🔎Module 03: Enumeration
Objective
The objective of the lab is to extract information about the target organization that includes, but is not limited to:
Machine names, their OSes, services, and ports
Network resources
Usernames and user groups
Lists of shares on individual hosts on the network
Policies and passwords
Routing tables
Audit and service settings
SNMP and FQDN details
Overview of Enumeration
Enumeration creates an active connection with the system and performs directed queries to gain more information about the target. It extracts lists of computers, usernames, user groups, ports, OSes, machine names, network resources, and services using various techniques. Enumeration techniques are conducted in an intranet environment.
Lab 1: Perform NetBIOS Enumeration
Task 1: Perform NetBIOS Enumeration using Windows Command-Line Utilities
Nbtstat helps in troubleshooting NETBIOS name resolution problems. The nbtstat command removes and corrects preloaded entries using several case-sensitive switches. Nbtstat can be used to enumerate information such as NetBIOS over TCP/IP (NetBT) protocol statistics, NetBIOS name tables for both the local and remote computers, and the NetBIOS name cache.
nbtstat -a [IP address of the remote machine]
-a displays the NetBIOS name table of a remote computer.
-c lists the contents of the NetBIOS name cache of the remote computer.
Now, type net use and press Enter. The output displays information about the target such as connection status, shared folder/drive and network information, as shown in the screenshot.
Using this information, the attackers can read or write to a remote computer system, depending on the availability of shares, or even launch a DoS attack. This concludes the demonstration of performing NetBIOS enumeration using Windows command-line utilities such as Nbtstat and Net use.
Task 2: Perform NetBIOS Enumeration using NetBIOS Enumerator
NetBIOS Enumerator is a tool that enables the use of remote network support and several other techniques such as SMB (Server Message Block). It is used to enumerate details such as NetBIOS names, usernames, domain names, and MAC addresses for a given range of IP addresses.
NetBIOS Enumerator
Task 3: Perform NetBIOS Enumeration using an NSE Script
NSE allows users to write (and share) simple scripts to automate a wide variety of networking tasks. NSE scripts can be used for discovering NetBIOS shares on the network. Using the nbstat NSE script, for example, you can retrieve the target’s NetBIOS names and MAC addresses. Moreover, increasing verbosity allows you to extract all names related to the system.
--script nbstat.nse
Global Network Inventory (http://www.magnetosoft.com)
Advanced IP Scanner (https://www.advanced-ip-scanner.com)
Hyena (https://www.systemtools.com)
Nsauditor Network Security Auditor (https://www.nsauditor.com)
Lab 2: Perform SNMP Enumeration
Task 1: Perform SNMP Enumeration using snmp-check
snmp-check is a tool that enumerates SNMP devices, displaying the output in a simple and reader-friendly format. The default community used is “public.” As an ethical hacker or penetration tester, it is imperative that you find the default community strings for the target device and patch them up.
snmp-check
Task 2: Perform SNMP Enumeration using SoftPerfect Network Scanner
SoftPerfect Network Scanner can ping computers, scan ports, discover shared folders, and retrieve practically any information about network devices via WMI (Windows Management Instrumentation), SNMP, HTTP, SSH, and PowerShell.
The program also scans for remote services, registries, files, and performance counters. It can check for a user-defined port and report if one is open, and is able to resolve hostnames as well as auto-detect your local and external IP range. SoftPerfect Network Scanner offers flexible filtering and display options, and can export the NetScan results to a variety of formats, from XML to JSON. In addition, it supports remote shutdown and Wake-On-LAN.
SoftPerfect Network Scanner
Network Performance Monitor (https://www.solarwinds.com)
OpUtils (https://www.manageengine.com)
PRTG Network Monitor (https://www.paessler.com)
Engineer’s Toolset (https://www.solarwinds.com)
Task 3: Perform SNMP Enumeration using SnmpWalk
SnmpWalk is a command line tool that scans numerous SNMP nodes instantly and identifies a set of variables that are available for accessing the target network. It is issued to the root node so that the information from all the sub nodes such as routers and switches can be fetched.
snmpwalk
–v: specifies the SNMP version number (1 or 2c or 3)
–c: sets a community string.
Task 4: Perform SNMP Enumeration using Nmap
The Nmap snmp script is used against an SNMP remote server to retrieve information related to the hosted SNMP services.
--script=snmp-sysdescr
--script=snmp-processes
--script=snmp-win32-software
--script=snmp-interfaces
Lab 3: Perform LDAP Enumeration
Task 1: Perform LDAP Enumeration using Active Directory Explorer (AD Explorer)
Active Directory Explorer (AD Explorer) is an advanced Active Directory (AD) viewer and editor. It can be used to navigate an AD database easily, define favorite locations, view object properties and attributes without having to open dialog boxes, edit permissions, view an object’s schema, and execute sophisticated searches that can be saved and re-executed.
Steps to use the tool:
The Connect to Active Directory pop-up appears; type the IP address of the target in the Connect to field (in this example, we are targeting the Windows Server 2022 machine: 10.10.1.22) and click OK.
The Active Directory Explorer displays the active directory structure in the left pane, as shown in the screenshot.
Now, expand DC=CEH, DC=com, and CN=Users by clicking “+” to explore domain user details.
Right-click any attribute in the right pane (in this case, displayName) and click Modify… from the context menu to modify the user’s profile.
The Modify Attribute window appears. First, select the username under the Value section, and then click the Modify… button. The Edit Value pop-up appears. Rename the username in the Value data field and click OK to save the changes.
Softerra LDAP Administrator (https://www.ldapadministrator.com)
LDAP Admin Tool (https://www.ldapsoft.com)
LDAP Account Manager (https://www.ldap-account-manager.org)
LDAP Search (https://securityxploded.com)
Task 2: Perform LDAP Enumeration using Python and Nmap
LDAP enumeration can be performed using both manual and automated methods. Using various Python commands LDAP enumeration is performed on the target host to obtain information such as domains, naming context, directory objects, etc. Using NSE script can be used to perform queries to brute force LDAP authentication using the built-in username and password lists.
Nmap Commands for LDAP Enumeration
-sU: performs a UDP scan
-p: specifies the port to be scanned.
cn(Common Name): This attribute represents the common name of the entry.dc(Domain Component): This attribute represents a domain component of the LDAP directory. Eachdccomponent represents a part of the domain name.
-p: specifies the port to be scanned,
ldap-brute: to perform brute-force LDAP authentication.
ldap.base: if set, the script will use it as a base for the password guessing attempts.
Python Commands for LDAP Enumeration
Now, connect to the target LDAP server without credentials using python.
If we will receive response as True that means the connection is established successfully.
To gather information about naming context or domain name, as shown in the screenshot below.
The command performs an LDAP search starting from the CEH.com domain, looking for all objects and retrieving all their attributes from the entire subtree of the specified base DN.
run connection.entries To retrieve all the directory objects.
The command performs an LDAP search starting from the CEH.com domain, looking for all entries of the person object class, and retrieving only the userpassword attribute for each of these entries. This command is essentially searching for user password information for all user entries within the specified domain and its subtree.
run connection.entries To retrieve all the directory objects.
Task 3: Perform LDAP Enumeration using ldapsearch
ldapsearch is a shell-accessible interface to the ldap_search_ext(3) library call. ldapsearch opens a connection to an LDAP server, binds the connection, and performs a search using the specified parameters. The filter should conform to the string representation for search filters as defined in RFC 4515. If not provided, the default filter, (objectClass=*), is used.
-x: specifies simple authentication, -h: specifies the host, and -s: specifies the scope.
to gather details related to the naming contexts.
-x: specifies simple authentication, -h: specifies the host, and -b: specifies the base DN for search.
to obtain more information about the primary domain.
to retrieve information related to all the objects in the directory tree.
Lab 4: Perform NFS Enumeration
Overview of NFS Enumeration
NFS (Network File System) is a type of file system that enables computer users to access, view, store, and update files over a remote server. This remote data can be accessed by the client computer in the same way that it is accessed on the local system.
Task 1: Perform NFS Enumeration using RPCScan and SuperEnum
RPCScan communicates with RPC (remote procedure call) services and checks misconfigurations on NFS shares. It lists RPC services, mountpoints,and directories accessible via NFS. It can also recursively list NFS shares. SuperEnum includes a script that performs a basic enumeration of any open port, including the NFS port (2049).
SuperEnum Tool
Type ./superenum and press Enter. Under Enter IP List filename with path, type Target.txt, and press Enter.
The script starts scanning the target IP address for open NFS and other. The scan will take approximately 15-20 mins to complete.
RPCScan Tool
--rpc: lists the RPC (portmapper)
Lab 5: Perform DNS Enumeration
Overview of DNS Enumeration
DNS enumeration techniques are used to obtain information about the DNS servers and network infrastructure of the target organization. DNS enumeration can be performed using the following techniques:
Zone transfer
DNS cache snooping
DNSSEC zone walking
Task 1: Perform DNS Enumeration using Zone Transfer
DNS zone transfer is the process of transferring a copy of the DNS zone file from the primary DNS server to a secondary DNS server. In most cases, the DNS server maintains a spare or secondary server for redundancy, which holds all information stored in the main server.
If the DNS transfer setting is enabled on the target DNS server, it will give DNS information; if not, it will return an error saying it has failed or refuses the zone transfer.
On Linux-based systems, the dig command is used to query the DNS name servers to retrieve information about target host addresses, name servers, mail exchanges, etc.
In this command, axfr retrieves zone information.\
Now, we will perform DNS enumeration on Windows DNS servers.
Open the Command Prompt window appears; type
nslookup, and press Enter.In the nslookup interactive mode, type
set querytype=soa, and press Enter.
set querytype=soa sets the query type to SOA (Start of Authority) record to retrieve administrative information about the DNS zone of the target domain certifiedhacker.com.
In the nslookup interactive mode, type
ls -d [Name Server]and press Enter, as shown in the screenshot.
In this command, ls -d requests a zone transfer of the specified name server.
After retrieving DNS name server information, the attacker can use one of the servers to test whether the target DNS allows zone transfers or not. In this case, the zone transfer was refused for the target domain. A penetration tester should attempt DNS zone transfers on different domains of the target organization.
Task 2: Perform DNS Enumeration using DNSSEC Zone Walking
DNSSEC zone walking is a DNS enumeration technique that is used to obtain the internal records of the target DNS server if the DNS zone is not properly configured. The enumerated zone information can assist you in building a host network map.
There are various DNSSEC zone walking tools that can be used to enumerate the target domain’s DNS record files.
In this command, -d specifies the target domain and -z specifies that the DNSSEC zone walk be performed with standard enumeration.
The result appears, displaying the enumerated DNS records for the target domain. In this case, DNS record file A is enumerated, as shown in the screenshot.
Using the DNSRecon tool, the attacker can enumerate general DNS records for a given domain (MX, SOA, NS, A, AAAA, SPF, and TXT). These DNS records contain digital signatures based on public-key cryptography to strengthen authentication in DNS.
You can also use other DNSSEC zone enumerators such as
LDNS (https://www.nlnetlabs.nl),
nsec3map (https://github.com),
nsec3walker (https://dnscurve.org),
DNSwalk (https://github.com) to perform DNS enumeration on the target domain.
Task 3: Perform DNS Enumeration using Nmap
Nmap can be used for scanning domains and obtaining a list of subdomains, records, IP addresses, and other valuable information from the target host.
The result appears displaying a list of all the available DNS services on the target host along with their associated ports.
The result appears displaying various common service (SRV) records for a given domain name.
Lab 6: Perform SMTP Enumeration
Overview of SMTP Enumeration
The Simple Mail Transfer Protocol (SMTP) is an internet standard based communication protocol for electronic mail transmission. Mail systems commonly use SMTP with POP3 and IMAP, which enable users to save messages in the server mailbox and download them from the server when necessary. SMTP uses mail exchange (MX) servers to direct mail via DNS. It runs on TCP port 25, 2525, or 587.
Task 1: Perform SMTP Enumeration using Nmap
The Nmap scripting engine can be used to enumerate the SMTP service running on the target system, to obtain information about all the user accounts on the SMTP server.
-p: specifies the port
--script: argument is used to run a given script (here, the script is smtp-enum-users).
Lab 7: Perform RPC, SMB, and FTP Enumeration
Overview of Other Enumeration Techniques
Besides the methods of enumeration covered so far (NetBIOS, SNMP, LDAP, NFS, and DNS), various other techniques such as RPC, SMB, and FTP enumeration can be used to extract detailed network information about the target.
RPC Enumeration: Enumerating RPC endpoints enables vulnerable services on these service ports to be identified
SMB Enumeration: Enumerating SMB services enables banner grabbing, which obtains information such as OS details and versions of services running
FTP Enumeration: Enumerating FTP services yields information about port 21 and any running FTP services; this information can be used to launch various attacks such as FTP bounce, FTP brute force, and packet sniffing
Task 1: Perform SMB and RPC Enumeration using NetScanTools Pro
NetScanTools Pro is an integrated collection of Internet information-gathering and network-troubleshooting utilities for network professionals. The utility makes it easy to find IPv4/IPv6 addresses, hostnames, domain names, email addresses, and URLs related to the target system.
NetScanTools Pro tool to perform SMB enumeration.
Steps given in the course content of CEH Course
The NetScanTools Pro main window appears, as shown in the screenshot.
Screenshot In the left pane, under the Manual Tools (all) section, scroll down and click the SMB Scanner option, as shown in the screenshot.
If a dialog box appears explaining the tool, click OK.
Screenshot In the right pane, click the Start SMB Scanner (external App) button.
If the Demo Version Message pop-up appears, click OK. In the Reminder window, click Start the DEMO.
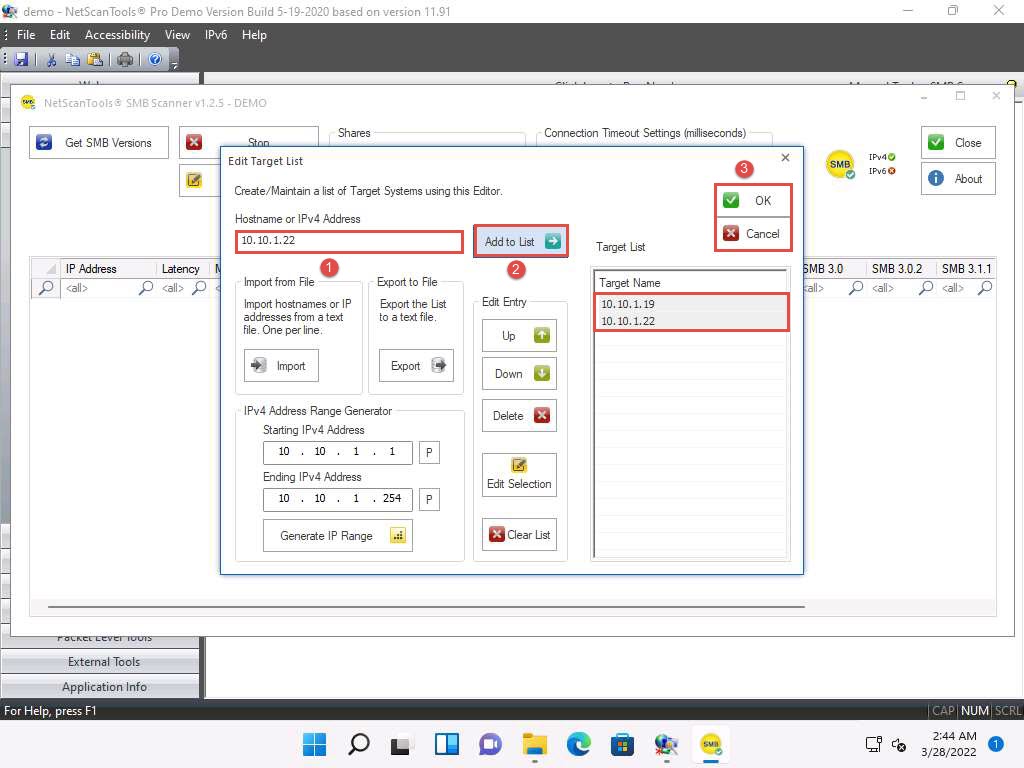
Screenshot The SMB Scanner window appears; click the Edit Target List button.
Screenshot The Edit Target List window appears. In the Hostname or IPv4 Address field, enter the target IP address (10.10.1.19, in this example). Click the Add to List button to add the target IP address to Target List.
Similarly, add another target IP address (10.10.1.22, in this example) to Target List and click OK.
In this task, we are targeting the Windows Server 2019 (10.10.1.19) and Windows Server 2022 (10.10.1.22) machines.
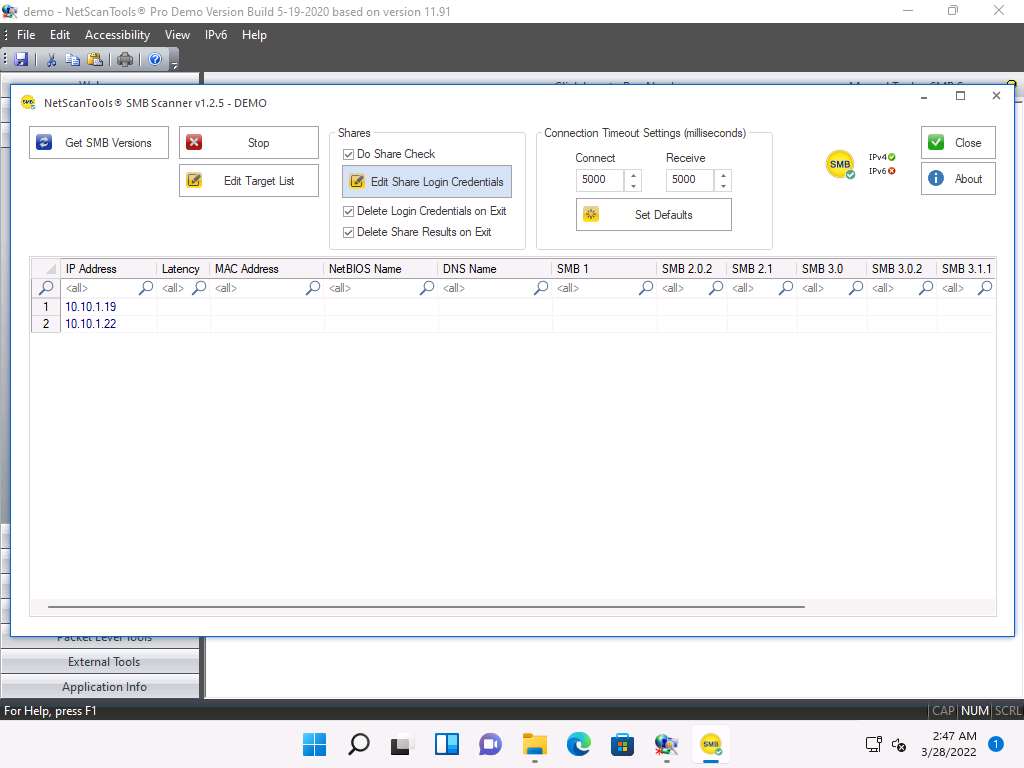
e1v1tklf.jpg Now, click Edit Share Login Credentials to add credentials to access the target systems.
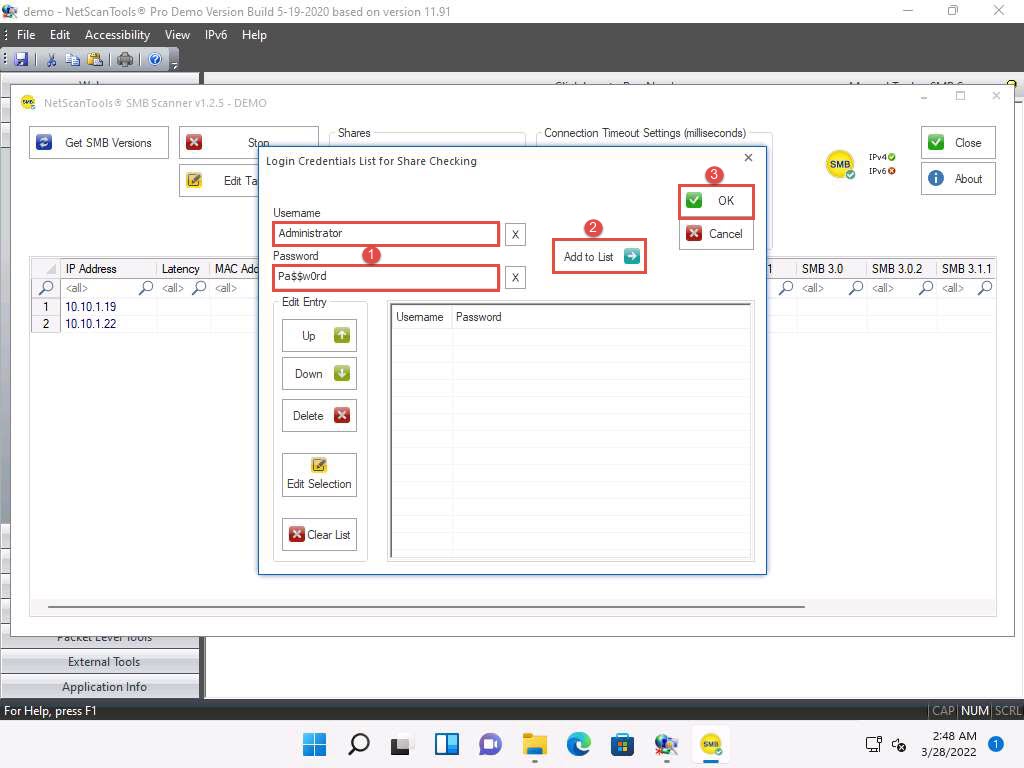
Screenshot The Login Credentials List for Share Checking window appears. Enter Administrator and Pa$$w0rd in the Username and Password fields, respectively. Click Add to List to add the credentials to the list and click OK.
In this task, we are using the login credentials for the Windows Server 2019 and Windows Server 2022 machines to understand the tool. In real-time, attackers may add a list of login credentials by which they can log in to the target machines and obtain the required SMB share information.
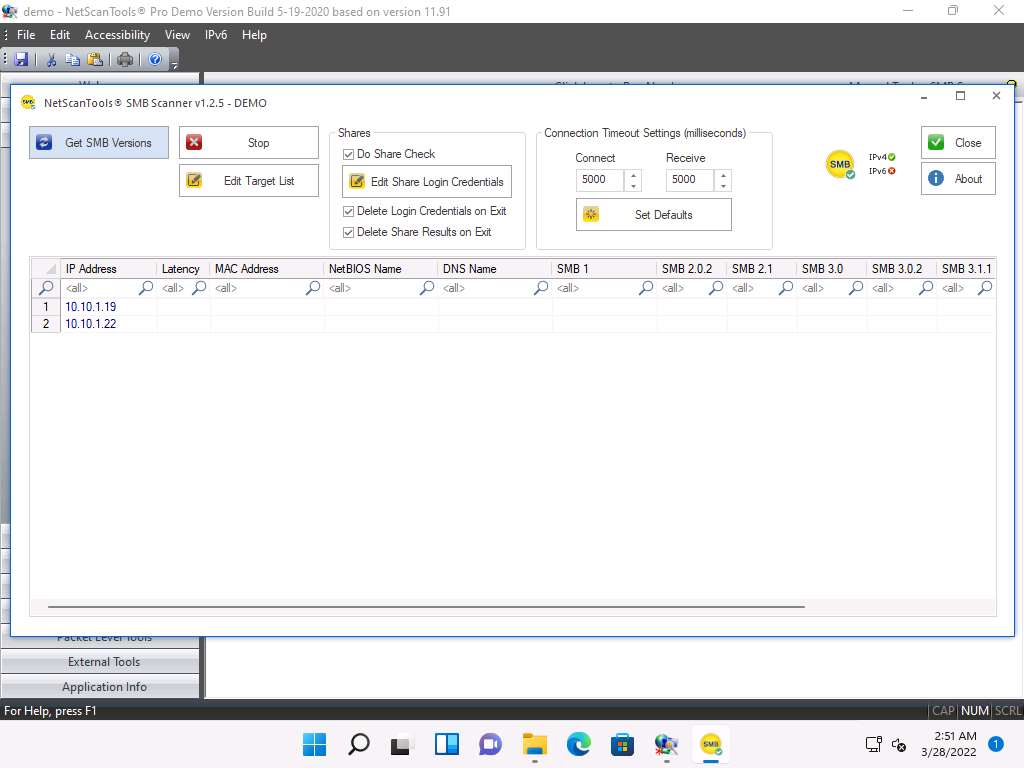
bc54jall.jpg In the SMB Scanner window, click the Get SMB Versions button.
Screenshot Once the scan is complete, the result appears, displaying information such as the NetBIOS Name, DNS Name, SMB versions, and Shares for each target IP address.
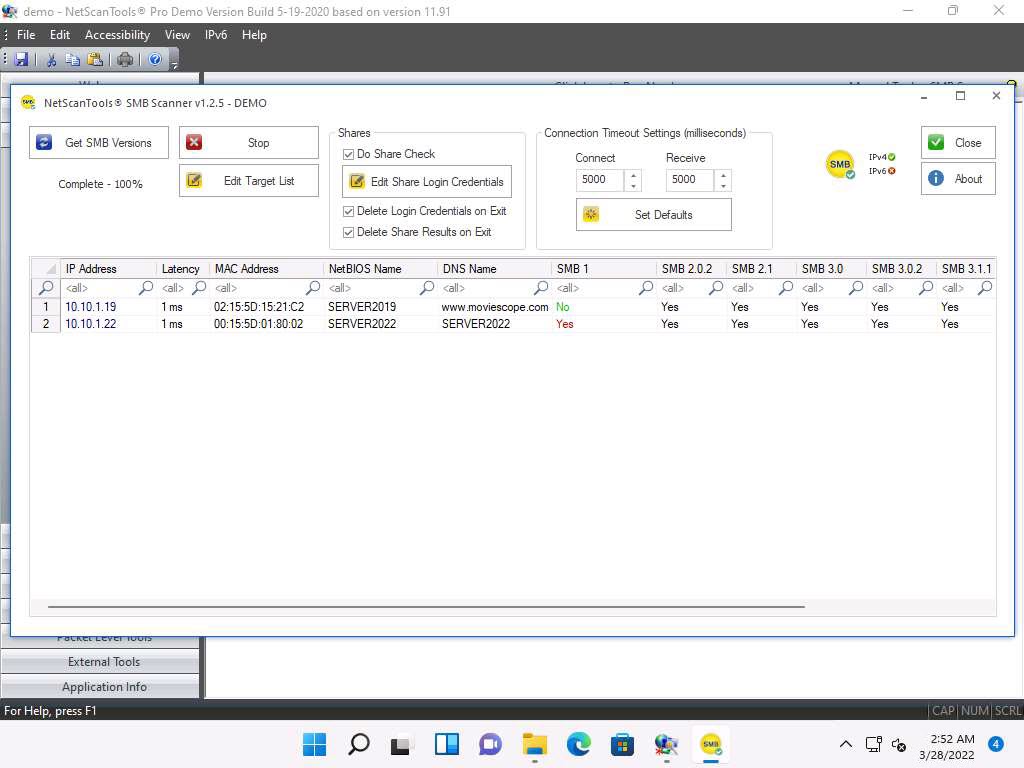
smb%20new.jpg Right-click on any of the machines (in this example, we will use 10.10.1.19) and click View Shares from the available options.
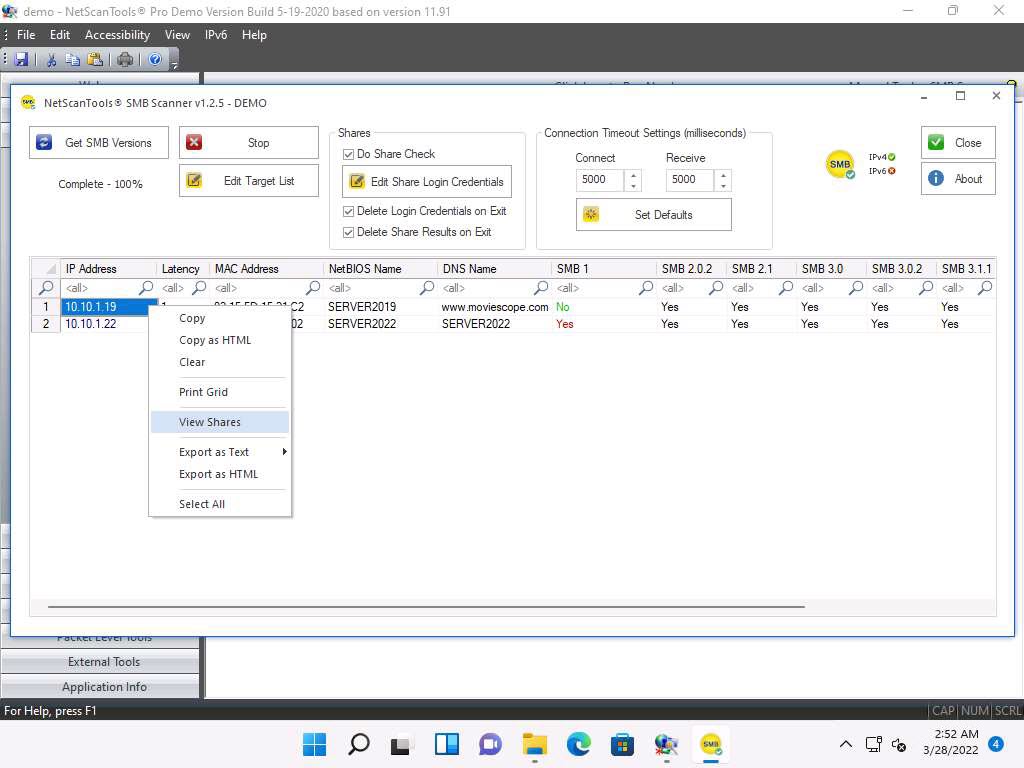
smb2%20new.jpg The Shares for 10.10.1.19 window appears, displaying detailed information about shared files such as Share Name, Type, Remark, Path, Permissions, and Credentials Used. Close the Shares for 10.10.1.19 window.
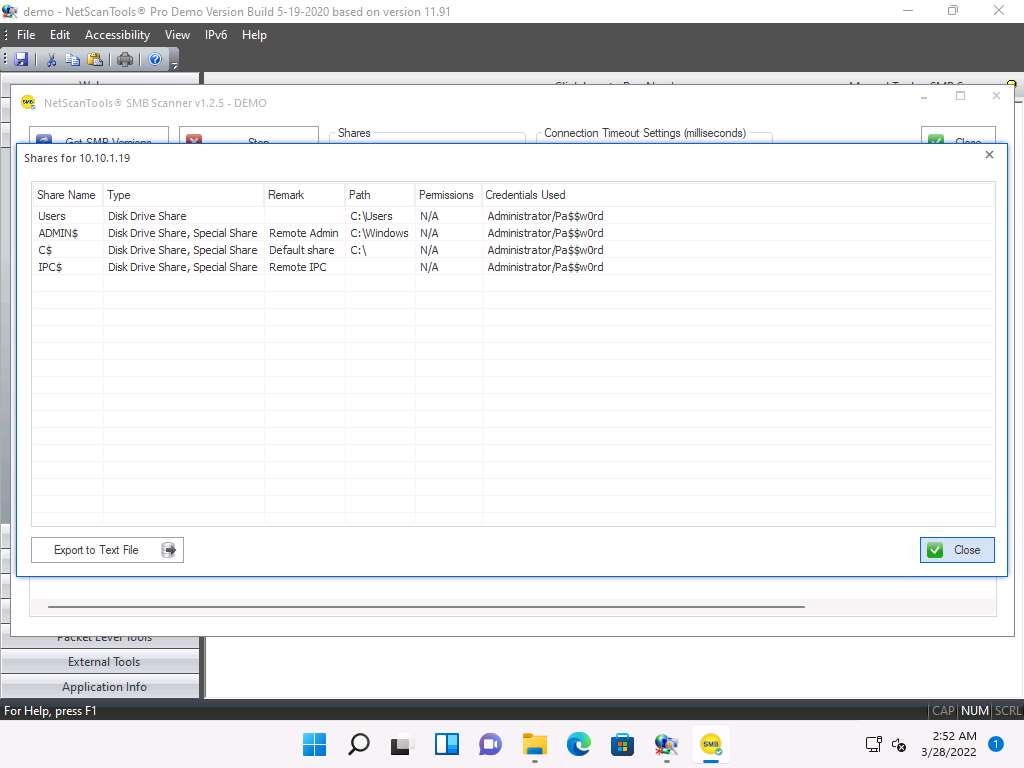
Screenshot By using this information, attackers can perform various attacks such as SMB relay attacks and brute-force attacks on the target system.
You can view the details of the shared files for the target IP address 10.10.1.22 in the same way.
In the left pane, under the Manual Tools (all) section, scroll down and click the *nix RPC Info option, as shown in the screenshot.
If a dialog box appears explaining the tool, click OK.
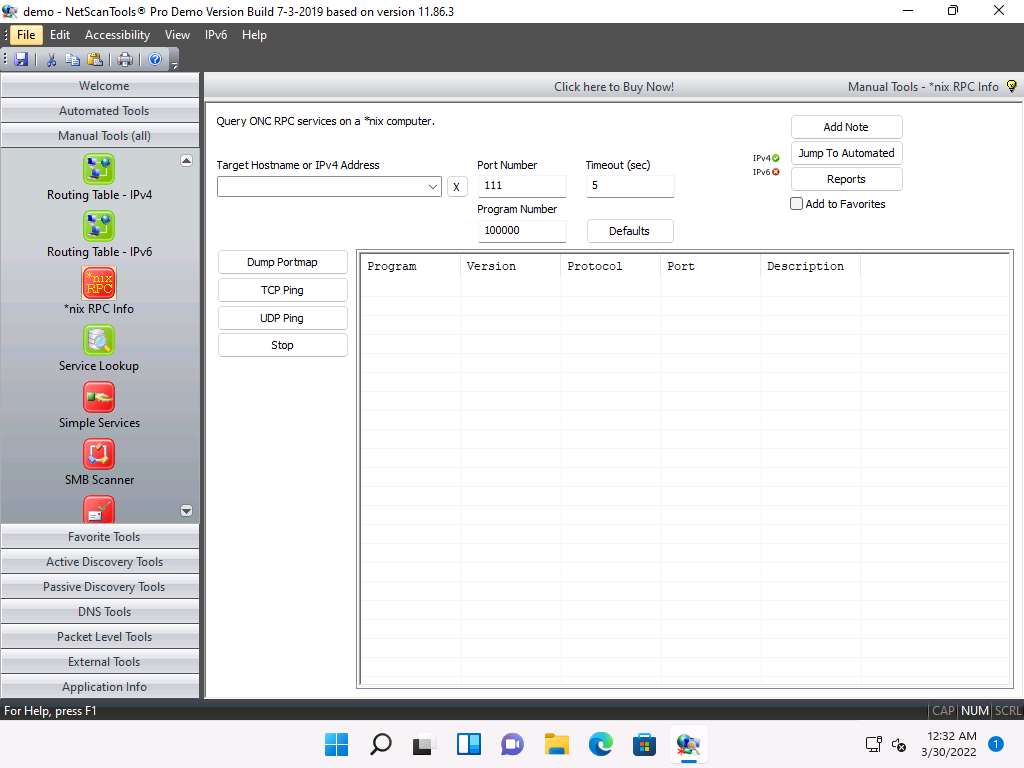
Screenshot In the Target Hostname or IPv4 Address field enter 10.10.1.19 and click Dump Portmap.
Screenshot The result appears displaying the RPC info of the target machine (Windows Server 2019), as shown in the screenshot.
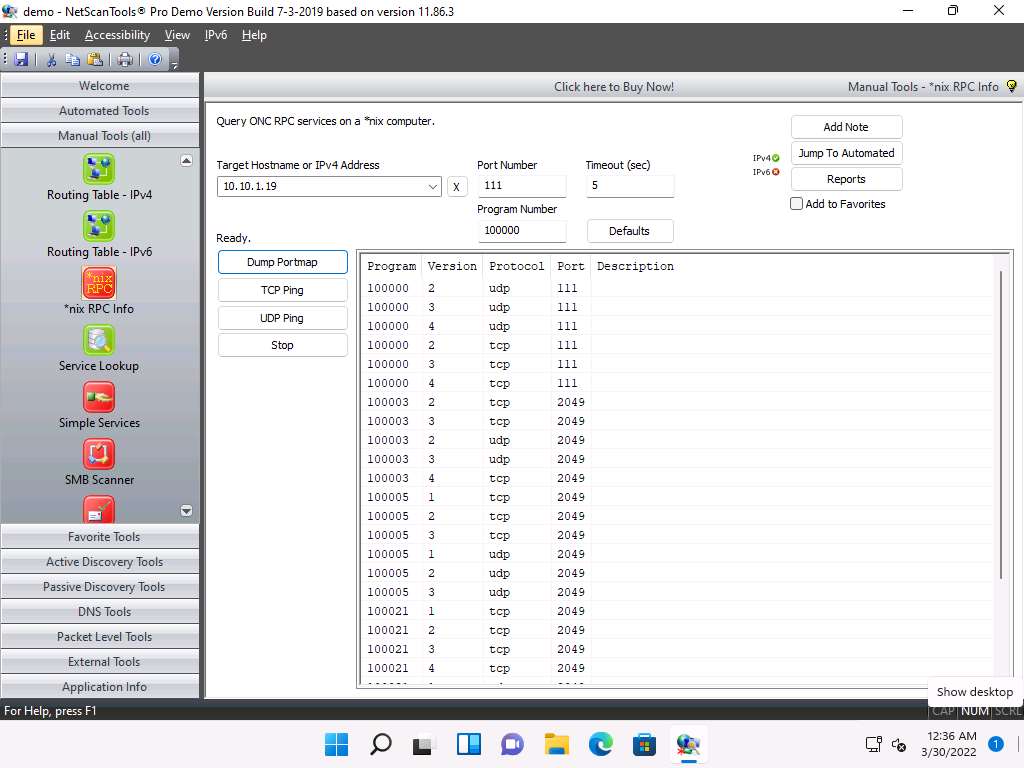
Screenshot Enumerating RPC endpoints enables attackers to identify any vulnerable services on these service ports. In networks protected by firewalls and other security establishments, this portmapper is often filtered. Therefore, attackers scan wide port ranges to identify RPC services that are open to direct attack.
Task 2: Perform RPC, SMB, and FTP Enumeration using Nmap
Nmap is a utility used for network discovery, network administration, and security auditing. It is also used to perform tasks such as network inventory, service upgrade schedule management, and host or service uptime monitoring.
Lab 8: Perform Enumeration using Various Enumeration Tools
Overview of Enumeration Tools
To recap what you have learned so far, enumeration tools are used to collect detailed information about target systems in order to exploit them. The information collected by these enumeration tools includes data on the NetBIOS service, usernames and domain names, shared folders, the network (such as ARP tables, routing tables,traffic, etc.), user accounts, directory services, etc.
Task 1: Enumerate Information using Global Network Inventory
Global Network Inventory Tool
Global Network Inventory is used as an audit scanner in zero deployment and agent-free environments. It scans single or multiple computers by IP range or domain, as defined by the Global Network Inventory host file.
Task 2: Enumerate Network Resources using Advanced IP Scanner
Advanced IP Scanner provides various types of information about the computers on a target network. The program shows all network devices, gives you access to shared folders, provides remote control of computers (via RDP and Radmin), and can even remotely switch computers off.
Task 3: Enumerate Information from Windows and Samba Hosts using Enum4linux
Enum4linux is a tool for enumerating information from Windows and Samba systems. It is used for share enumeration, password policy retrieval, identification of remote OSes, detecting if hosts are in a workgroup or a domain, user listing on hosts, listing group membership information, etc.
Hacker's Mantra:Growth isn’t free, it always has a cost - Morgan Brown