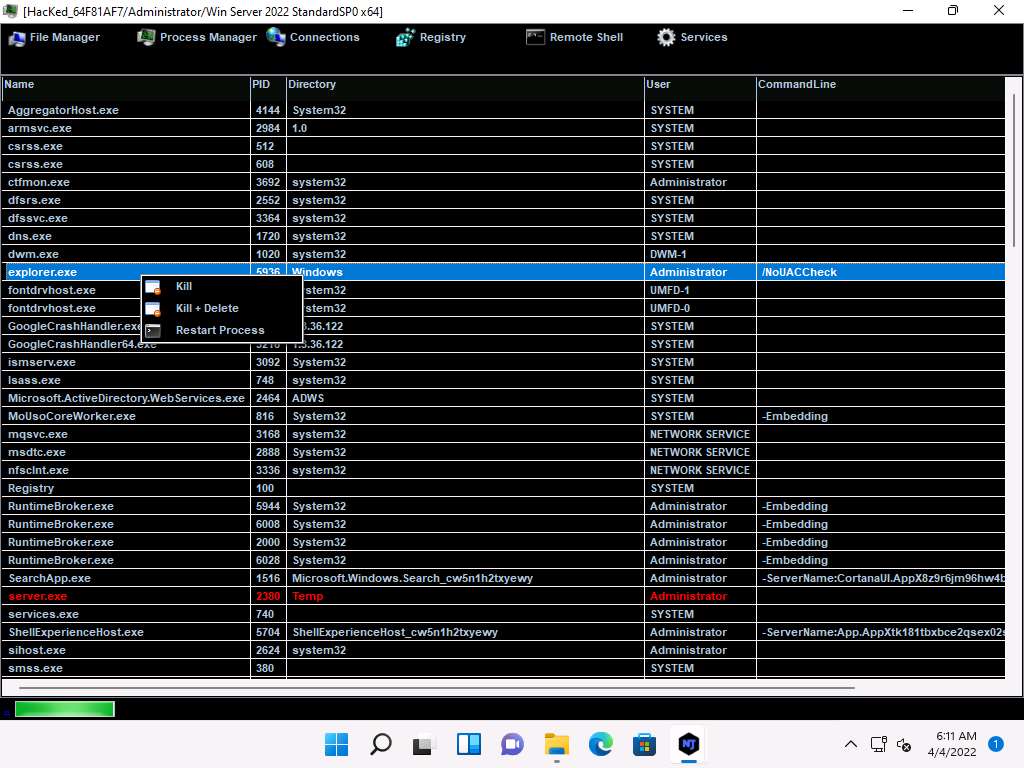
Screenshot Click on Connections, select a specific connection, right-click on it, and click Kill Connection. This kills the connection between two machines communicating through a particular port.
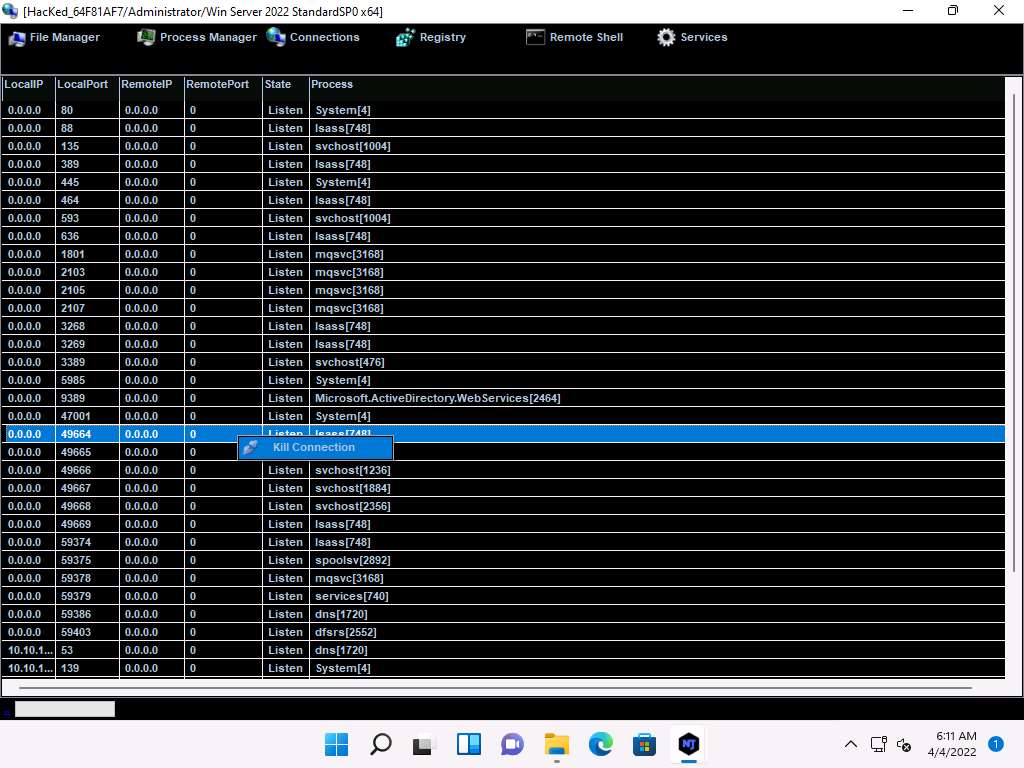
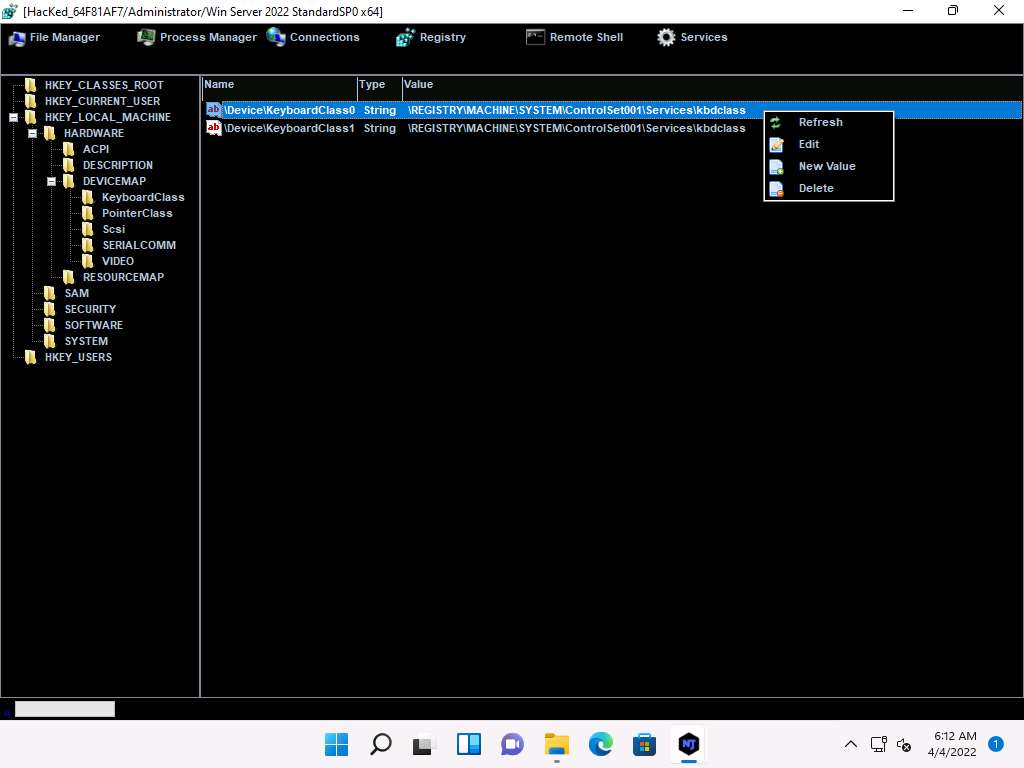
Screenshot Click on Registry, choose a registry directory from the left pane, and right-click on its associated registry files.
A few options appear for the files; you can use these to manipulate them.
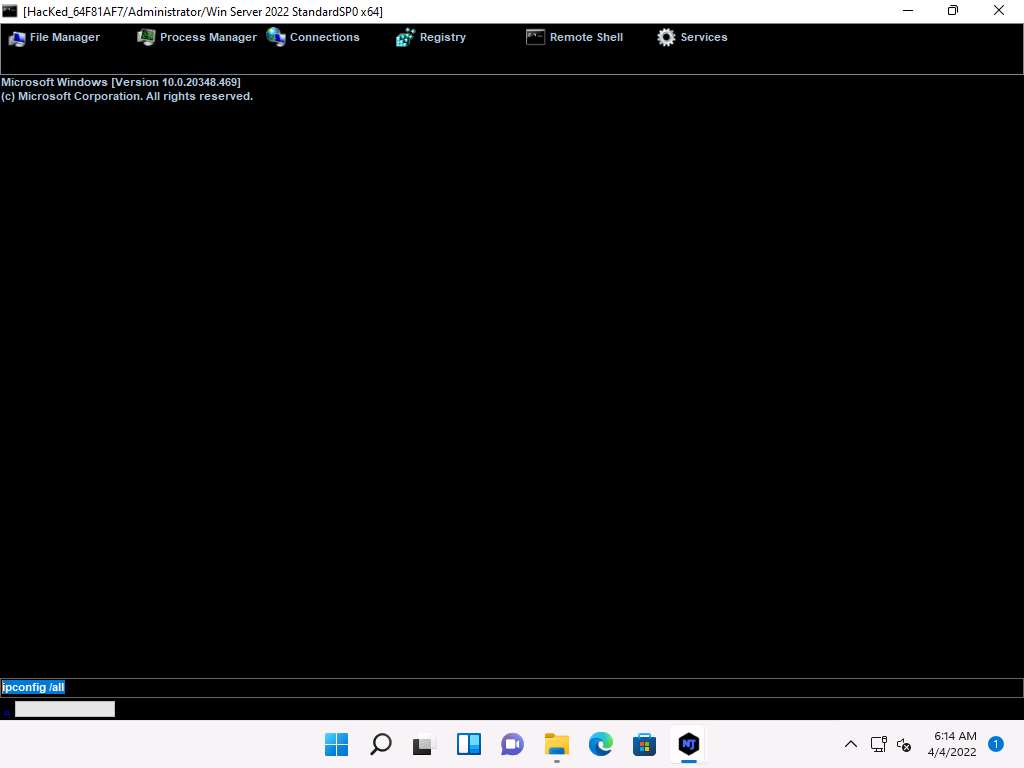
Screenshot Click Remote Shell. This launches a remote command prompt for the victim machine (Windows Server 2022).
In the text field present in the lower section of the window, type the command ipconfig/all and press Enter.
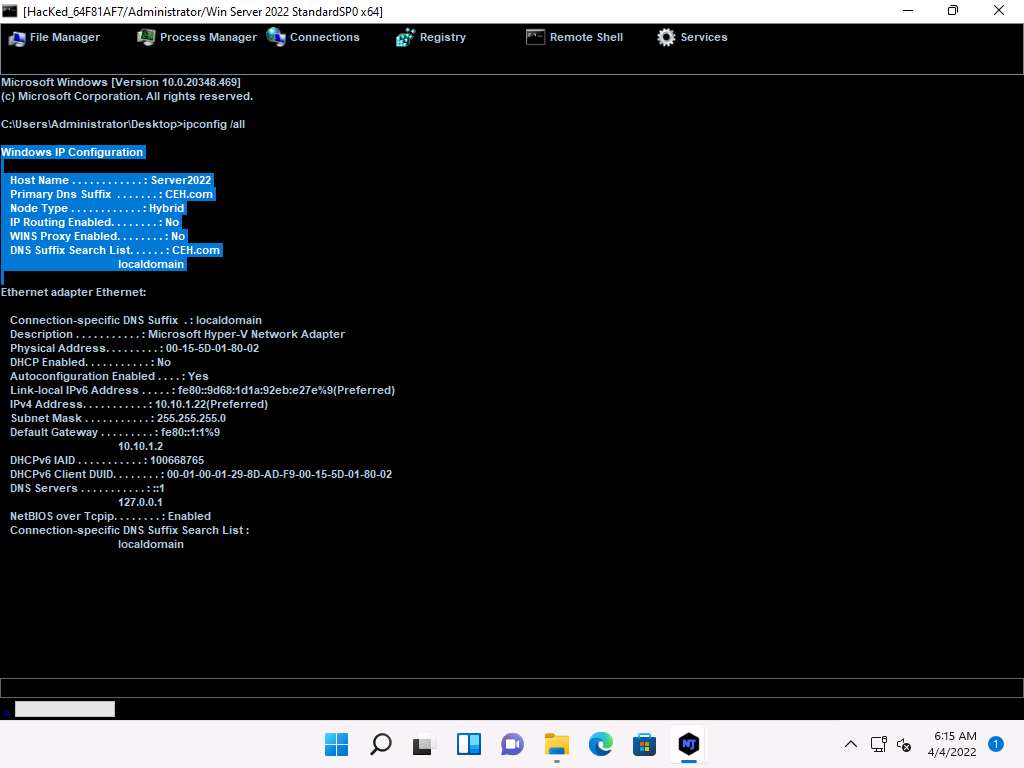
Screenshot This displays all interfaces related to the victim machine, as shown in the screenshot.
Screenshot Similarly, you can issue all other commands that can be executed in the command prompt of the victim machine.
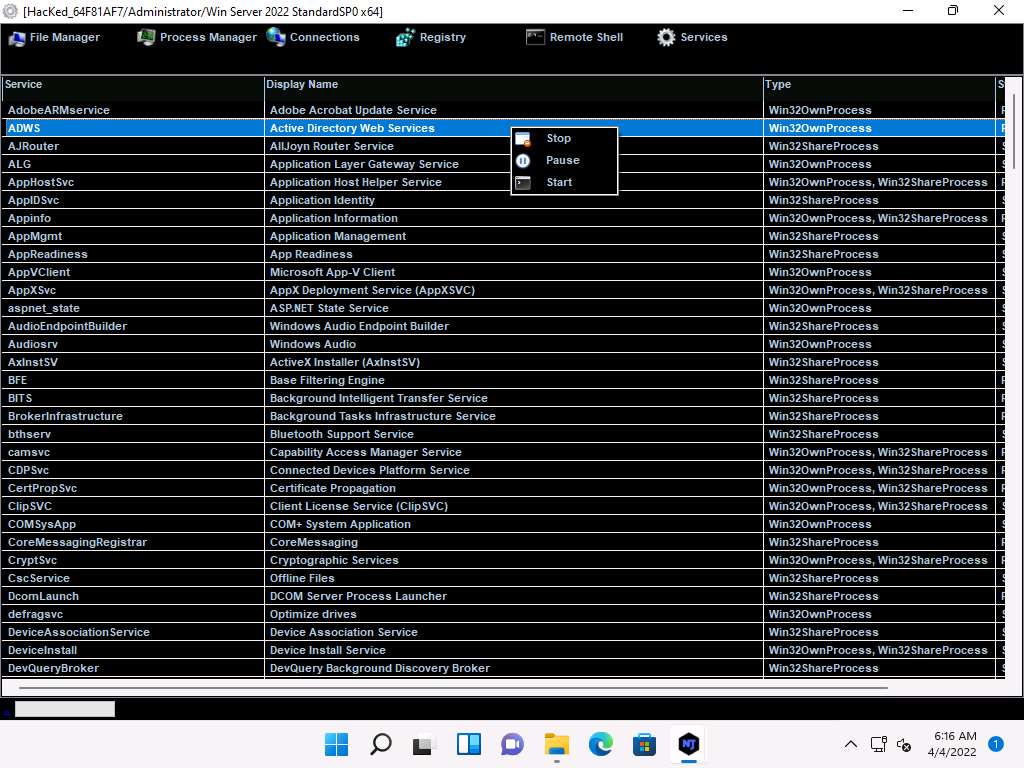
In the same way, click Services. You will be able to view all services running on the victim machine. In this section, you can use options to start, pause, or stop a service.
Screenshot Close the Manager window.
Right-click on the victim name, and then select Remote Desktop.
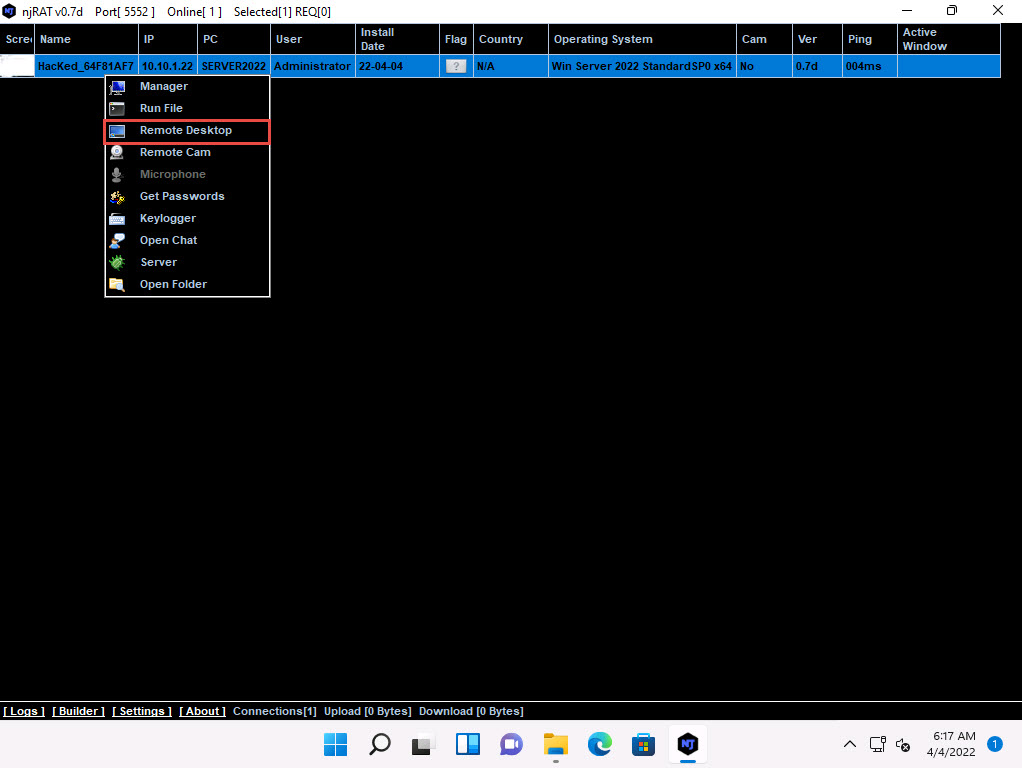
232323.jpg This launches a remote desktop connection without the victim’s awareness.
A Remote Desktop window appears; hover the mouse cursor to the top-center area of the window. A down arrow appears; click it.
It might take a while for the screen to appear.
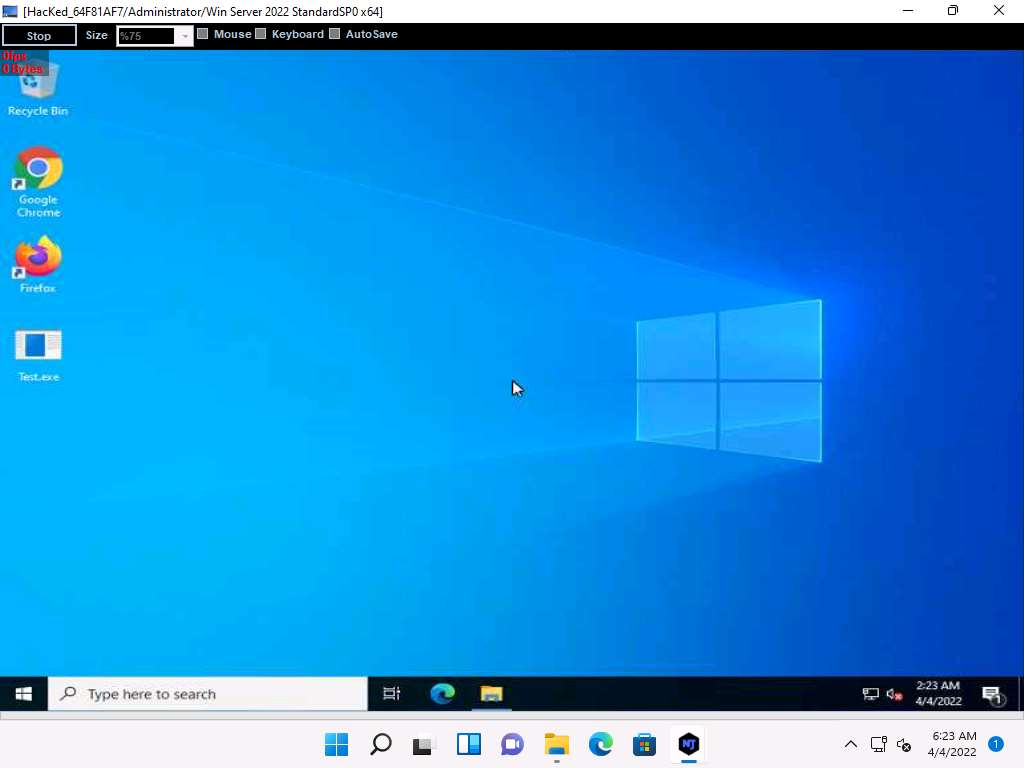
Screenshot A remote desktop control panel appears; check the Mouse option.
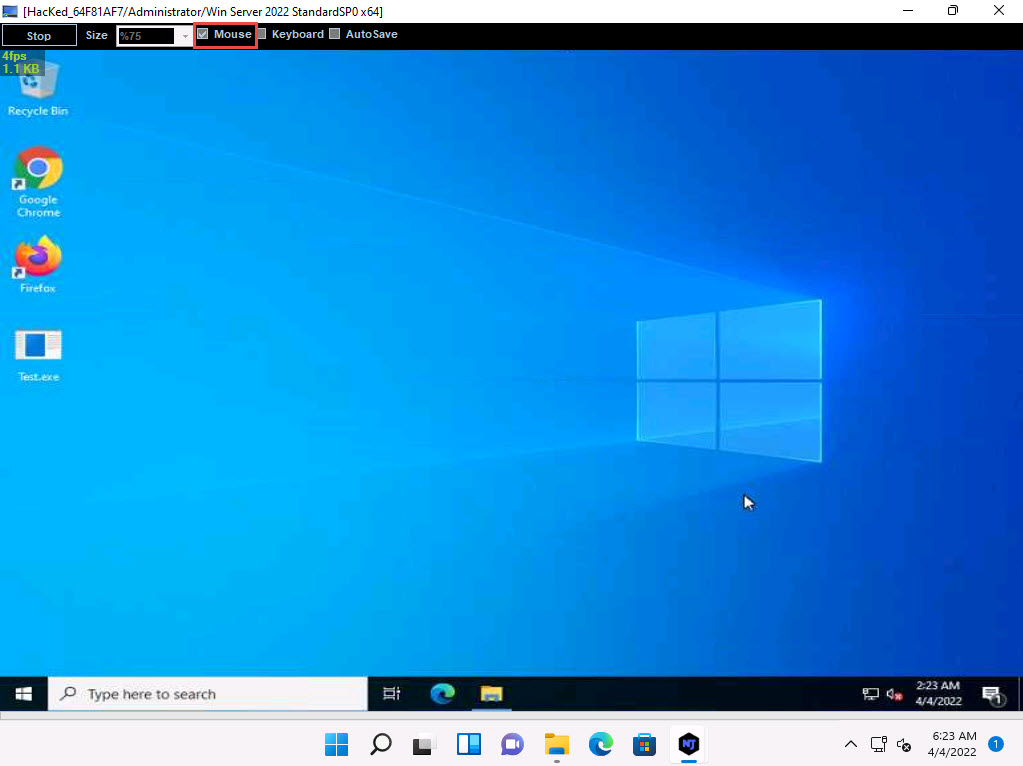
2022-04-04_14-54-10.jpg Now, you will be able to remotely interact with the victim machine using the mouse.
If you want to create any files or write any scripts on the victim machine, you need to check the Keyboard option.
On completing the task, close the Remote Desktop window.
If a Hacked pop-up appears, click Continue to close it.
In the same way, right-click on the victim name, and select Remote Cam and Microphone to spy on them and track voice conversations.
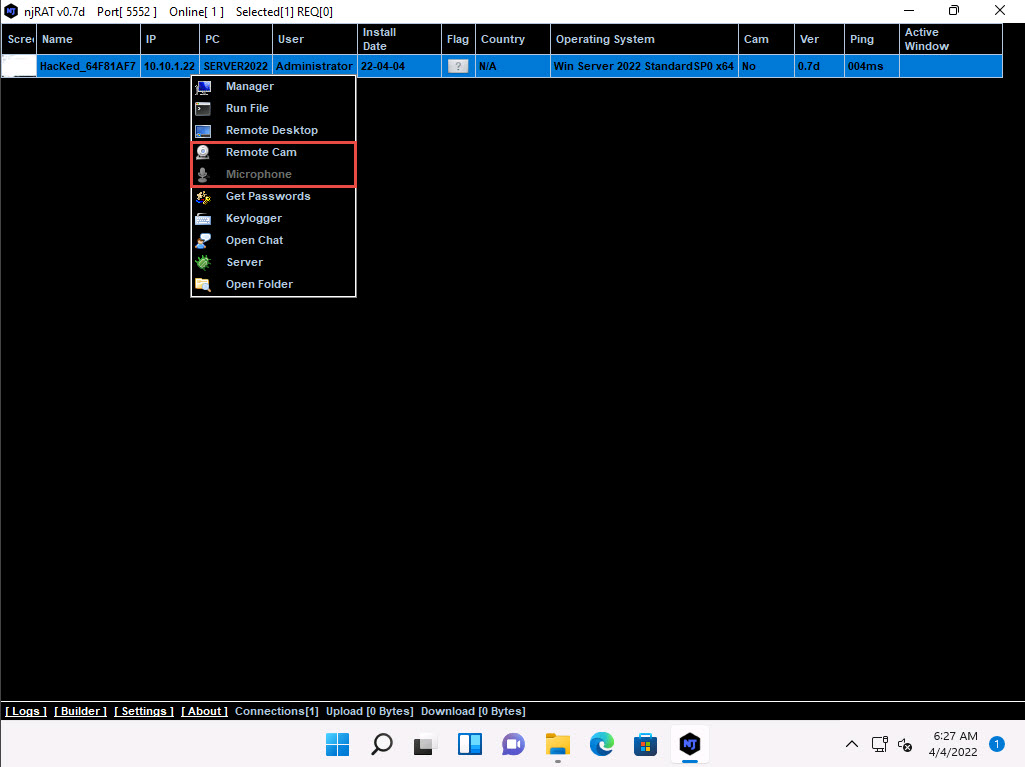
2022-04-04_14-57-18.jpg Click Windows Server 2022 to switch to the Windows Server 2022 machine. Assume that you are a legitimate user and perform a few activities such as logging into any website or typing some text in text documents.
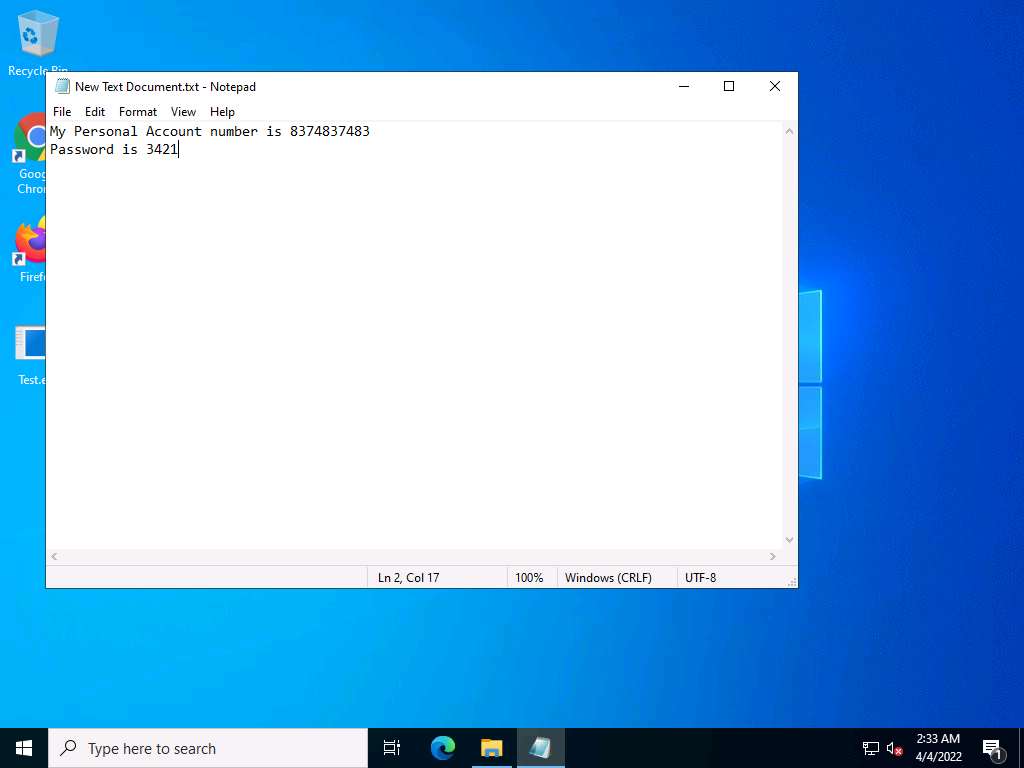
Screenshot Click Windows 11 to switch back to the Windows 11 machine, right-click on the victim name, and click Keylogger.
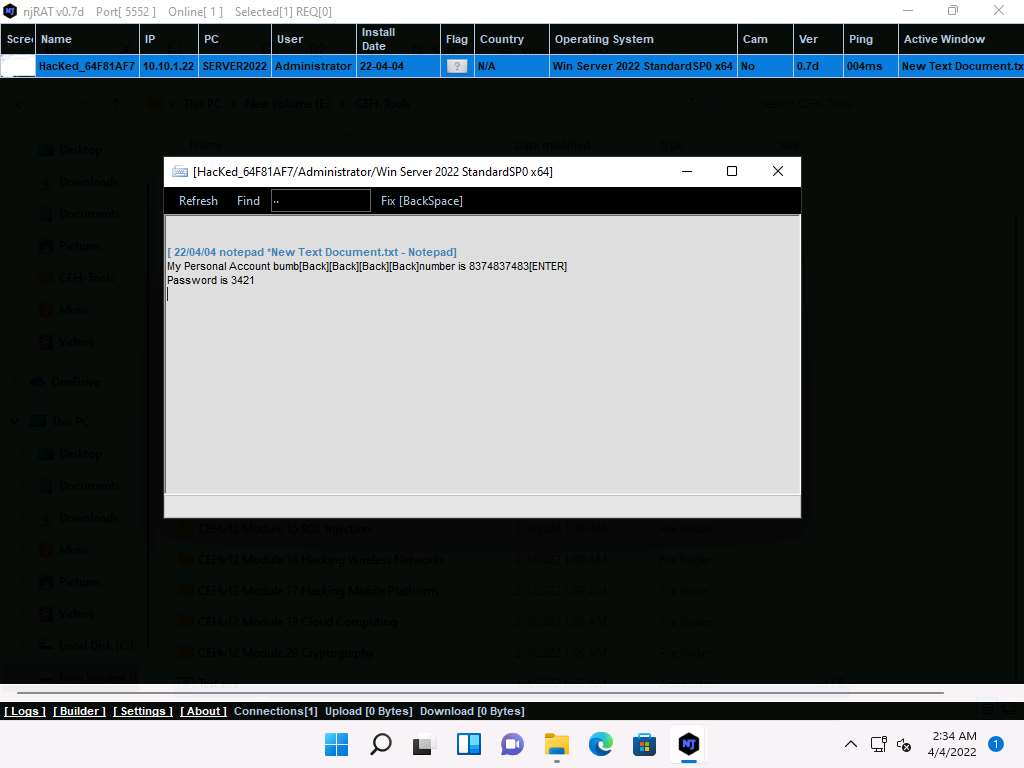
Screenshot The Keylogger window appears; wait for the window to load.
The window displays all the keystrokes performed by the victim on the Windows Server 2022 machine, as shown in the screenshot.
Screenshot Close the Keylogger window.
Right-click on the victim name, and click Open Chat.
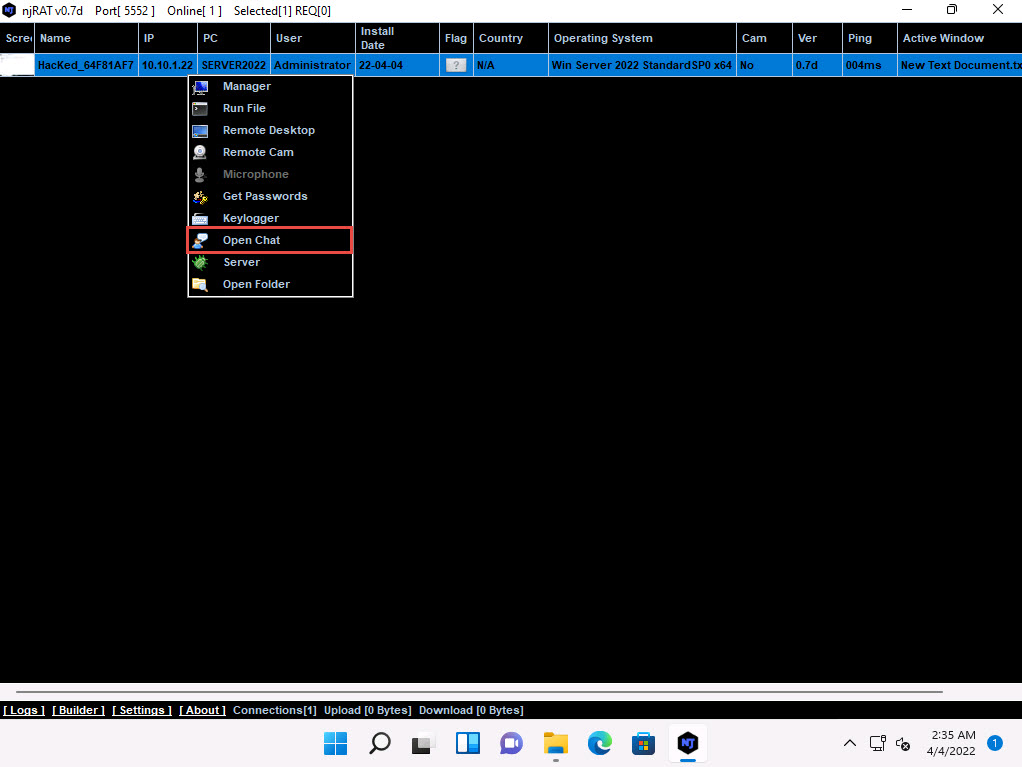
2022-04-04_15-05-43.jpg A Chat pop-up appears; enter a nickname (here, Hacker) and click OK.
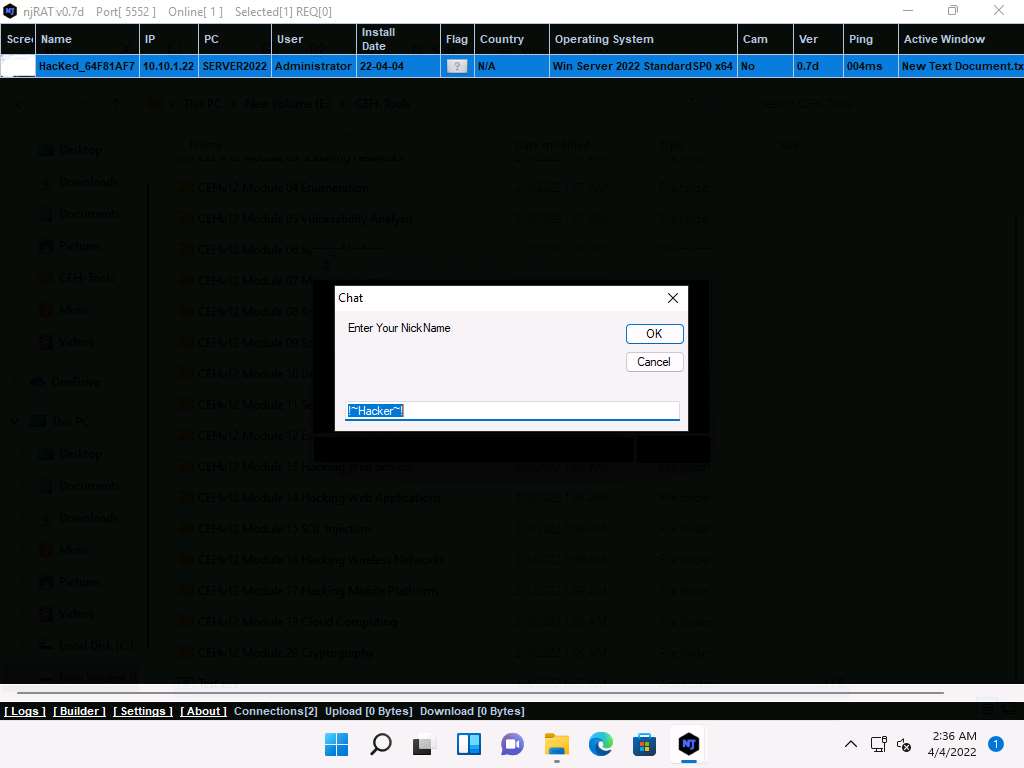
Screenshot A chat box appears; type a message, and then click Send.
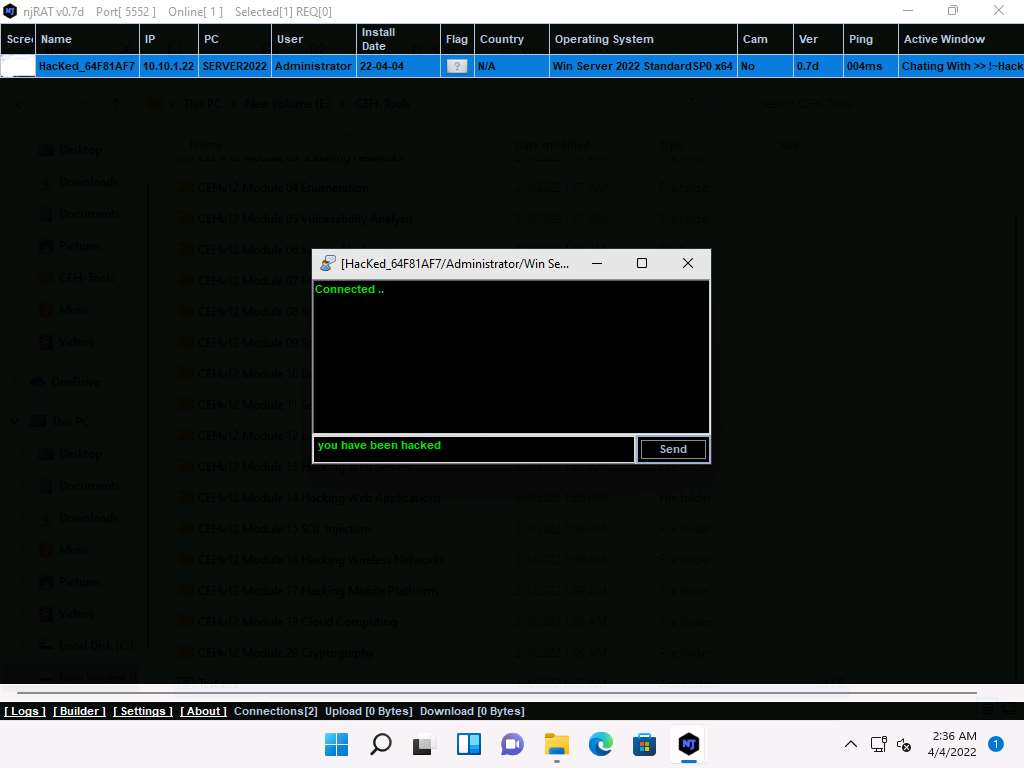
Screenshot In real-time, as soon as the attacker sends the message, a pop-up appears on the victim’s screen (Windows Server 2022), as demonstrated in the screenshot.
Click Windows Server 2022 to switch to the Windows Server 2022 machine, you can observe the message from the hacker appears on the screen.
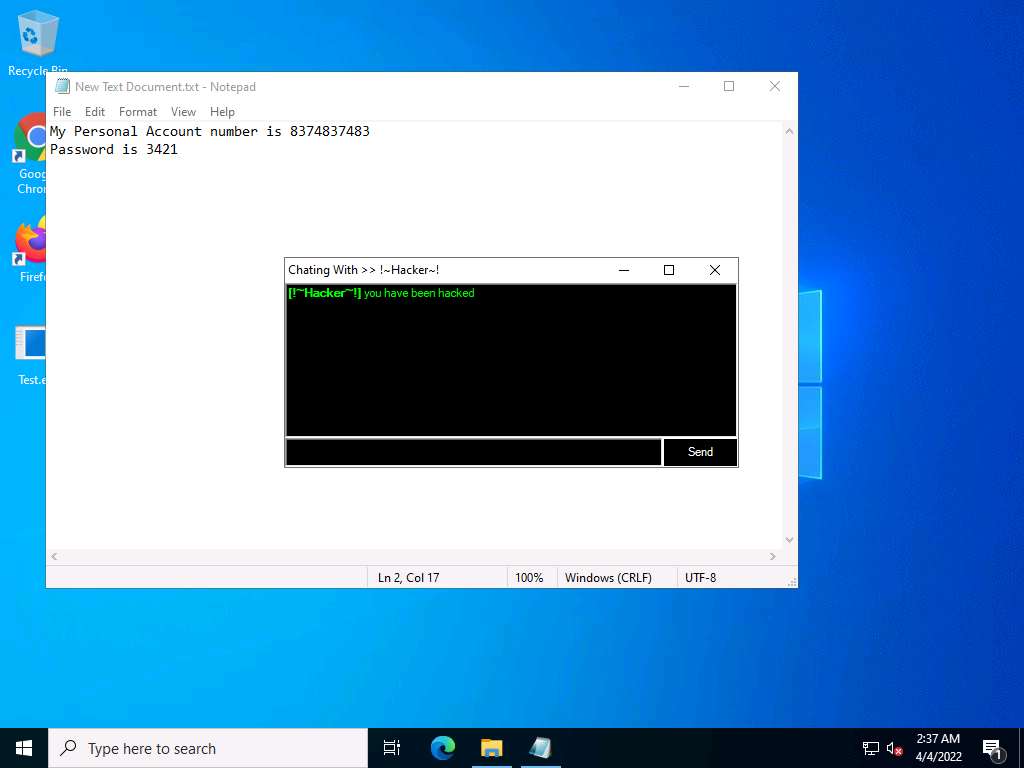
Screenshot Seeing this, the victim becomes alert and attempts to close the chatbox. Irrespective of what the victim does, the chatbox remains for open as long as the attacker uses it.
Surprised by the behavior, the victim (you) attempts to break the connection by restarting the machine. As soon as this happens, njRAT loses its connection with Windows Server 2022, as the machine is shut down in the process of restarting.

Screenshot Click Windows 11 to switch back to the attacker machine (Windows 11); you can see that the connection with the victim machine is lost.
Screenshot However, as soon as the victim logs in to their machine, the njRAT client automatically establishes a connection with the victim, as shown in the screenshot.
Click Windows Server 2022 to switch to the victim machine (Windows Server 2022).
It might take some time to establish a connection with the victim.
Task 2: Hide a Trojan using SwayzCryptor and Make it Undetectable to Various Anti-Virus Programs
At present, numerous anti-virus software programs have been configured to detect malware such as Trojans, viruses, and worms. Although security specialists keep updating the virus definitions, hackers continually try to evade or bypass them. One method that attackers use to bypass AVs is to “crypt” (an abbreviation of “encrypt”) the malicious files using fully undetectable crypters (FUDs). Crypting these files allows them to achieve their objectives, and thereby take complete control over the victim’s machine.
Crypter is a software that encrypts the original binary code of the .exe file to hide viruses, spyware, keyloggers, and RATs, among others, in any kind of file to make them undetectable by anti-viruses. SwayzCryptor is an encrypter (or “crypter”) that allows users to encrypt their program’s source code.
Task 3: Create a Trojan Server using Theef RAT Trojan
Theef is a Remote Access Trojan written in Delphi. It allows remote attackers access to the system via port 9871. Theef is a Windows-based application for both client and server. The Theef server is a virus that you install on a target computer, and the Theef client is what you then use to control the virus.
Enter the IP address of the target machine (here, Windows Server 2022) in the IP field (10.10.1.22), and leave the Port and FTP fields set to default; click Connect.
Lab 2: Infect the Target System using a Virus
Overview of Viruses and Worms
Viruses can attack a target host’s system using a variety of methods. They can attach themselves to programs and transmit themselves to other programs by making use of specific events. Viruses need such events to take place, since they cannot self-start, infect hardware, or transmit themselves using non-executable files. “Trigger” and “direct attack” events can cause a virus to activate and infect the target system when the user triggers attachments received through email, Web sites, malicious advertisements, flashcards, pop-ups, or other methods. The virus can then attack a system’s built-in programs, antivirus software, data files, and system startup settings, or perform other malicious activities.
Like a virus, a worm does not require a host to replicate, but in some cases, the worm’s host machine also infects. At first, Blackhat professionals treated worms as a mainframe problem. Later, with the introduction of the Internet, they concentrated and targeted Windows OSes using the same worms by sharing them by email, IRC, and other network functions.
Task 1: Create a Virus using the JPS Virus Maker Tool and Infect the Target System
The JPS Virus Maker tool is used to create its own customized virus. This tool has many options for building that can be used to create a virus. Some of the tool’s features are auto-start, shutdown, disable security center, lock mouse and keyboard, destroy protected storage, and terminate windows. An ethical hacker and pen-tester can use the JPS Virus Maker Tool as a proof of concept to audit perimeter security controls in an organization.
Lab 3: Perform Static Malware Analysis
Overview of Static Malware Analysis
Static Malware Analysis, also known as code analysis, involves going through the executable binary code without executing it to gain a better understanding of the malware and its purpose. The process includes the use of different tools and techniques to determine the malicious part of the program or a file. It also gathers information about malware functionality and collects the technical pointers or simple signatures it generates. Such pointers include file name, MD5 checksums or hashes, file type, and file size. Analyzing the binary code provides information about the malware’s functionality, network signatures, exploit packaging technique, dependencies involved, as well as other information.
Some of the static malware analysis techniques are:
File fingerprinting
Local and online malware scanning
Performing strings search
Identifying packing and obfuscation methods
Finding portable executable (PE) information
Identifying file dependencies
Malware disassembly
Task 1: Perform Malware Scanning using Hybrid Analysis
Hybrid Analysis is a free service that analyzes suspicious files and URLs and facilitates the quick detection of unknown threats such as viruses, worms, Trojans, and other kinds of malware.
It helps ethical hackers and penetration testers to examine files and URLs, enabling the identification of viruses, worms, Trojans, and other malicious content detected by anti-virus engines and website scanners.
VirusTotal Tool/Web -- analyzes suspicious files and URLs
You can also use other local and online malware scanning tools such as
Valkyrie (https://valkyrie.comodo.com)
Cuckoo Sandbox (https://cuckoosandbox.org)
Jotti (https://virusscan.jotti.org)
IObit Cloud (https://cloud.iobit.com) to perform online malware scanning.
Task 2: Perform a Strings Search using BinText
Software programs include some strings that are commands to perform specific functions such as printing output. Strings communicate information from a program to its user. Various strings that could represent the malicious intent of a program such as reading the internal memory or cookie data, are embedded in the compiled binary code.
Searching through strings can provide information about the basic functionality of any program. During malware analysis, search for malicious strings that could determine the harmful actions that a program can perform. For instance, if the program accesses a URL, it will have that URL string stored in it. You should be attentive while looking for strings and search for the embedded and encrypted strings for a complete analysis of the suspect file.
BinText is a text extractor that can extract text from any file. It includes the ability to find plain ASCII text, Unicode text, and Resource strings, providing useful information for each item.
The type of string is designated by a colored letter to the left of the list. ANSI strings are marked with a green “A,” Unicode strings (double byte ANSI) have a red “U,” and resource strings have a blue “R.”
You can also use other string searching tools such as
FLOSS (https://www.fireeye.com)
Strings (https://docs.microsoft.com)
Free EXE DLL Resource Extract (https://www.resourceextract.com)
FileSeek (https://www.fileseek.ca) to perform string search.
Task 3: Identify Packaging and Obfuscation Methods using PEid
Attackers often use packing and obfuscation or a packer to compress, encrypt, or modify a malware executable file to avoid detection. Obfuscation also hides the execution of the programs. When the user executes a packed program, it also runs a small wrapper program to decompress the packed file, and then runs the unpacked file. It complicates the task of reverse engineers to determine the actual program logic and other metadata via static analysis. The best approach is to try and identify if the file includes packed elements and locate the tool or method used to pack it.
PEid is a free tool that provides details about Windows executable files. It can identify signatures associated with over 600 different packers and compilers. This tool also displays the type of packer used in packing a program.
Task 4: Analyze ELF Executable File using Detect It Easy (DIE)
The Executable and Linkable Format (ELF) is a generic executable file format in Linux environment. It contains three main components including ELF header, sections, and segments. Each component plays an independent role in the loading and execution of ELF executables. The static analysis of an ELF file involves investigating an ELF executable file without running or installing it. It also involves accessing the binary code and extracting valuable artifacts from the program. Numerous tools can be used to perform static analysis on ELF files. In this task, we will be using Detect It Easy (DIE) tool to analyze ELF file.
Detect It Easy (DIE) is an application used for determining the types of files. Apart from the Windows, DIE is also available for Linux and Mac OS. It has a completely open architecture of signatures and can easily add its own algorithms for detecting or modifying the existing signatures. It detects a file’s compiler, linker, packer, etc. using a signature-based detection method.
You can also use other packaging/obfuscation tools such as
Macro_Pack (https://github.com)
UPX (https://upx.github.io)
ASPack (http://www.aspack.com) to identify packing/obfuscation methods.
Task 5: Find the Portable Executable (PE) Information of a Malware Executable File using PE Explorer
The Portable Executable (PE) format is the executable file format used on Windows OSes that stores the information a Windows system requires to manage the executable code. The PE stores metadata about the program, which helps in finding additional details of the file. For instance, the Windows binary is in PE format that consists of information such as time of creation and modification, import and export functions, compilation time, DLLs, and linked files, as well as strings, menus, and symbols.
PE Explorer lets you open, view, and edit a variety of different 32-bit Windows executable file types (also called PE files) ranging from common such as EXE, DLL, and ActiveX Controls to less familiar types such as SCR (Screensavers), CPL (Control Panel Applets), SYS, MSSTYLES, BPL, DPL, and more (including executable files that run on MS Windows Mobile platform).
q
You can also use other PE extraction tools such as
Portable Executable Scanner (pescan) (https://tzworks.net)
Resource Hacker (http://www.angusj.com)
PEView (https://www.aldeid.com) to find the Portable Executable (PE) information of a malware executable file.
Task 6: Identify File Dependencies using Dependency Walker
Any software program depends on the various inbuilt libraries of an OS that help in performing specified actions in a system. Programs need to work with internal system files to function correctly. Programs store their import and export functions in a kernel32.dll file. File dependencies contain information about the internal system files that the program needs to function properly; this includes the process of registration and location on the machine.
Find the libraries and file dependencies, as they contain information about the run-time requirements of an application. Then, check to find and analyze these files to provide information about the malware in the file. File dependencies include linked libraries, functions, and function calls. Check the dynamically linked list in the malware executable file. Finding out all library functions may allow guessing about what the malware program can do. You should know the various DLLs used to load and run a program.
The Dependency Walker tool lists all dependent modules of an executable file and builds hierarchical tree diagrams. It also records all functions that each module exports and calls. Further, it detects many common application problems such as missing and invalid modules, import and export mismatches, circular dependency errors, mismatched machine modules, and module initialization failures.
You can also use other dependency checking tools such as
Dependency-check (https://jeremylong.github.io)
Snyk (https://snyk.io)
RetireJS (https://retirejs.github.io) to identify file dependencies.
Task 7: Perform Malware Disassembly using IDA and OllyDbg
Static analysis also includes the dismantling of a given executable into binary format to study its functionalities and features. This process helps identify the language used for programming the malware, look for APIs that reveal its function, and retrieve other information. Based on the reconstructed assembly code, you can inspect the program logic and recognize its threat potential. This process uses debugging tools such as IDA Pro and OllyDbg.
IDA As a disassembler, IDA explores binary programs, for which the source code might not be available, to create maps of their execution. The primary purpose of a disassembler is to display the instructions actually executed by the processor in a symbolic representation called “assembly language.” However, in real life, things are not always simple. Hostile code usually does not cooperate with the analyst. Viruses, worms, and Trojans are often armored and obfuscated; as such, more powerful tools are required. The debugger in IDA complements the static analysis capabilities of the disassembler. By allowing an analyst to single-step through the code being investigated, the debugger often bypasses the obfuscation. It helps obtain data that the more powerful static disassembler will be able to process in depth.
OllyDbg OllyDbg is a debugger that emphasizes binary code analysis, which is useful when source code is unavailable. It traces registers, recognizes procedures, API calls switches, tables, constants, and strings, and locates routines from object files and libraries.
IDA Pro -- Tool
IDA Pro -- ToolOllyDbg - Tool
OllyDbg - ToolTask 8: Perform Malware Disassembly using Ghidra
Ghidra is a software reverse engineering (SRE) framework that includes a suite of full-featured, high-end software analysis tools that enable users to analyze compiled code on a variety of platforms including Windows, MacOS, and Linux. It's capabilities include disassembly, assembly, decompilation, debugging, emulation, graphing, and scripting. Ghidra supports a wide variety of processor instruction sets and executable formats and can be run in both user-interactive and automated modes. Analysts can also develop their own Ghidra plug-in components and/or scripts using the exposed API. In addition there are numerous ways to extend Ghidra such as new processors, loaders/exporters, automated analyzers, and new visualizations.
You can also use other disassembling and debugging tools such as
Radare2 (https://rada.re)
WinDbg (http://www.windbg.org)
ProcDump (https://docs.microsoft.com) to perform malware disassembly.
Lab 4: Perform Dynamic Malware Analysis
Overview of Dynamic Malware Analysis
Dynamic analysis is performed to gather valuable information about malware activity, including the files and folders created, ports and URLs accessed, called functions and libraries, applications and tools accessed, information transferred, settings modified processes, and services the malware started, and other items. You should design and set up the environment for performing the dynamic analysis in such a way that the malware cannot propagate to the production network, and ensure that the testing system can recover to an earlier set timeframe (prior to launching the malware) in case anything goes wrong during the test.
To achieve this, you need to perform the following:
System Baselining Baselining refers to the process of capturing a system’s state (taking snapshot of the system) at the time the malware analysis begins. This can be used to compare the system’s state after executing the malware file, which will help understand the changes that the malware has made across the system. A system baseline involves recording details of the file system, registry, open ports, network activity, and other items.
Host Integrity Monitoring Host integrity monitoring is the process of studying the changes that have taken place across a system or a machine after a series of actions or incidents. It involves using the same tools to take a snapshot of the system before and after the incident or actions and analyzing the changes to evaluate the malware’s impact on the system and its properties. In malware analysis, host integrity monitoring helps to understand the runtime behavior of a malware file as well as its activities, propagation techniques, URLs accessed, downloads initiated, and other characteristics.
Host integrity monitoring includes:
Port monitoring
Process monitoring
Registry monitoring
Windows services monitoring
Startup program monitoring
Event logs monitoring and analysis
Installation monitoring
Files and folder monitoring
Device driver monitoring
Network traffic monitoring and analysis
DNS monitoring and resolution
API calls monitoring
Task 1: Perform Port Monitoring using TCPView and CurrPorts
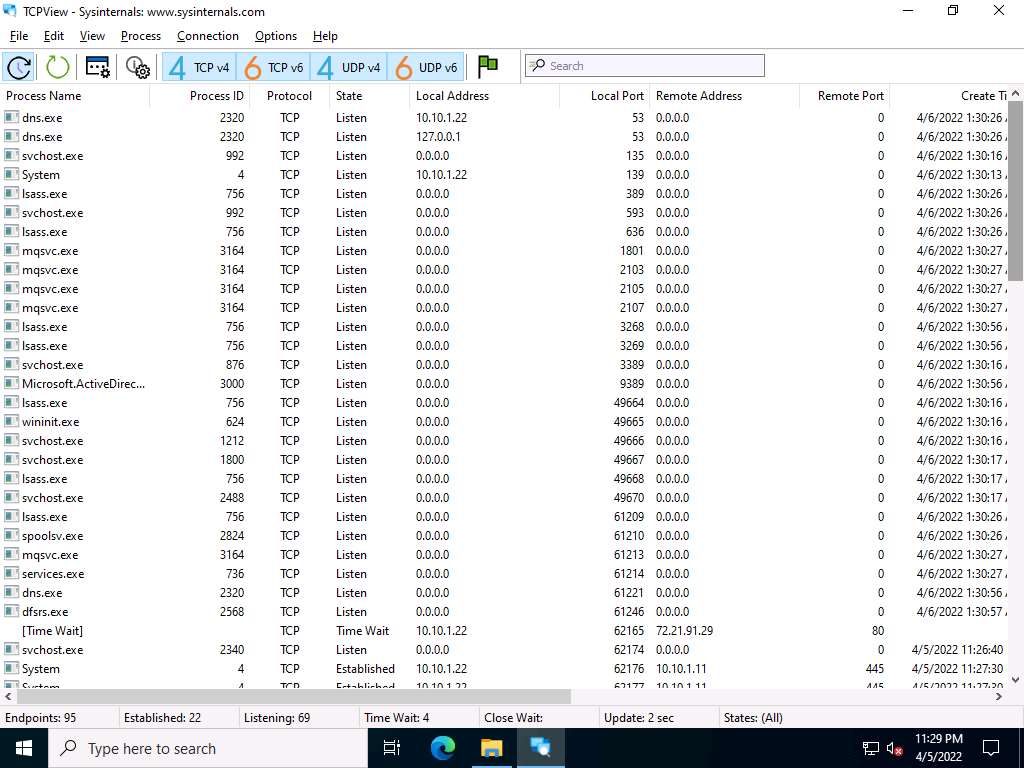
TCPView TCPView is a Windows program that shows the detailed listings of all the TCP and UDP endpoints on the system, including the local and remote addresses, and the state of the TCP connections. It provides a subset of the Netstat program that ships with Windows. The TCPView download includes Tcpvcon, a command-line version with the same functionality. When TCPView runs, it enumerates all active TCP and UDP endpoints, resolving all IP addresses to their domain name versions.
CurrPorts CurrPorts is a piece of network monitoring software that displays a list of all the currently open TCP/IP and UDP ports on a local computer. For each port in the list, information about the process that opened the port is also displayed, including the process name, full path of the process, version information of the process (product name, file description, etc.), the time that the process was created, and the user that created it.
TCPView -- Tool
If a TCPView License Agreement window appears, click the Agree button to agree to the terms and conditions.
The TCPView main window appears, displaying the details such as Process, ProcessId, Protocol, Local Address, Local Port, Remote Address, Remote Port, and State, as shown in the screenshot.
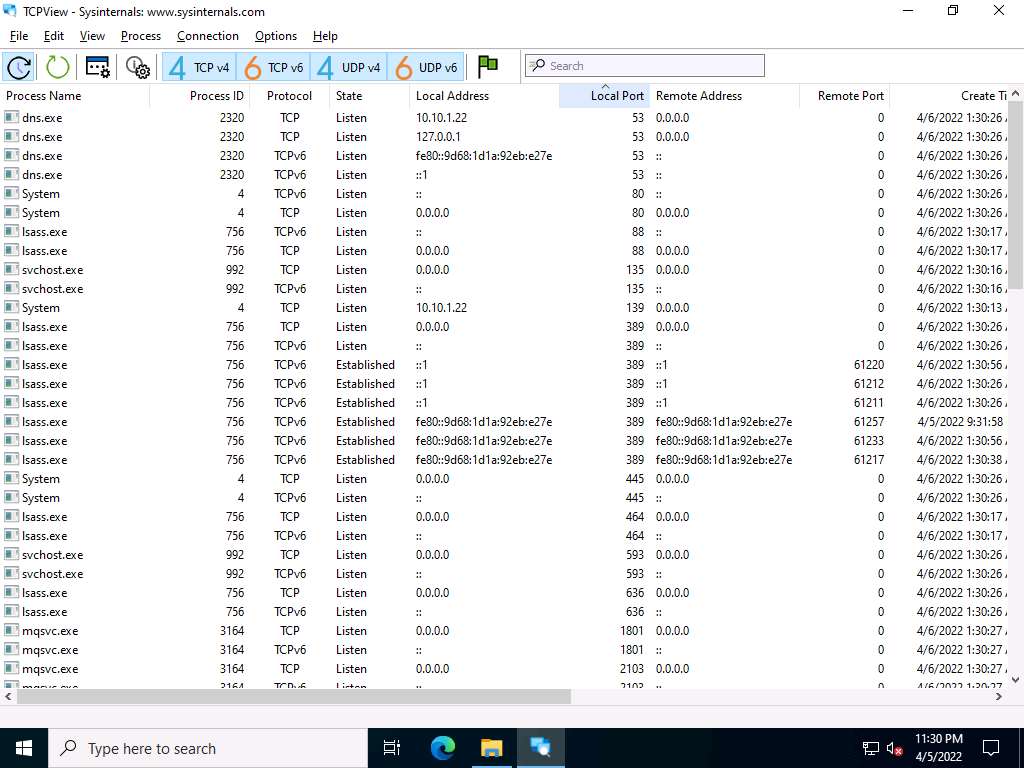
Screenshot TCPView performs Port monitoring. Click the Local Port tab to view the ports in serial order.
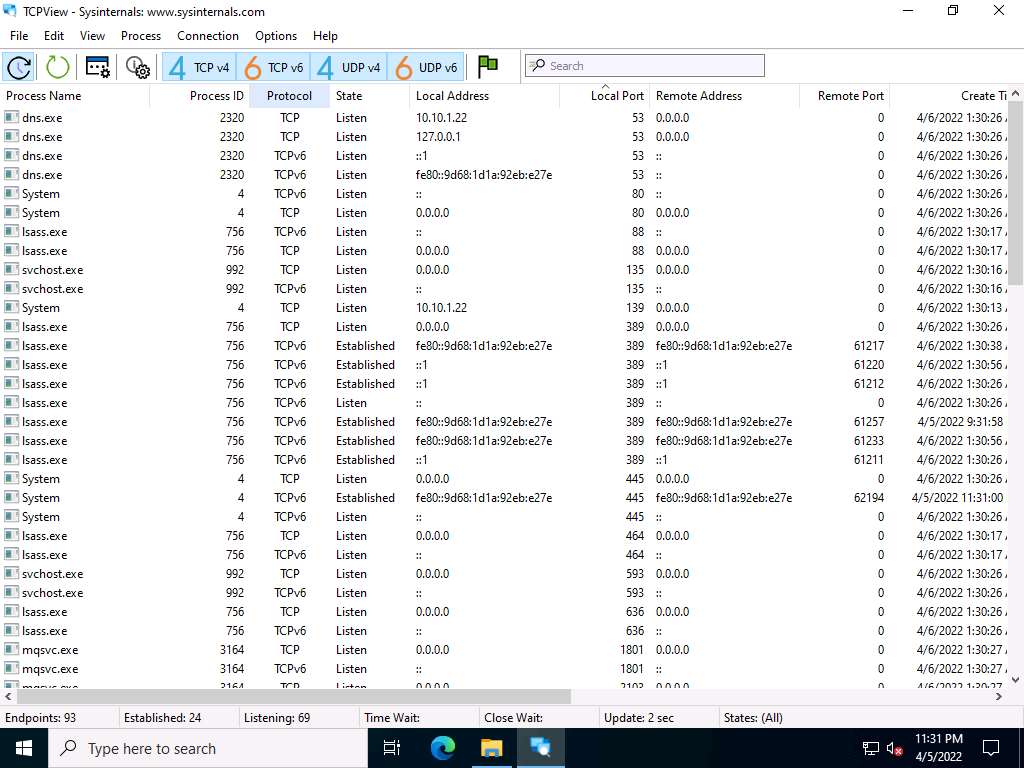
Screenshot Observe the protocols running on different ports under the Protocol column.
Screenshot As you have executed a malicious application, now search for the Trojan.exe process in the TCPView.
You can observe that the Trojan.exe malicious program is running on the Windows Server 2022 machine. You can see details such as Remote Address and Remote Port.
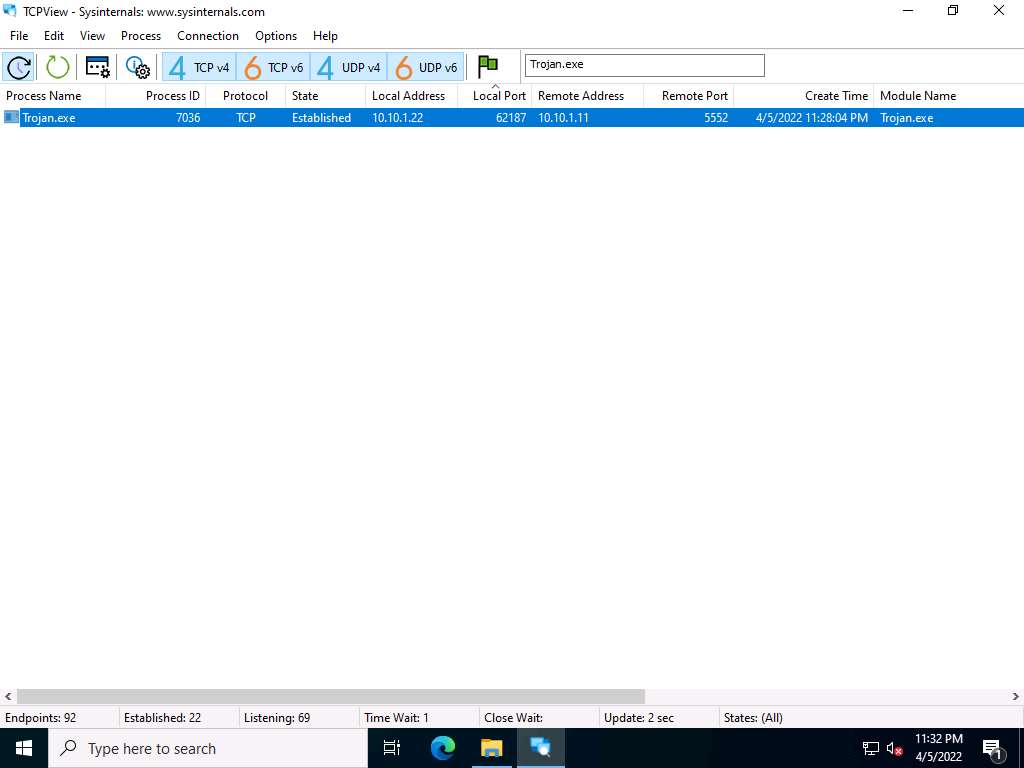
Screenshot Right-click the process Trojan.exe; select Kill Process… to end the running process.
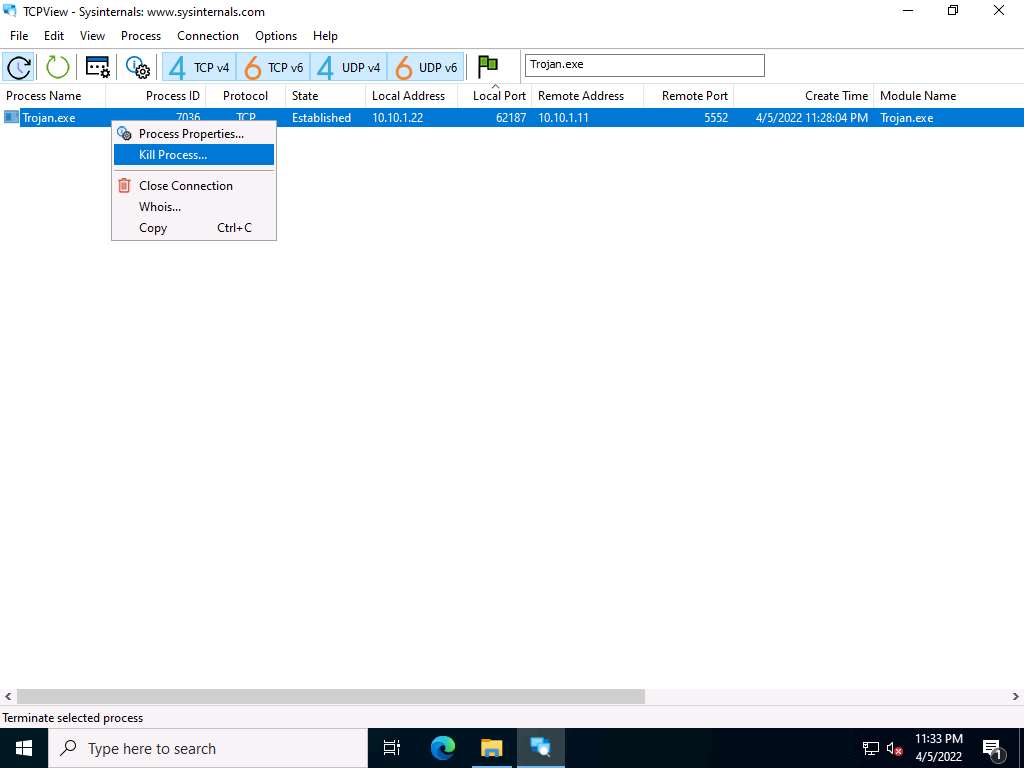
Screenshot Normally, if a TCPView dialog box appears, click OK to terminate the process. However, for this task, do not Kill the process in this step as we are going to use this running process for the next task; click Cancel.
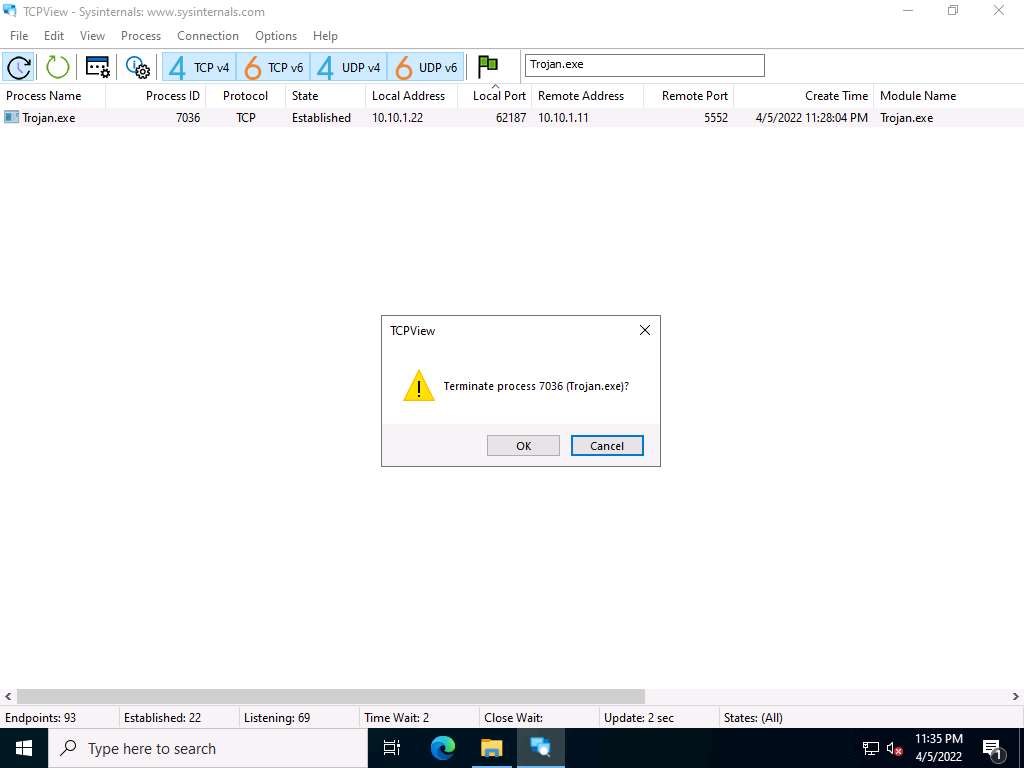
Screenshot This way, you can view all processes running on the machine and stop unwanted or malicious processes that may affect your system. If you are unable to stop a process, you can view the port on which it is running and add a firewall rule to block the port.
CurrPorts -- Tool
The CurrPorts window appears, displaying a list of currently open TCP/IP and UDP ports on the machine.
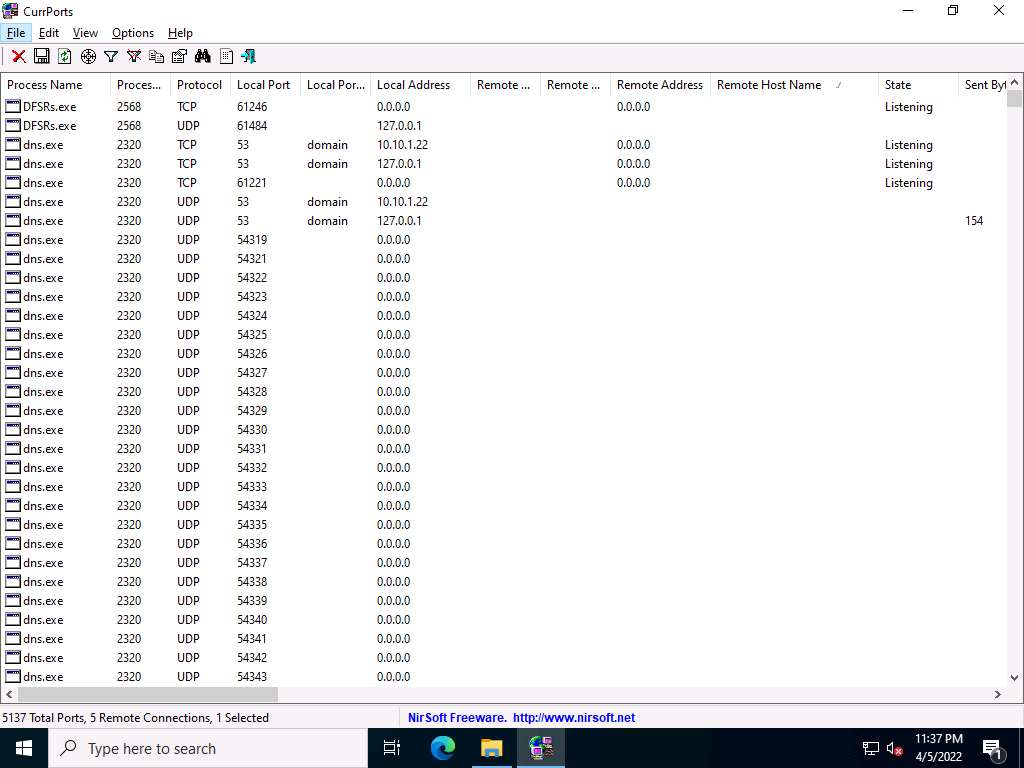
Screenshot Scroll-down to search for Trojan.exe process running on the machine, as the shown in the screenshot. It is evident from the above screenshot that the process is connected to the machine on port 5552.
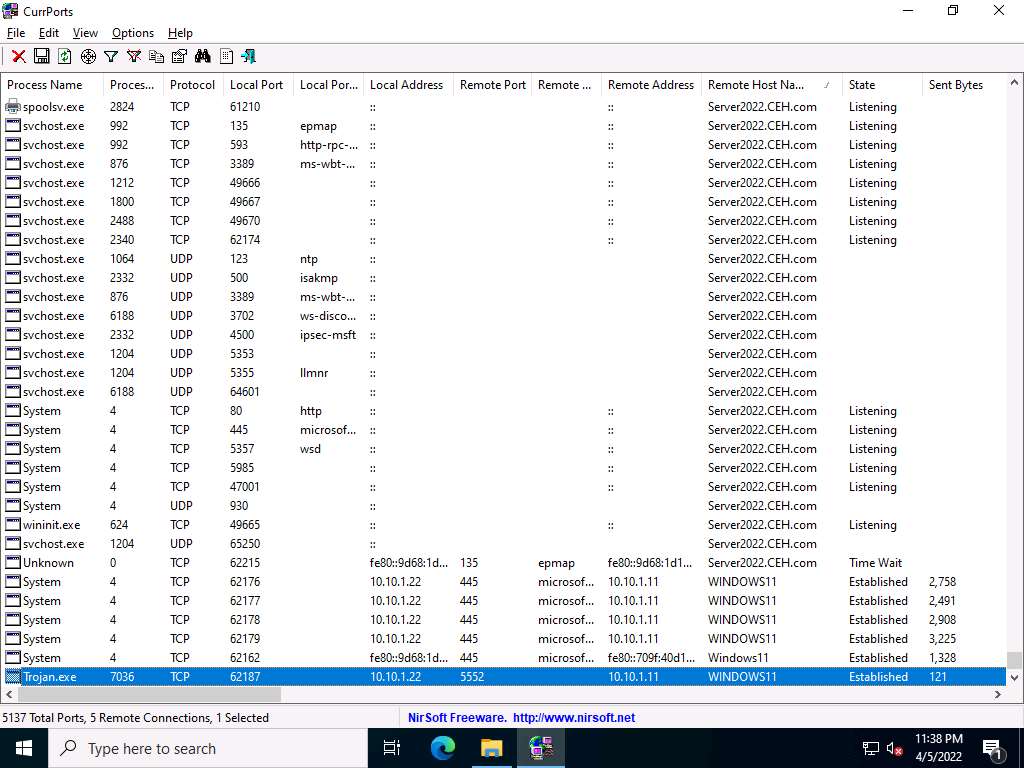
Screenshot You can view the properties of the process by right-clicking on the process and clicking Properties from the Context menu.
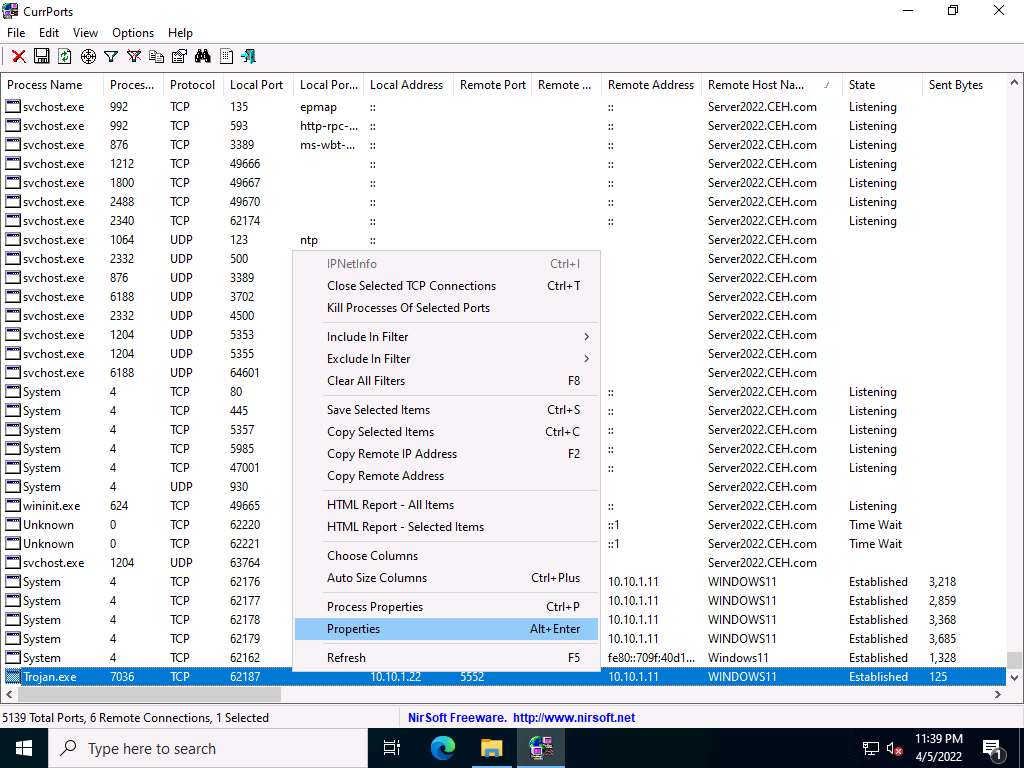
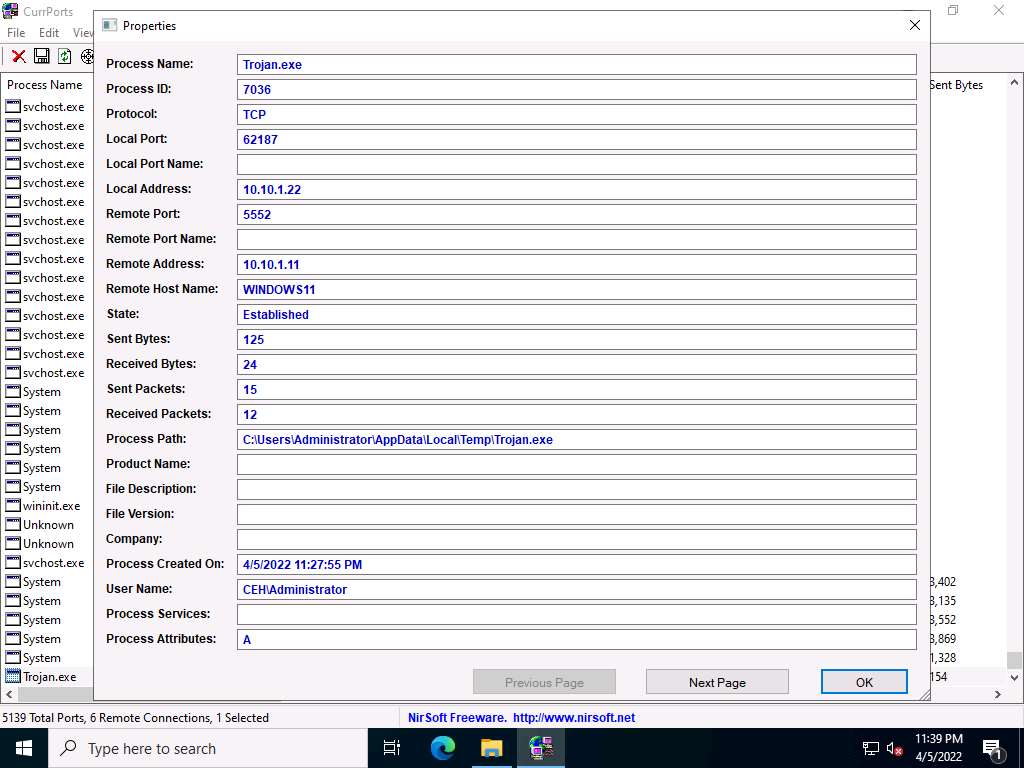
Screenshot The Properties window appears, displaying information related to the process such as the name of the process, its process ID, Remote Address, Process Path, Remote Host Name, and other details.
Once you are done examining the properties associated with the process, click OK.
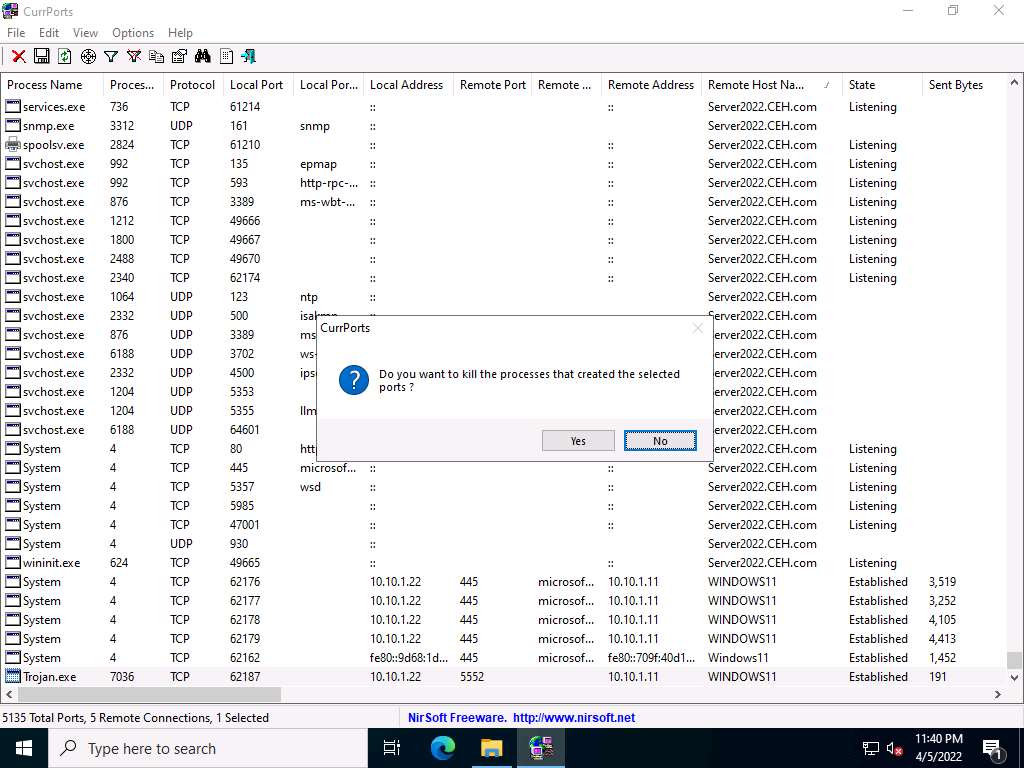
Screenshot Because Trojan.exe is a malicious process, you may end the process by right-clicking on it and selecting Kill Processes Of Selected Ports from the context menu.
Alternatively, you may select Close Selected TCP Connections, so that the port closes, and the attacker can never regain connection through the port unless you open it.
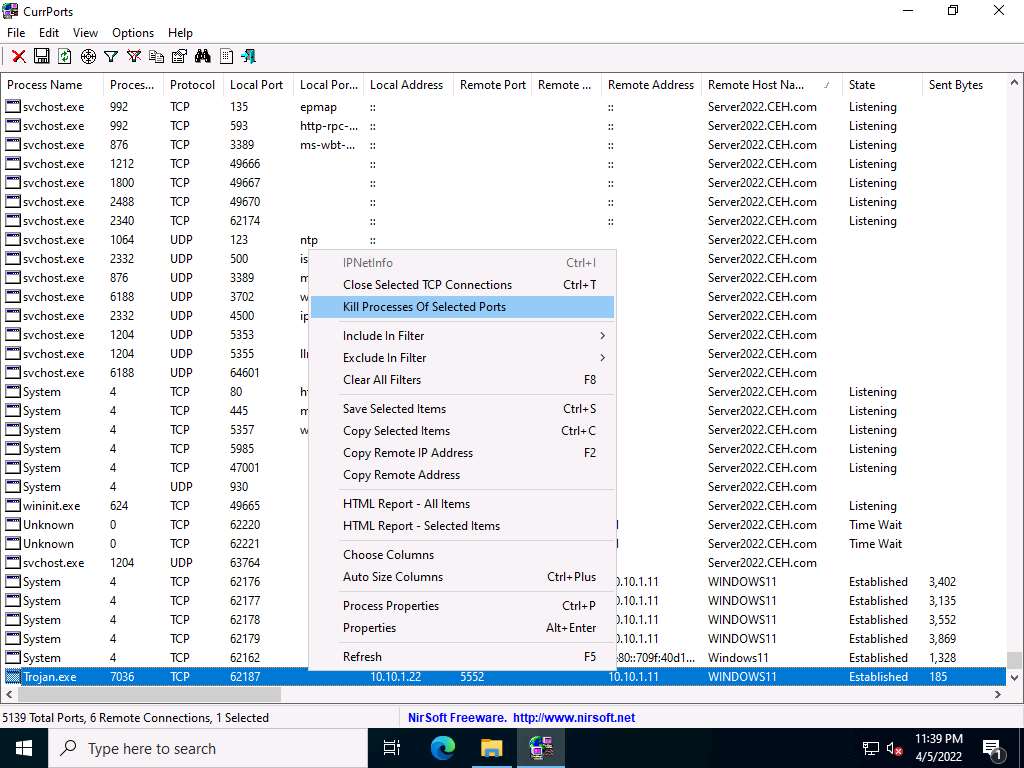
Screenshot Normally, when the CurrPorts dialog-box appears, you would click Yes to close the connection. However, do not Kill the process at this step, as this running process will be used for the next task; click No.
Screenshot This way, you can analyze the ports open on a machine and the processes running on it.
Task 2: Perform Process Monitoring using Process Monitor
Process Monitor is a monitoring tool for Windows that shows the real-time file system, Registry, and process and thread activity. It combines the features of two legacy Sysinternals utilities, Filemon and Regmon. It adds an extensive list of enhancements including rich and non-destructive filtering, comprehensive event properties such session IDs and user names, reliable process information, full thread stacks with integrated symbol support for each operation, and simultaneous logging to a file. Unique features of Process Monitor make it a core utility in system troubleshooting and vital to the malware hunting toolkit.
You can also use other process monitoring tools such as
Process Explorer (https://docs.microsoft.com)
OpManager (https://www.manageengine.com)
Monit (https://mmonit.com)
ESET SysInspector (https://www.eset.com) to perform process monitoring.
Task 3: Perform Registry Monitoring using Reg Organizer
The Windows Registry stores OS and program configuration details such as settings and options. If the malware is a program, the registry stores its functionality. When an attacker installs a type of malware on the victim’s machine, it generates a registry entry. One must have fair knowledge of the Windows Registry, its contents, and inner workings to analyze the presence of malware. Scanning for suspicious registries will help to detect malware. While most computer users generally do not do this, monitoring the registry entries is a great way to track any modifications made to your system.
Registry monitoring tools such as Reg Organizer provide a simple way to track registry modifications, which is useful in troubleshooting and monitoring background changes.
Reg Organizer
Reg Organizer is designed to edit keys and parameters, as well as to delete the content of.reg files. It allows users to perform various operations with the system registry such as export, import and copy key values. It can also perform a deep searches to find even those keys associated with the application that cannot be found by other similar programs.
You can also use other registry monitoring tools such as
regshot (https://sourceforge.net)
Registry Viewer (https://accessdata.com)
RegScanner (https://www.nirsoft.net)
Registrar Registry Manager (https://www.resplendence.com) to perform registry monitoring.
Task 4: Perform Windows Services Monitoring using Windows Service Manager (SrvMan)
Attackers design malware and other malicious code in such a way that they install and run on a computer device in the form of a service. As most services run in the background to support processes and applications, malicious services are invisible, even when they are performing harmful activities on the system, and can even function without intervention or input. Malware spawns Windows services that allow attackers to control the victim machine and pass malicious instructions remotely. Malware may also employ rootkit techniques to manipulate the following registry keys to hide their processes and services.
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services These malicious services run as the SYSTEM account or another privileged account, which provides more access compared to regular user accounts, making them more dangerous than common malware and executable code. Attackers also try to conceal their actions by naming the malicious services with the names similar to genuine Windows services to avoid detection.
You can trace malicious services initiated by the suspect file during dynamic analysis by using Windows service monitoring tools such as Windows Service Manager (SrvMan), which can detect changes in services and scan for suspicious Windows services.
SrvMan has both GUI and Command-line modes. It can also be used to run arbitrary Win32 applications as services (when such a service is stopped, the main application window automatically closes).
You can also use other Windows service monitoring tools such as
Advanced Windows Service Manager (https://securityxploded.com)
Process Hacker (https://processhacker.sourceforge.io)
Netwrix Service Monitor (https://www.netwrix.com)
AnVir Task Manager (https://www.anvir.com) to perform Windows services monitoring.
Task 5: Perform Startup Program Monitoring using Autoruns for Windows and WinPatrol
Autoruns for Windows This utility can auto-start the location of any startup monitor, display which programs are configured to run during system bootup or login, and show the entries in the order Windows processes them. As soon as this program is included in the startup folder, Run, RunOnce, and other Registry keys, users can configure Autoruns to show other locations, including Explorer shell extensions, toolbars, browser helper objects, Winlogon notifications, and auto-start services. Autoruns’ Hide Signed Microsoft Entries option helps the user zoom in on third-party auto-starting images that add to the users’ system, and it has support for looking at the auto-starting images configured for other accounts configured on the system.
WinPatrol WinPatrol provides the user with 14 different tabs to help in monitoring the system and its files. This security utility gives the user a chance to look for programs that are running in the background of a system so that the user can take a closer look and control the execution of legitimate and malicious programs.
Autoruns -- Tool
WinPatrol -- Tool
You can also use other Windows startup programs monitoring tools such as
Autorun Organizer (https://www.chemtable.com)
Quick Startup (https://www.glarysoft.com)
Chameleon Startup Manager (https://www.chameleon-managers.com) to perform startup programs monitoring.
Task 6: Perform Installation Monitoring using Mirekusoft Install Monitor
Mirekusoft Install Monitor automatically monitors what gets placed on your system and allows you to uninstall it completely. Install Monitor works by monitoring what resources such as file and registry, are created when a program is installed. It provides detailed information about the software installed, including how much disk space, CPU, and memory your programs are using. It also provides information about how often you use different programs. A program tree is a useful tool that can show you which programs were installed together.
You can also use other installation monitoring tools such as
SysAnalyzer (https://www.aldeid.com)
Advanced Uninstaller PRO (https://www.advanceduninstaller.com)
REVO UNINSTALLER PRO (https://www.revouninstaller.com),
Comodo Programs Manager (https://www.comodo.com) to perform installation monitoring.
Task 7: Perform Files and Folder Monitoring using PA File Sight
Malware can modify system files and folders to save information in them. You should be able to find the files and folders that malware creates and analyze them to collect any relevant stored information. These files and folders may also contain hidden program code or malicious strings that the malware plans to execute on a specific schedule.
You can also use other file and folder integrity checking tools such as
Tripwire File Integrity and Change Manager (https://www.tripwire.com)
Netwrix Auditor (https://www.netwrix.com)
Verisys (https://www.ionx.co.uk)
CSP File Integrity Checker (https://www.cspsecurity.com) to perform file and folder monitoring.
Task 8: Perform Device Driver Monitoring using DriverView and Driver Reviver
DriverView The DriverView utility displays a list of all device drivers currently loaded on the system. For each driver in the list, additional information is displayed such as the load address of the driver, description, version, product name, and developer.
Driver Reviver Without proper drivers, computers start to misbehave. Sometimes updating the drivers using conventional methods can be a daunting task. Outdated drivers are more vulnerable to hacking and can lead to a breach in the system. Driver Reviver provides an effective way of scanning your PC to identify out of date drivers. Driver Reviver can quickly and easily update these drivers to restore optimum performance to your PC and its hardware and extend its life.
DriverView -- Tool
Driver Reviver -- Tool
You can also use other device driver monitoring tools such as
Driver Booster (https://www.iobit.com)
Driver Easy (https://www.drivereasy.com)
Driver Fusion (https://treexy.com)
Driver Genius 22 (https://www.driver-soft.com) to perform device driver monitoring.
Task 9: Perform DNS Monitoring using DNSQuerySniffer
DNSQuerySniffer is a network sniffer utility that shows the DNS queries sent on your system. For every DNS query, the following information is displayed: Host Name, Port Number, Query ID, Request Type (A, AAAA, NS, MX, and other types), Request Time, Response Time, Duration, Response Code, Number of records, and the content of the returned DNS records. You can easily export the DNS query information to a CSV, tab-delimited, XML, or HTML file, or copy the DNS queries to the clipboard and then paste them into Excel or another spreadsheet application.
You can also use other DNS monitoring/resolution tools such as
DNSstuff (https://www.dnsstuff.com)
Sonar Lite (https://constellix.com) to perform DNS monitoring
Hacker's Mantra:We need to have a talk on the subject of what's yours and what's mine. - Stieg Larsson